Cryptography dates back centuries where the early findings of "ciphers" were inscribed on the walls of a tomb of the Old Egyptian Kingdom in 1900BC. The term cryptography came from the Greek words kryptós "hidden" and graphein "to write". There have been various adaptations of cryptographic techniques, but the core principles hold even in the modern-day.
Technologies as recent as blockchain also use cryptographic tools and techniques, which forms its bases. In this article, we will discuss the intricacies of cryptographic techniques, used in Blockchain Technology.
Blockchain is a distributed ledger technology as it preserves and securely transfers data using a decentralised network. To achieve data security, immutability and integrity, we heavily depend on cryptography. Now let's dive in.
The three main pillars of Blockchain Technology, which upholds its unique features of data security and immutability, include:
Hash Functions
Public Key Asymmetric Cryptography
Merkle Trees
Hash Functions
A cryptographic hash is a mathematical function that produces a unique fingerprint of the input data, an alphanumeric having n bits. An n bit length hash has 2^n possibilities hence hash lengths that range 64 and higher are preferred.
Hash is a one-way function, using the input provided we can determine its hash, but vice versa is not possible. No two inputs can have the same fingerprint thus, it is "collision-resistant".
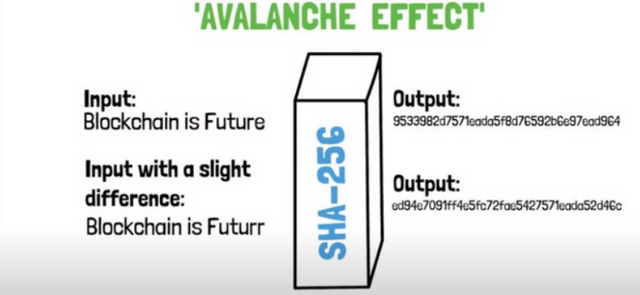
It preserves immutability through the avalanche effect, i.e. a drastic change in the hash if the input is changed even by one character. SHA-256, SHA-3, keccak-256 are a few popular hashing algorithms used in blockchain technology. The figure below describes the avalanche effect.
Public Key Asymmetric Cryptography
Public Key Cryptography is also known as Asymmetric cryptography as it uses two keys, public and private, instead of one as in symmetric cryptography. The principle of Asymmetric cryptography is detailed below:
Every node has two keys, the public key and the private key, simply put public key acts as a user id and the private key acts as a password.
Any plain text encrypted by a public key can only be decrypted using its private key and vice versa.
If any key from the pair is lost, then it is highly improbable to recover the data.
Let's understand it's working using an example, if Alice wants to send a message to Bob, she encrypts the message using Bob's public key and transmits it into the network. As only Bob has access to his private key, no one except Bob can read the message.
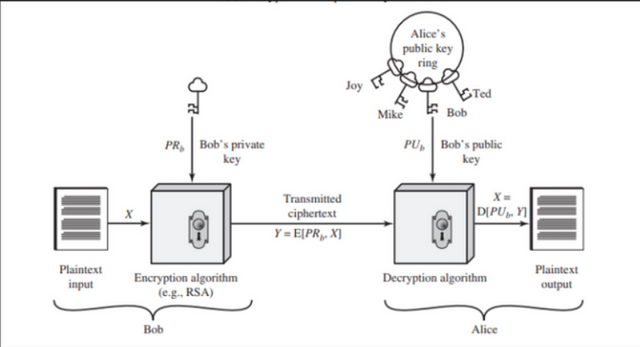
Using this technique transactions in blockchain are processed securely. Crypto-wallets are used to store and transact coins in and around the network and are protected using public-key asymmetric cryptography.
There are many algorithms used in asymmetric cryptography including, RSA, Diffie-Hellman Key Arrangement, ECC etc. RSA algorithm, the oldest of the lot, was developed in the 1970s by three MIT scientists Ron Rivest, Adi Shamir, and Len Adleman. The inventors of RSA published a cipher puzzle in the Mathematical games column of Scientific American in the August 1977 edition which claimed that it would take a million years to break it. They also announced a reward of 100$ in case it is solved.
With the advancement of technology in less than two decades, in April 1994, an internet group claimed the price by decoding the plain text using 1600 computers in 8 months.
Merkle Trees
Merkle trees are an extension of hash functions. If you observe the structure of a block, you can find a Merkle root in the header. As we know, that every transaction in the network is processed and validated after which, the block enters the main-network. Hence, the hash of the block plays a key role.
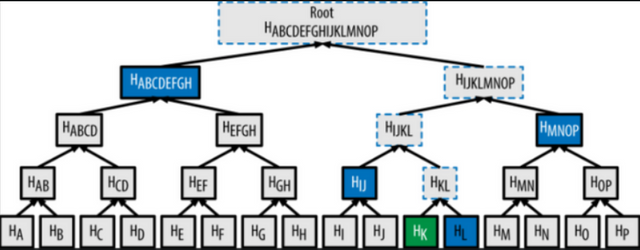
When a block is mined, the miners are trying to find the block hash, whose value is less than the target value. The prerequisites needed while finding the block hash include the hash of the previous block, Merkle root and nonce. Merkle root is one such hash, that is a result of combining all the hashes of the blocks that are present in the network. As the root hash is a confined representation of all the blocks, it is easily detected if an attempt of data tampering occurs.
The future of cryptography is vibrant as it forms the crux of digital currencies like bitcoin and dogecoin. There can be many path-breaking applications of cryptography in the future. But as of today, we can surely concur that as long as covert message exchanges exist, cryptographic tools will play an essential role in the data movement.