Introduction.

Define Cryptography.
Cryptographic functions are meant to protect sensitive data during transfers or transactions on the blockchain that are almost impossible to break meaning that they cannot be duplicated or altered In any way.
Cryptography Involves encrypting and decrypting of data or transactions between two people or users In the presence of other outsiders who are blinded to the secret information because the do not have the necessary keys to decrypt the message.
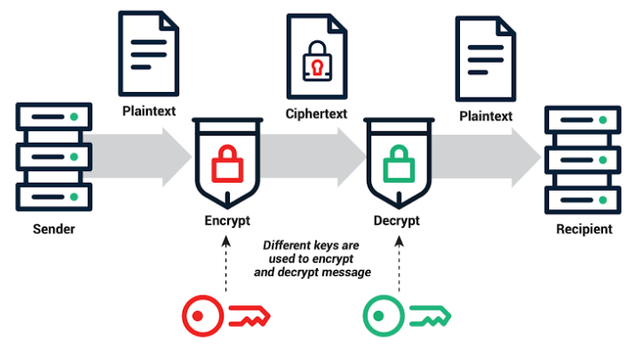
Therefore cryptography is the science of providing security on the blockchain through encryption and decryption of messages or data. Encryption is converting a message into code language that cannot be understood by humans using the private key if it is private key encryption or the public key if it is public key encryption.
Decryption on the other hand means to change the coded message into text or readable words again so that they can be read and understood by a person.

Explain Private-Key Encryption, Public-Key Encryption, and Hash Functions.
Private key encryption works in a way that there is only one key that is used to encrypt and decrypt the data. The sender uses the private key to send the message in code and shares the private key with the recipient who uses it to view the message in it's original form. It is also called Symmetric Encryption.
For example Jane uses a key (Y) to send a message " Come tomorrow" to Joe as a code like #@@27##7@-&-((#-& and Joe uses the same (Y) key to decrypt and view the message in as "Come tomorrow". The outsiders who see it see only the code message.
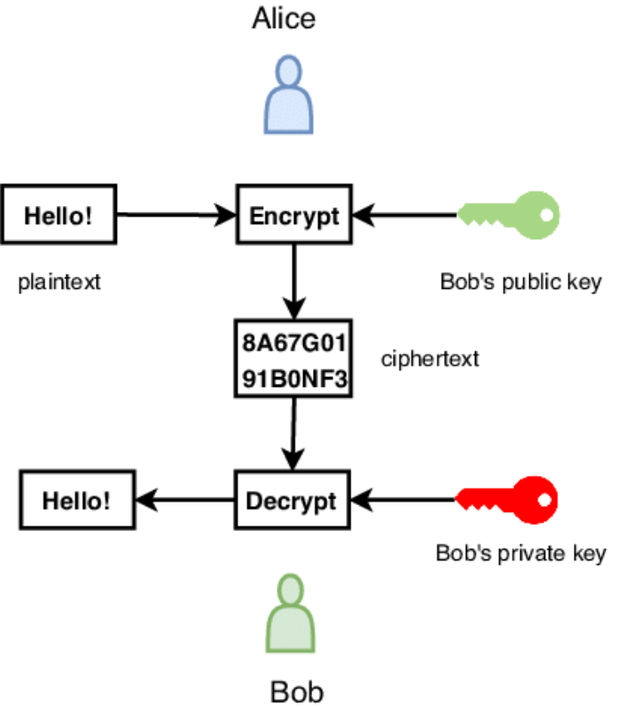
Public Key Encryption is where the sender sends a message using the public key of the recipient and the receiver uses a private key to decrypt it.
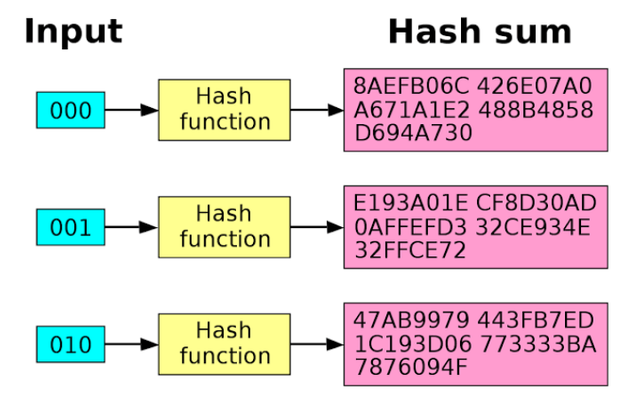
Hash Function is the code made up of mathematical and numerical characters generated for every new transaction on the blockchain. A Hush function converts an input length into an encrypted output length. It is a one-way function and it is practically impossible to reverse. It is used to validate the integrity of various input and each block contains a unique hash from which it can be identified.

What is the distinctive difference between Private-Key Encryption and Public-Key Encryption?
The distinct difference between private-key and public-key encryption is that the private key encryption works with only one (private) key while the public-key encryption works with two keys that is the public key used by to encrypt messages, and the private key used by the receiver to decrypt the message.

What happens to outsiders if a message is encrypted? Give a brief example.
If a message is encrypted, outsiders cannot see or view it. They are blinded to the message and have no access to it since they cannot read the code language and understand it, even if they try to do so. The outsiders cannot see the message being sent because it is locked.
For example in the illustration given above in public key encryption, between Slice and Bob, the other outsiders only view the cipher text and can't see the message "Hello".
Visit https://andersbrownworth.com/blockchain/hash, enter two different inputs, and show your observation. (Screenshot required).
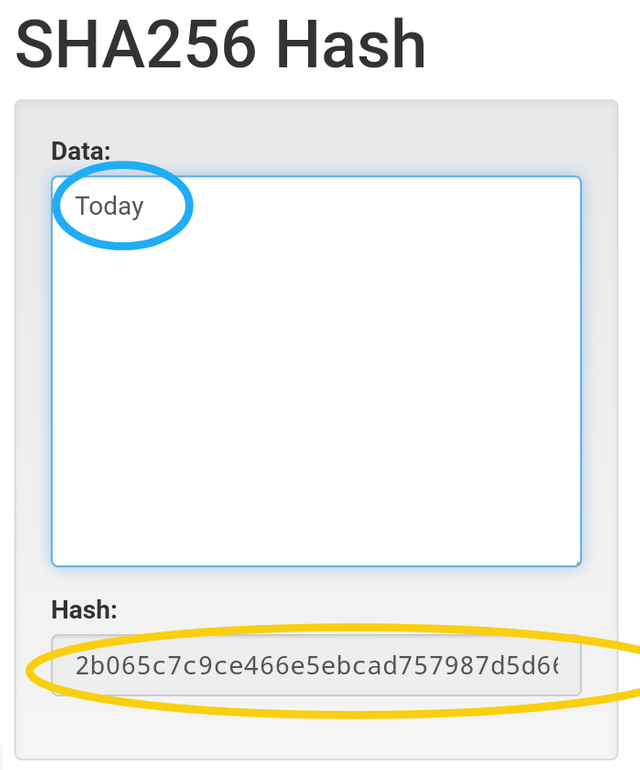
When I input the word 'Today', this Hash is generated beginning with 2b065c...
When I input the word 'Tomorrow', this Hash is generated beginning with 456a73bbcefb1def......
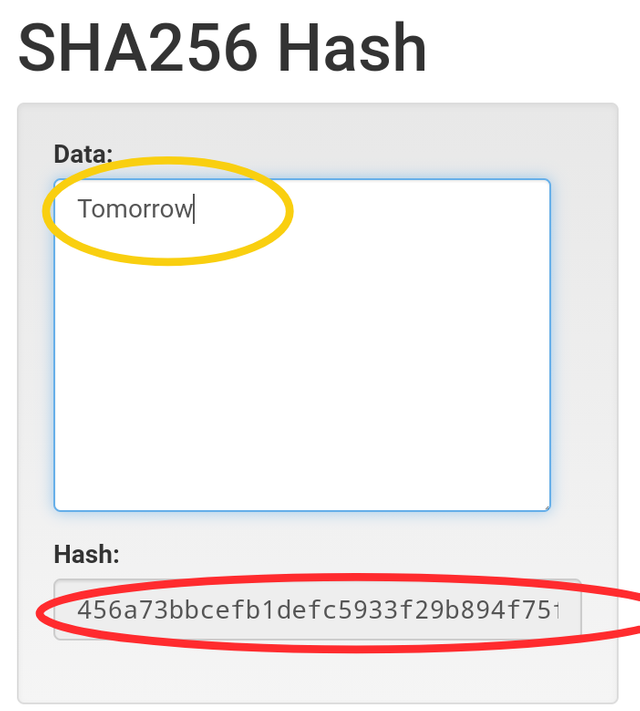
This means different input created a different hash in the above cases. Each being unique from the other.
Conclusion
I would like to conclude by saying that cryptography is very important in keeping the crypto space safe and transparent while using the private key encryption, public key encryption and Hash algorithms to validate transactions. Thank you so much and good day to you all. Bye.

Hello thank you for participating in the grassroot crypto education for kids. From my observations, I noticed that you wrote well like you understood the topic of the lecture. You do a very good job. Success to you...
Thank you for being part of steemkids community and for sharing your publication. You can join the telegram groups for kids and other social Media groups in the community
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit