The fast progress of information technologies has heralded a period of transformation across all sectors. Information technology has come to be effective in every part of our lives as a result of the fundamental changes it has brought about in every industry, leading in the emergence of new crimes. Many states have had to develop legal procedures, as well as update and change their existing legislation, in order to keep up with the rapidly evolving field of informatics.

Source
Our privacy in real life must be respected, just as it is respected in the information we put on digital media, which has become a vital part of our existence. In this digital age, are we aware of the dangers of doxing, which can threaten our ability to maintain our privacy?
According to study, when communicating with others, we pay attention to our instincts, and some of these instincts are influenced by the nonverbal behavior of the other person. It is true that people you like and get along with can become quite dangerous if they have done their homework and know what you like, if they allow you to communicate with them using nonverbal cues, and if they give the impression that communicating with them will benefit you, believe me when I say that you may find yourself a victim! Being able to read the body language and facial emotions of social engineers can help you avoid becoming a victim of their schemes.

Source
In the digital era, attempts to collect information through social engineering techniques can take on a variety of forms. Subliminal tactics are one of the methods of social engineering that can be used. Using subliminal techniques or sending subliminal messages in news, programs, films, serials, digital games, and many other visual or audio broadcasts (such as music and sound files) has been shown to have a negative impact on people's mental and physical development, as well as their social and emotional development. Typical examples of such visual broadcasts include situations involving possible cyberbullying, cyber violence, and sexual content, as well as online harassment.
A hundred percent protection is impossible in cyber security, and humans are the weakest link, according to the latest research. Countermeasures against cyber-attacks on information systems can be rendered ineffective due to a mistake made by a human. It is possible that when people are stressed, their decision-making systems will be impaired, their perceptions will be impaired, they will become distracted, and they will feel under a great deal of strain. They have the potential to lay the groundwork for a cyber attack and make irreversible mistakes as a result of the pressure they are under.
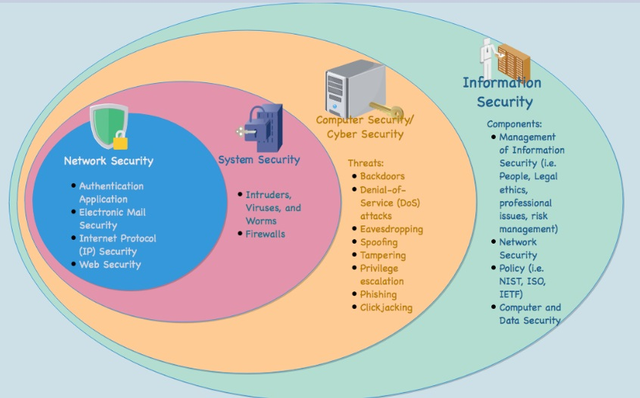
SourceInformation security , cybersecurity and network security
The use of the Internet as a form of communication between persons is becoming increasingly prevalent. It is one of the tactics that enables people from all cultures, social groups, ethnicities, and countries to communicate with large groups of people in a simple and effective manner. Because it is quick and simple, using the internet has a certain allure for many people today. People of all ages, from state officials to celebrities to employees to civil servants to students to teachers to young children to the elderly, have found it to be a convenient medium. In this context, the importance of technology and the use of the internet in terms of increasing information and awareness about certain topics is crucial.
Is it possible for you to make predictions about how crime will change in the future? If we lived in ancient times, theft, fraud, robbery, and extortion would have always been considered bodily crimes. Nonetheless, as we take our first tentative steps into the digital era, it is important to examine the types of crimes that may befall us in the near future.
Every internet user has the option of freely sharing or being compelled to expose more or less personal information on the internet. This is due to the fact that the vast majority of apps ask for permission to access our personal data. We, the users, may be reluctant to provide these permissions, but we are obligated to do so in order to make use of the programs.
Currently, the internet is perceived mainly as a medium for social media, short video, and video games. This is especially true of youthful users. So, what are the factors that have led us to squeeze the internet into such a little amount of space? What happened to bring us to this point? Were we able to determine whether the Internet is a tool that would meet all of our needs? Furthermore, why are the social media platforms that we believe are appropriate for our needs completely free of charge? Where do they get their money from, and how do they manage to afford to buy trucks full of servers every single day? If something is provided for free, are we the product?
Until 15 or 20 years ago, digital games played on phones, laptops, tablets, and the internet mainly supplanted street games played on the streets of cities everywhere.
References:
