
As a wallet, safety is the most important guarantee. In this article, we are going to discuss how the basic technology “cryptography” behind the blockchain works and how does it ensure the security of digital assets?
The process of generating wallet address
First, a private key is generated by a random number generator. Then, the private key generates the public key through the Elliptic Curve Cryptography. The public key can be derived from the private key, but it is nearly impossible for the private key to be calculated from the public key. Finally, the public key derives the address through a one-way hash function.
The whole process involves three cryptographic knowledge: random number, asymmetric encryption, and one-way hash function.
Random Number
Random numbers are closely related to the security of wallets. Therefore, random numbers are used to generate private keys and must have the following characteristics:
- Randomness: There is no statistical deviation, a completely messy series.
- Unpredictability: Cannot infer from the past sequence to the next number.
- Non-repeatability: Unless the sequence itself is saved, the same sequence cannot be reproduced.
Asymmetric Encryption
In asymmetric encryption, the key is divided into encryption key and decryption key, which is what we often call public key and private key. The most fundamental principle is to use the asymmetry of information.
The data is encrypted with the public key, and only the corresponding private key can be used to decrypt. Similarly, if the data is encrypted with the private key, only the corresponding public key can be used to decrypt. Because encryption and decryption use two different keys, this algorithm is called an asymmetric encryption algorithm.
Classic asymmetric encryption algorithms include RSA, Elgamal, knapsack algorithm, Rabin, D-H, ECC.
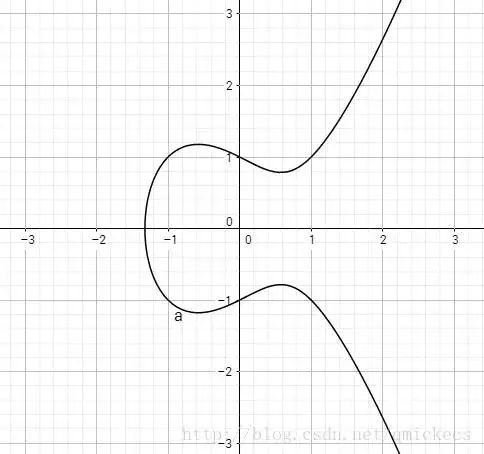
The Elliptic Curve Cryptography is mainly used in the blockchain. I won’t go into a deep explanation here. Basically, its principle is that forward calculation is relatively simple, but the reverse is an almost impossible task. On this basis, the scientists selected a curve and named it secp256k1, as shown in the following figure:
One-Way Hash Function
The one-way hash function is a function that compresses messages of any length to a fixed length (the process is irreversible). Hash functions can be used for digital signatures, message integrity testing, and message origin verification testing.
A qualified hash function often has the following characteristics:
- A fixed-length hash value can be output according to a message of any length.
- It is able to quickly calculate the hash value.
- With unidirectionality, it is impossible to reverse the hash value input.
- With uniqueness, the hash value is unique for different messages.
To sum up, cryptography is closely related to mathematics. It has a distance for general people who are just interested in cryptocurrency, so we are used to refusing to understand cryptography and related knowledge. However, cryptography plays an important role in the basic technology behind the blockchain. I hope through this article, we can understand some basic cryptography knowledge.
Finally, the important tips for wallet users again,
☑️ Make sure you have backed up all your private keys properly.
⛔️ Never reveal your private keys to anyone for any reason!
About Us
The earliest light wallet in Neo ecology. We have 100,000+ users in the European and North American markets, supporting BTC, ETH, ERC-20 tokens, NEO, ONT, and NEP5 assets.