Hello all.....
Today I will try to join professor @pelon53 class on hash and cryptography. This is a very interesting class. ok i will try to solve some questions from homework this week.
Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Resistance to Collision
Resistance to Collision is a hash function that anticipates a collision against 2 different inputs leading to the same output. so the hash function will anticipate the occurrence of the same output from 2 different inputs. Resistance to Collision plays an important role in the security level of the hash.
although the length of the input characters is different, the output has the same hash length in the form of an alphanumeric code that is given randomly, making it difficult for hackers to find out which input has been processed. With the Resistance to Collision function, it is almost impossible for a collision between inputs to occur. because if the inputs have the same hash then this can cause data loss as well as hacking can occur.
Resistance to Preimage
Resistance to Preimage is one of the hash functions that can be said to make it difficult for hackers to find input from output (hash). so if you have done the input and output has been generated in the form of a hash. then it is quite difficult to decode the hash to find the previous input, and arguably almost impossible. There are two types of resistance to preimage, namely Preimage resistance and Second preimage resistance.
- Preimage resistance
preimage resistance has a function to protect user data from hackers by making it difficult for hackers to find input from a very unique hash code.
- Second preimage resistance
Second preimage resistance has the function of anticipating hackers who find two different inputs when colliding into the same output, this is all if a collision is possible.
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking
Tronscan
- first, visit the web https://tronscan.org/#/. and you can see the main page as shown below dibawah
- after that select last block to view the information.
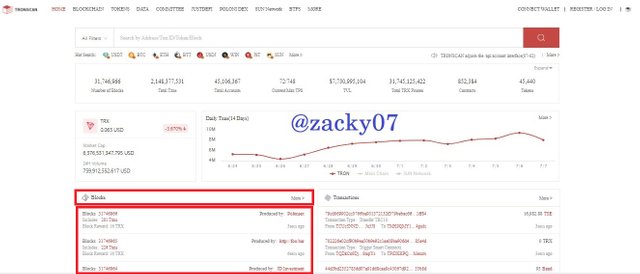
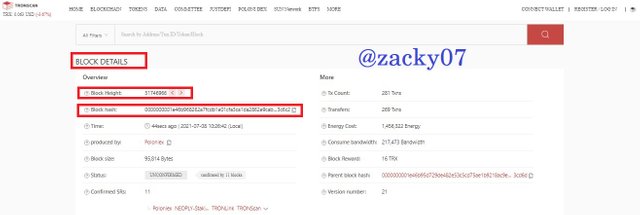
- after that you can find detailed block information, such as :
Block height : 31746966
Block hash : 0000000001e46b968262a7fcdb1e01cfa3ca1da2862e9cab0f5f6d52d793c6c2
- To view transaction information, return to the main page and select the last transaction.
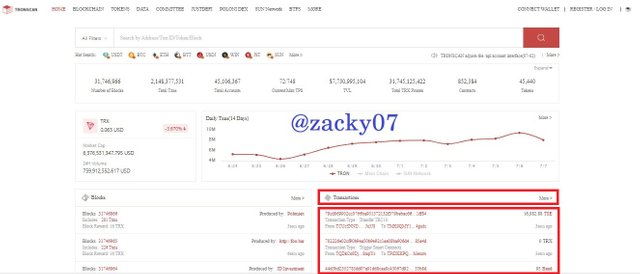
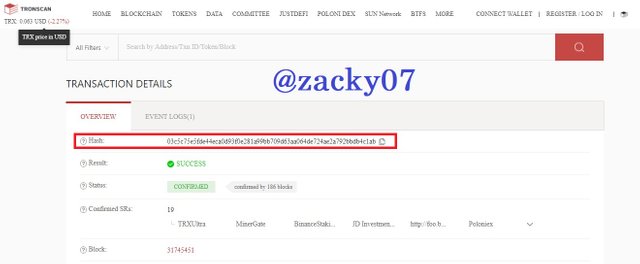
- on that page you can see detailed transaction information. as :
Hash : 03c5c75e5fde44eca0d93f0e281a99bb709d63aa064de724ae2a792bbdb4c1ab
Etherscan
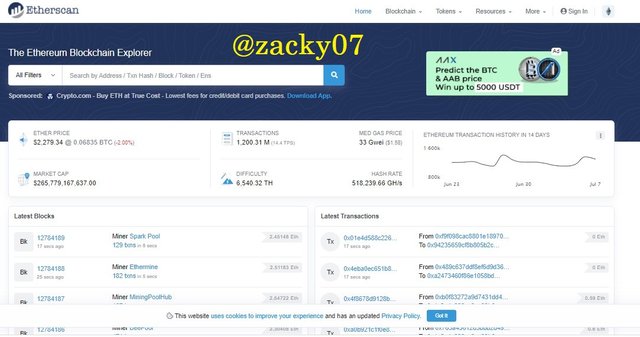
- first visit the webpage https://etherscan.io/. then you can see the main page as below
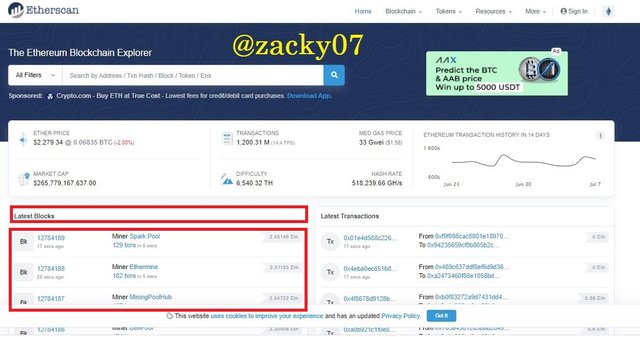
- after that select last block to view the information.
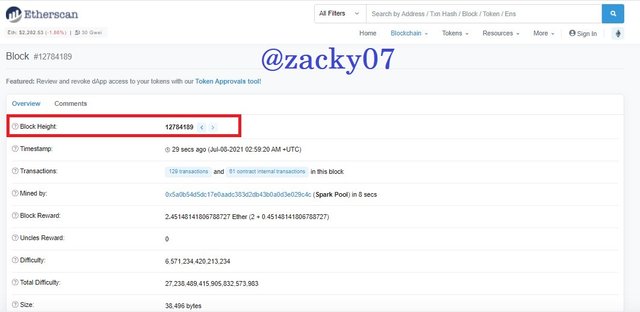
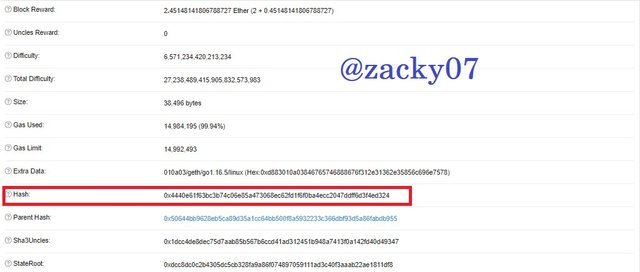
- after that you can find detailed block information, such as :
Block height : 12784189
- Then scroll down to see hash information:
Hash : 0x50644bb9628eb5ca89d35a1cc64bb500f8a5932233c366dbf93d5a86fabdb955
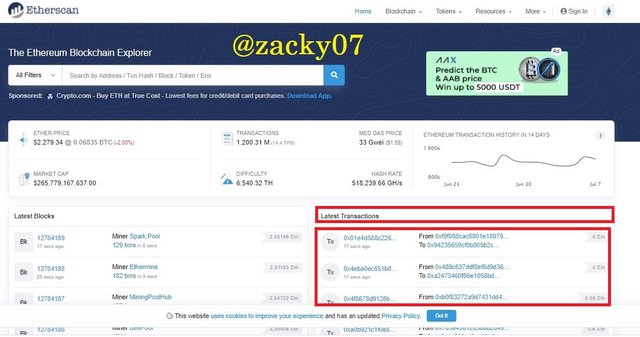
- To view transaction information, return to the main page and select the last transaction.
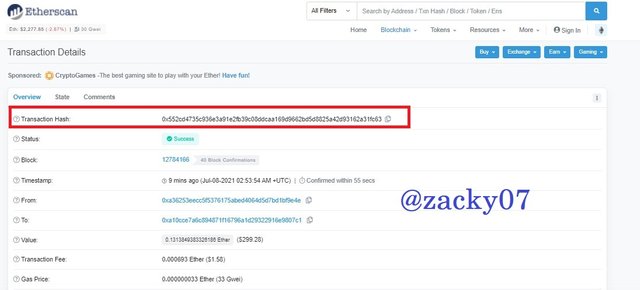
- on that page you can see detailed transaction information. as :
Transaction Hash : 0x552cd4735c936e3a91e2fb39c08ddcaa169d9662bd5d8825a42d93162a31fc63
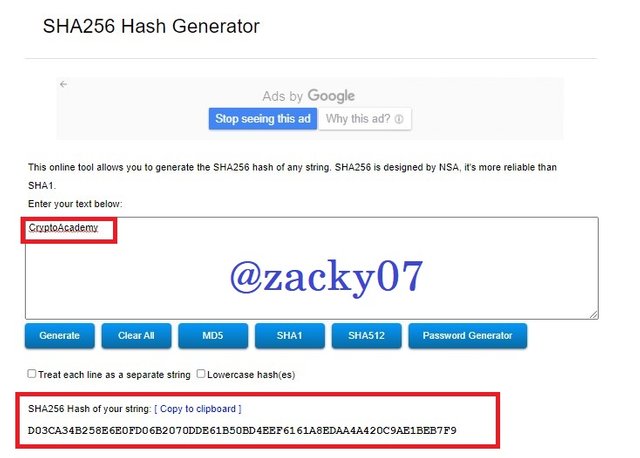
Generate the hash using SHA-256, from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain
- First visit the SHA-256 web: https://passwordsgenerator.net/sha256-hash-generator/. then try entering "CryptoAcademy". it will generate Hash : D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
- then try to enter "cryptoacademy". it will generate Hash : 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
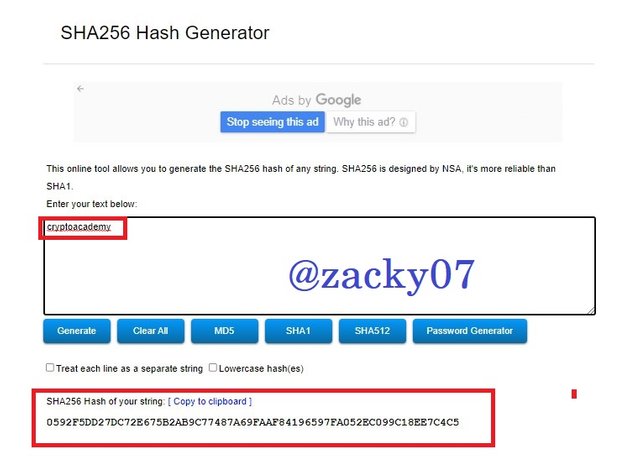
from the above experiment we can conclude that the hash has a different output from each different input even though only the capital letters are different. from the example above I gave the first input, namely "CryptoAcademy" with the letters "C" and "A" contained in the word capitalized. and the second input is "cryptoacademy", although with the same word but produces a different hash due to changes in capital letters. these have all proved that the hash is immutable and remains the same length. so it can be said to have a very good level of security.
Explain the difference between hash and cryptography
hash is an algorithm code that functions for security on the blockchain, with the code provided is quite unique and has a different hash for each input so that it can be said that the hash provides a good level of security and cannot be hacked easily. hash also has the same length even though the length of the input given is different. because the hash system is a unique code so that hackers cannot guess or predict the input from the hash.
Cryptography is a method to provide security to users related to user privacy such as passwords, information and other user data. Cryptography runs on a blockchain network to provide security and convenience for its users. with the cryptographic function can maintain the blockchain network rather than hacker activities, so with the cryptographic function, only the user and the intended party can know the information.
Here are the differences between hash and cryptography which I have summarized in the table below.
| No | Hash | Cryptography |
|---|---|---|
| 1 | Hash requires no password | Cryptography requires password |
| 2 | Hashes are the same length | Cryptography has varying lengths of data |
| 3 | The hash is immutable | Secret information on the blockchain network |
| 4 | unable to predict input from hash | very difficult to find information related to user privacy |
| 5 | providing security by processing input data into hash | providing security when sending data to the intended user |
Conclusion
Hash and cryptography have the same goal of increasing security on blockchain networks. hash is a unique form of code generated from the inputted information, so that by converting the input information into a hash it can secure the information from hackers. while cryptography protects all information on the blockchain so that the users and the intended users know it. with hash and cryptography can provide security and convenience to users who use blockchain.
Thank you for reading my writing, hopefully it can be useful and easy to understand
CC: @pelon53
.jpg)

Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
No pude corroborar que el bloque sea el mismo tanto para su propio hash, como para el de la transacción. Las captures no me lo permitieron por estar borrosas.
Buen trabajo, continúe mejorando.
Recomendaciones:
Cuando las captures de pantalla no se vean bien trate de mostrar los datos relevantes, para poder verificar su tarea.
Calificación: 8.8
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks professor @pelon53 for the advice, it looks like you have wrongly added the total value that should be 8.8
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Saludos, gracias tienes razón. Ya hice la corrección.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit