Hello fellow steemians it's the last week of the steemit crypto academy season 3 the assignment by @stream4u is on cryptography.

Let's get started
1. EXPLAIN THE BLOCKCHAIN CRYPTOGRAPHY AND MENTION FEW NAMES WHICH ARE THE BLOCKCHAIN PLATFORM.
What is BLOCKCHAIN cryptography?
Firstly let me define cryptography. Cryptography is the system that secures information through a platform where we can communicate with another user privately without leaking the information to a third party. The cryptography system is built in a way to privatize information between two member or within a group without the information shared reaching out to non member.
Its only the receiver and the sender can see the information passed. There are three types of cryptography namely asymmetric cryptography, symmetric cryptography and hash function. In cryptography information are sent in an encrypted form (transferring readable information in unreadable plain code) then the receiver will use a key to decrypt the information to become readable. Whereas only the receiver can view the message.
BLOCKCHAIN Cryptography
Cryptography in BLOCKCHAIN is the method of ensuring secure transactions carried out between users with the use of private keys, public keys, Hash and digital signature to validate the transaction.
Every users are given a private key and a public key. The private key remains private it's not to be shared. But the public key is known. The private keys are used to validate or sign transactions. And our wallet address are generated from the public key with the help of the Hash function.
Anything involving transactions or messages send from form one user to another on the blockchain we use the public key to validate this things it serves as a signature of approval.
Blockchain Platform
There are lot of blockchain platform. Below are few blockchain platforms.
- Ethereum
- Quorum
- Stellar
- Tron
2. Explain The Public key Cryptography
The public key is a key generated by the asymmetric cryptography algorithm. It is an alphanumeric key/hash generated for identification. It can be used to verify transactions in the blockchain. And as we all know from the name the key is public. It's always available so there is no way we can lose this key. It is generated in form of hash whenever a transaction is made.
The public key is used for encryption of information between the sender and the receiver. It can be used by any member for the encryption of data sent or received. Every public key is assigned to a private key but it's can't be used to retrieve the private key.
3. Explain The Private Cryptography
Private key is a secret key assigned to every user. It is used to encrypt information/data. This key remains private because it the only key used to login into our wallet to access our funds and it can be used to sign transactions. Then we use digital signature with the public key to validate the transaction.
We can use the private key to generate new public key but the public key can't be used to retrieve new private key
When we create wallet we get a unique alphanumeric keys which serves as our private key and we are to save this key secretly
4. Explain The Digital Signatures Cryptography And What is Signing Transaction/Message?
This is the creation of digital codes for verifying if a message is real/legit. This is also same in cryptography it proves the sender of the transaction is the holder is the owner of the account or wallet.
The digital signature is created with the Private key when the a transaction is initiated. This signature can't be forged because it's created when a transaction is initiated so without the owner signing the transaction with the signature he got the transaction won't be validated.
Signing of Transaction
Signing a transaction is subdivided into two sign and verification. For a transaction to be validated, the digital signature for the transaction has to be verified. A transaction is signed with the private key then we get a signature in the process.
When the message is sent then we need to verify it before the message will be validated. The digital signature and the public key are used for verifying.
5. Explain What Is Symmetric And Asymmetric Cryptography?
Symmetric Cryptography
In a Symmetric system only one key is used to encrypt and decrypt messages sent this key is shared between the sender and the receiver of the data. This key is also a secret key. This system is very fast because it only requires one key for encryption and decryption.
Asymmetric Cryptography
This is different from the Symmetric cryptography because it uses two different keys to encrypt and decrypt messages sent. It just the same with what I have been explaining before, the keys are the public key and the private key. A good example is the Ethereum blockchain. The advantage that the Asymmetric cryptography has over the Symmetric cryptography is that it is more secure because it requires some process to encrypt and decrypt messages.
6. How Blockchain Wallet Cryptography Works And Explain The Available Types of Crypto Wallets.
Blockchain wallet like the name implies, is a place where funds are stored in a blockchain. We know blockchain has many features in which wallet is one of them. This is an online wallet where funds are stored in a blockchain. Every wallet has address for receiving the crypto. This address is just like an account number to every bank account.
Blockchain Wallet cryptography is all about ciphering a transaction between wallet addresses to make sure that there is no interference of a third party. It is done in a what that only the receiver and the sender have access to the transaction. The transactions are always transparent in a blockchain but the cryptography makes the transaction secured.
Types of Crypto wallet
There are two main types of wallet namely Hot wallet and cold wallet
Hot wallet
This is a digital wallet for online trades and exchanges of Crypto currency. It enable users to store their asset on a digital wallet. It has both private and public keys for validating transactions and for security purpose. Examples of hot wallets are binance exchange, trust wallet, blockchain wallet.
Cold wallet
This types of wallet saves users private and public keys offline. It works with a software complicated computer. This type of wallet stored all data offline. Asset are stored offline example of cold wallet are hardware wallet, terzor wallet and paper wallet. This wallet are not connected to the internet.
7. What Is The Merkle Trees And What It's Importance In The Blockchain
Merkle trees will always end with a string of data known as the Merkle Root. The Merkle tree is a way data are structured allowing the data to be verified for Efficiency and accuracy. Before transaction are stored, it needs to be verified the Merkle tree collects all the hash of transaction carried out at the time to generate a unique datta that will cover all different transaction. Then all the data will be stored in a block header.
Merkle tree used to increase the speed of verifying data. In cryptography, a Merkle tree is a tree whose branches are cryptographic hash of the data. The Merkle tree consist of nodes, collection of transactions and the root hash.
In the Merkel tree, hash are paired with another hash it's continue pairing then it forms a tree like structured consisting of data from the blockchain. There is always a root hash which carries every other hashes
Since every new hash contains data of the previous hash it become easy for the Merkle tree to reduces all the data in all previous hashes into a single hash then validates the data this way the validation becomes more efficient.
Importance of Merkle tree
- It is used for faster verification. It's make the verification of data fast, efficient and accurate.
- It solves one of the blockchain problem which is the 51% attack.
- It reduces memory usage of the nodes
- The Merkle tree validated transaction and also prove the integrity of the data.
8. Particle + Theory, Do Some Practical Research , Study on Blockchain. Demo: Public / Private key & Signing And Then Explain The Functionality of Keys, Signature, Transaction, Blockchain With Proper Screenshots of Your Practical.
Key
This part shows the private keys and the public keys. Below is the screenshot for the keys.
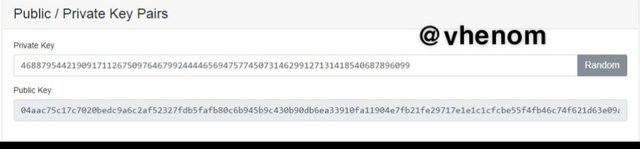
Incase you edited the private key you will always get a new public key. You can always generate new private keys for both public and private when you click on random
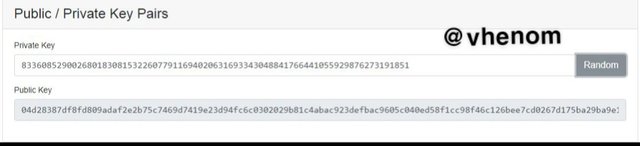
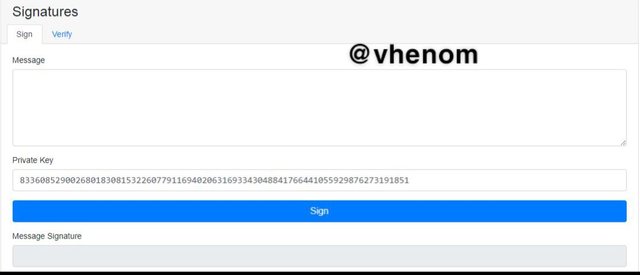
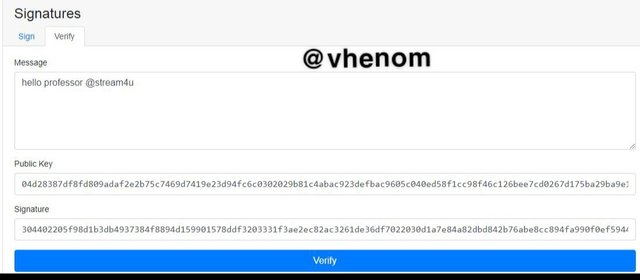
Signatures
Signature are used to sign the transaction and for every transaction we get a signature.
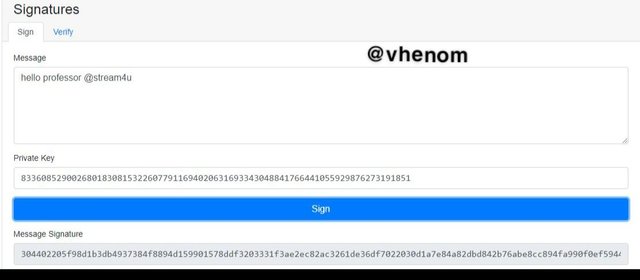
Then input a message. After inputting the message I got a signature for verifying the message .
Then I clicked on verify as you can see the message has been signed.
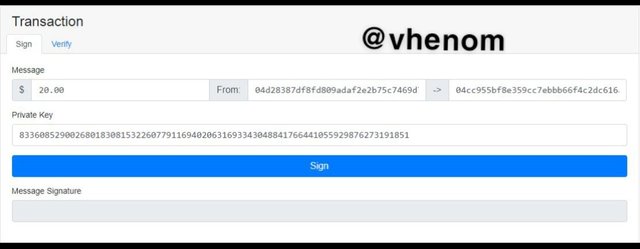
Transaction
I clicked on the transaction as you can see below is a screenshot showing a transaction. Then I clicked on sign.
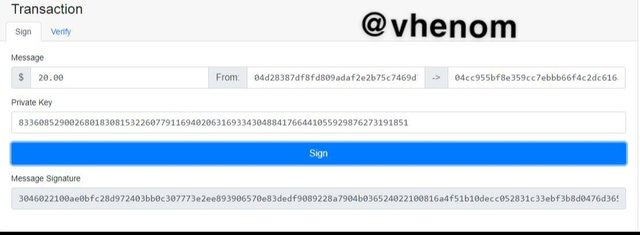
Then clicked on sign. After Signing I got another signature.
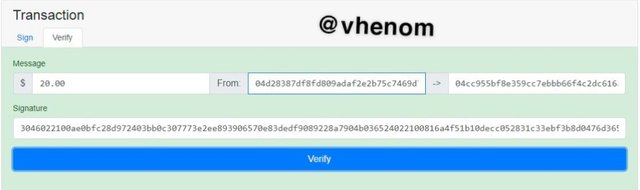
Then I proceed to verify the transaction. With the signature, the transaction become verify.
Blockchain
This is the block consisting of data of transactions and hash and signatures. Each block consists of previous hash information.
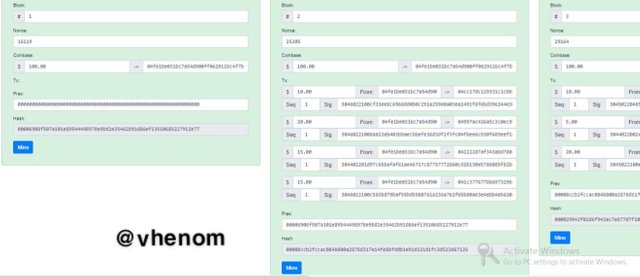
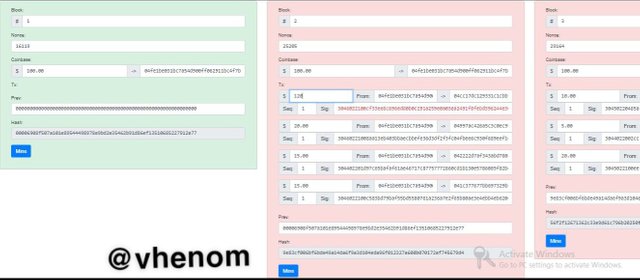
Here I try to change the information in the transaction. This changed the data in all other blocks make them invalid. So I have to re-mine every other blocks in the chain so as to make the transaction validated
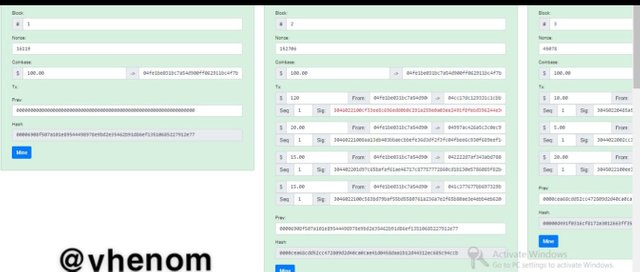
Here I have re-mined the blocks and the data are verified again. All the data in the affected block has be changed an reverified
Conclusion
Cryptography is the system that secures information through a platform where we can communicate with another user privately without leaking the information to a third party.
The cryptography system is built in a way to privatize information between two member or within a group without the information shared reaching out to non member