Hi, Greetings Dear Engagement Fellows & Community Mentors!!
Today, I am here to speak approximately a topic that is turning into increasingly more crucial in our virtual age – cybersecurity. In modern-day world, we depend heavily on generation for communication, facts, and enjoyment. We use our smartphones, laptops, and different gadgets on a each day foundation without giving an awful lot concept to the capacity risks that come together with them. However, with the rise of cyber threats and attacks, it has grow to be essential for us to train ourselves by way of work of cybersecurity inside the Steem4bloggers Community.
| What is Cybersecurity? Role in Safeguarding Information and Infrastructure? |
|---|

Cybersecurity is the protection of networks and computer structures from theft of or detriment to their tackle, software program software, or information stored in it, in addition to from the dislocation of the services they give. The authorities of every country is taking numerous enterprise to bedeck cybersecurity. With the fast development of information generation, it's far pivotal to offer a safe and secure cyberspace. Cybersecurity is essential due to the fact now not simplest it facilitates to steady information but also our contrivance from contagion attack.

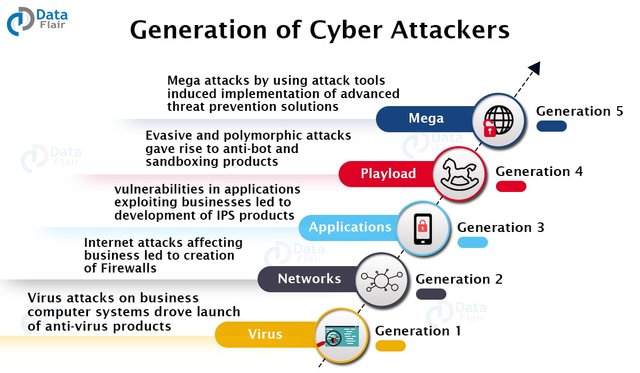
| Different Faces of Cyber Attackers |
|---|


| Importance of Cybersecurity |
|---|
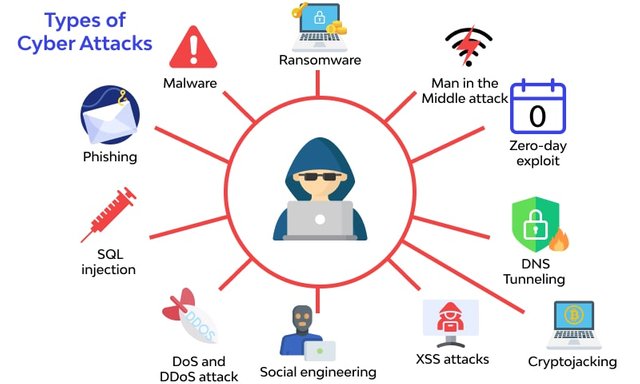
In order to shield ourselves from cyberattacks and to stop detriment to cyberspace, cybersecurity is veritably essential.
Several forms of cyberattacks and cybercrimes that have changed over time are:-

| Conclusion: |
|---|

Cyber attacks also can take control of the carry out different vicious sports. moment due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity pitfalls are veritably dangerous to the country’s security. Not only the government but also the citizens should spread mindfulness among the people to always modernize your system and network security settings and to the use proper anti-virus so that your system and network security settings stay contagion and malware-free.

Goodbye, friends. Thank you for taking your time to read and consider my views on the education of Cybersecurity. Your support and attention mean a lot. Take care & I hope to see you all again very soon , Best of Luck :D .

Upvoted. Thank You for sending some of your rewards to @null. It will make Steem stronger.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit