Hello Friends!
Thanks to professor @gbenga for this week's lesson on Blockchain security. It is important to know how to keep our wallet and network secured. There is so much I learned from this lesson and now I'm aware of these security concerns.
If there is anyone who missed this week's lesson here is the link - The Steemit Crypto Academy Week 5: All About Blockchain Security
This weeks homework task:
Make a Post about a Security problem with Cryptocurrency and Share a personal experience if possible.
What is Dusting Attack?
As you may aware, cryptocurrencies are decentralized blockchain where anybody can set up a wallet without providing any personal details. Bitcoin transactions aren't completely anonymous, it is considered as pseudonymous transactions. It records all transactions in a public ledger making it visible for anyone to see.
This somewhat reduces privacy and cybercriminals could take advantage of it.
A dusting attack is a strategy used by hackers or scammers to identify the user or a business entity behind the wallet. By sending a small number of tokens or coins known as "Dust", to a large number of wallets. The purpose of attackers is to trace the account details or to de-anonymizing by performing a combined analysis of different addresses to reveal the user behind the wallet.


source
Most cyber criminals use this method very often to attack large crypto holders. There is a reason for it, that is most of the large crypto holders won't recognize these tiny amounts of tokens or coins in their wallets.
If the wallet owner moves this dust (digital currency) the attackers are able to trace the transaction as it is linked to other dusted addresses and reveal the true identity. If the attackers are successful these large funds holders can be targeted in many ways. Such as phishing scams and cyber-extortion. When the criminals identify the true identity they can steal your wallet easily by sending a phishing E-mail that looks like a real e-mail. If you click on a link on the E-mail unknowingly, you will end up being a victim of a dusting attack.
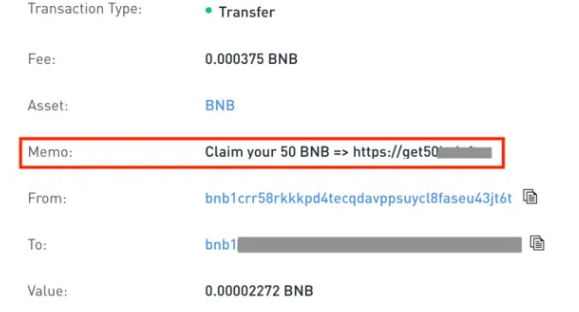
Example of a Binance chain dusting attackTo stay protected, the large fund holders should not move dust that is sent out to them. Without moving the dust, the attackers are unable to trace the transaction to find out the link to the true owner. Unless you don't move the tiny bit of cryptocurrency, there is nothing to be worried about. Sending dust will not give control of your funds to cybercriminals.
Is It possible to avoid Dusting Attacks?
Yes! To prevent such crypto attacks, the large fund holders are able to store their assets safely in a hardware wallet. Hardware wallets will provide maximum security by creating new addresses each time you make a transaction. It will make tracing transactions much harder. Using hardware wallets will ensure your assets are protected from dust attacks by showing dusty UTXOs (unspent transaction outputs), You can also mark these dust as "do not spend".
Am I a victim of Cyber Attacks?
No. Since I'm still a starter in the crypto journey I haven't experienced any security issues. Currently, I have stored all my keys safely. Someday, if I become a whale or somebody who owns a large number of crypto funds. I'll make sure that I use an HD wallet to keep my assets safely under my own ownership.
Thanks to professor @gbenga for the wonderful lesson. Looking forward to next week's lesson.
Thanks for reading!
Mentioning respected @steemcurator01 & @steemcurator02
#cryptoacademy #gbenga-week5 #srilanka #steemexclusive #steemitblog

Dusting Attack is easier on large stakeholders compared to people with little or no currency in their wallet.
Question: How can a person who has been attacked solve the problem of dusting attack?
rating 4
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi prof @gbenga
Thanks for the verification.
There is no way of recovering the assets which have been stolen. The person has to take necessary security actions to protect the assets in the future. A dusting attack is like a gift that you don't want. if these tokens are kept unspent, the person will not be facing any dusting attack. I have answered your question as per my understanding. Correct me if I'm wrong.
Thank you!
Have a great day...
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit