Hello Steemians,
I hope you all are doing well. In my recent 2 posts in Steem Alliance, I share some useful codes that will help fresh developers to boost their work. This time we will get in-depth into your keys. Why the public keys are there and how it works in combination with your private Keys. Let's jump into it.
There are native methods available to they private keys from the master key. dSteem is available on GitHub or the latest dHive we can use dHive as it is updated.
For Example to get the private posting Key from the Master Key.
const privPostingKey = PrivateKey.fromLogin(
username,
password,
'posting',
).toString();
here PrivateKey.fromLogin import from hiveio/dhive lib.

Lets read the actual logic of this algorithm so we can develop a secure login page for our dApps.
The Secure Cryptographic Algorithm Signature Standard (SECAS) defines a set of features and functionalities for public key infrastructure. The SECP256k1 Elliptic Curve Digital Signature Algorithm is one of the algorithm standards in the SECAS framework. This article details understanding key concepts for cryptographic algorithms, as well as some of the most important security risks associated with this algorithm.
What is a Cryptographic Algorithm?
A cryptographic algorithm determines the method that is used to convert data into a form that is unreadable by anyone without a key. This means that only those who have access to the key can retrieve the original data. One of the most important features of any cryptographic algorithm is security. The point of using a cryptographic algorithm is that you can make sure that the data you are sending is private and secure. There are many different types of cryptographic algorithms, and each has its own strengths and weaknesses. A common example of a commonly used algorithm is the Secure Socket Layer (SSL) protocol. It’s used to protect data as it travels across the internet, but it’s not very secure. For that reason, many people choose to encrypt only certain types of information, like passwords and personal information, with a more secure method.
The SECP256k1 Elliptic Curve Digital Signature Algorithm
A signature algorithm is designed to create a digital signature that can be used to verify the authenticity of a document. The digital signature uses a hashing function to generate a digest of the document that can be verified by the public key that’s given to the document. The SECP256k1 Elliptic Curve Digital Signature Algorithm uses a digital signature that relies on the elliptic curve point multiplication and discrete logarithm problem to create the signature digest. The problem is that there are many factors that can affect the outcome of the multiplication, which can lead to different digest results. The security risk with the SECP256k1 Elliptic Curve Digital Signature Algorithm is that it relies on point multiplication to create its signature digest. This is a factor that can be influenced by other computers on the internet. This means that if a hacker wants to manipulate the signature, they could also manipulate the point multiplication, resulting in completely different signatures.
Security Risks with the SECP256k1 Elliptic Curve
A digital signature algorithm is designed to create a digital signature that can be verified by the public key that’s associated with the document. If someone were to manipulate the data and create a digital signature, the signature could be verified by anyone who has access to the private key. The security risk with the SECP256k1 Elliptic Curve Digital Signature Algorithm is that it uses the elliptic curve point multiplication to create its signature digest. This is a factor that can be influenced by other computers on the internet. This means that if a hacker wants to manipulate the signature, they could also manipulate the point multiplication, resulting in completely different signatures.
Summary
The SECP256k1 Elliptic Curve Digital Signature Algorithm relies on the elliptic curve point multiplication to create its signature digest. This is a factor that can be influenced by other computers on the internet. This means that if a hacker wants to manipulate the signature, they could also manipulate the point multiplication, resulting in completely different signatures. It means if the hacker reaches into the session when the password is generated then there is a high possibility of an asset being lost at any time. Phishing attacks have no concern with this algorithm. If you are a victim of a phishing attack then you need to understand that you give your private key to a hacker. You can read more about this algorithm here
Happy Blogging!!!
Special Thank to:
@rme
@blacks
@hungry-griffin
VOTE @bangla.witness as witness
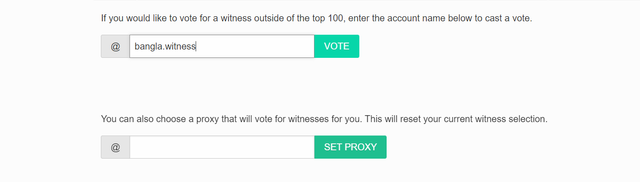
OR
▀▄▀▄▀▄ T̳̿͟͞h̳̿͟͞a̳̿͟͞n̳̿͟͞k̳̿͟͞s̳̿͟͞ ̳̿͟͞f̳̿͟͞o̳̿͟͞r̳̿͟͞ ̳̿͟͞R̳̿͟͞e̳̿͟͞a̳̿͟͞d̳̿͟͞i̳̿͟͞n̳̿͟͞g̳̿͟͞ ▄▀▄▀▄▀
@tipu curate
;) Holisss...
--
This is a manual curation from the @tipU Curation Project.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Upvoted 👌 (Mana: 3/7) Get profit votes with @tipU :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit