dForce's lending protocol, LendfMe, was drained for $25 million in a known smart contract exploit. dForce’s money market arm, LendfMe, was drained of $25 million in a known smart contract exploit. The incident comes less than a week after a $1.5 million raise.
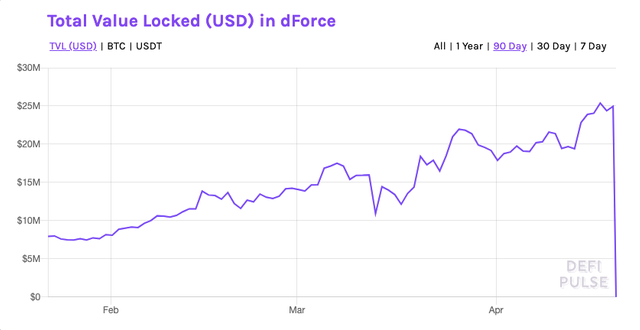
Market Eviscerates LendfMe
DeFi is an emerging niche within crypto, making it difficult for projects to implement vulnerability free code. But these difficulties are dramatically more pronounced when a project doesn’t fully understand the code it has deployed.
Uniswap’s imBTC pool was completely drained yesterday, raising the suspicions of on-chain investigators. The attack was done using a known exploit of ERC-777 tokens.
The vulnerability exploited on LendfMe was highlighted by ConsenSys for DEXes such as Uniswap. With ERC-777 token pools, a malicious entity can make constant contract calls to withdraw funds from the liquidity pool’s smart contract.
As a result, withdrawals are done faster than the balance can be updated, allowing an entity to purchase tokens for a steep discount by causing an imbalance to the liquidity pool. This very exploit was used to drain funds from the infamous Ethereum DAO smart contract in 2016.
Read full article here
