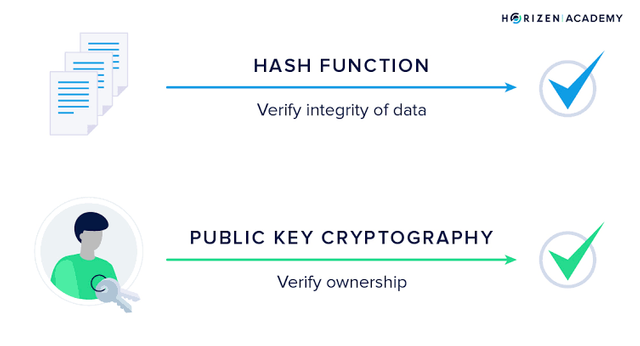
Difference between hash and cryptography
We can call Hash to encrypt any word (input) using a mathematical formula, making it unreadable, unparable and unpredictable. If we try to get Hash using the words Steem Blockchain and Tron Blockchain, we can get two different hashes with the same character. Although the number of characters in the words differ from each other, the length of the hashes we will get will be the same as each other.
The purpose of the hash is to hide the entered data. Think of any website. We go in there with our password. Our passwords are hidden and recorded in a database so that no one can see our passwords.
Several methods are used to make any information incomprehensible to people who do not want us to read the message. All these methods are called cryptography.
Difference Between Hash and Cryptography
The length of the data (input) is not important in the hash algorithm. An output of a certain length occurs. In cryptography, data is encrypted. The length of the encrypted data varies.
Keys are not required in hash functions. Keys are required in cryptography.
The hash algorithm has a one-way mechanism. That is, the output cannot be re-entered. Cryptography is bidirectional. The text/data is encrypted with a password. With the same password, the text can be opened and read again.

Greetings @crypto-01
I actually didn't know that the word Hash and Cryptography are two different terms entirely even though they are often used interwoven.
Thanks for sharing this great post with love from @hardaeborla and I hope you have a great day ahead ❤️💕❤️
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
very good
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit