
{Source} (https://fortune.com/2016/09/16/technology-benefits-companies-hackers/)
CONTENT
- INTRODUCTION
- ETHICAL HACKING
- WHO ARE HACKERS
- WHY DO HACKERS HACK
- TYPES OF HACKING
- WHAT SHOULD DO AFTER HACK
- HACKING PROCESS
INTRODUCTION
- A silent war is going on internet.
- Some effort is to spend on securing services, systems and networks.
- Independent computer security professionals breaking into the computer systems.
- Neither damage the target systems nor steal information.
- Evaluate target system security and report back to the owner's about the bug found.
- Ethical hacking is also known as PENETRATION TESTING or WHITE_HAT hacking .
ETHICAL_HACKING
- Independent Computer security professionals breaking into the computer systems.
- Neither damage the target system nor steal the information.
- Evaluate target system security and report back to the owner's about the bug.
- Ethical Hackers use the same tools, tricks and techniques that HACKERS use but the major difference is it is LEGAL
WHO ARE HACKERS

{Source} (https://unsplash.com/s/photos/hacker)
- A person who enjoys learning details of programing language or system.
- A person who enjoys actually doing the programming rather than just theorizing about it.
- A person who picks up programing quickly.
- A person who is expert at a particular programing language system.
WHY DO HACKERS HACK ?
- Just For Fun.
- Show Off.
- Hack others system secretly.
- Notify many people their thoughts.
- Steal important information.
- Destroy enemy's computer network during war etc.
ETHICAL HACKERS BUT NOT CRIMINAL HACKERS.
- Completely trustworthy.
- Strong programing and computer networking skills.
- Learn about the system and trying to find its weakness.
- Technique of Criminal hackers - Detection-Prevention.
TYPES OF HACKERS :

{Source} (https://blog.eccouncil.org/types-of-hackers-and-what-they-do-white-black-and-grey/)
As per working,
White hat Hackers
Black hat Hackers
Grey hat Hackers
Hackivists
Suicide Hacker's
White hat Hackers never intend to harm a system, while as Black hat Hackers hack to gain unauthorised access to a system.
Grey hat Hackers : they act without malicious intend but for fun.
Hackivists : Hacker's who use technology to announce a harmful messages.
Suicide Hacker's : They Just hack for the sake of destruction.
WHAT SHOULD DO AFTER BEEN HACKED?

{Source} (https://medium.com/swlh/what-to-do-after-youve-been-hacked-f9278ce9f761)
- Shutdown or turn off the system.
- Separate the system from network.
- Restore the system with backup or reinstall all the programs.
- Connect the system to the network
- It Can be better to call the Police.
HACKING PROCESS OR METHODOLOGY
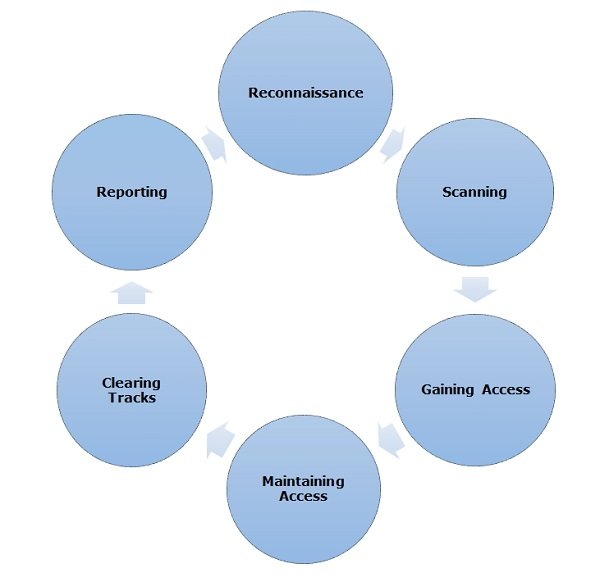
{Source} (https://www.tutorialspoint.com/ethical_hacking/ethical_hacking_process.htm)
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Acess
- Clearing Tracks
RECONNAISSANCE
- who is lookup
- NS lookup
- IP lookup
SCANNING
- Port Scanning
- Network Scanning
- Fingerprint Scanning
- Fire walking
GAINING ACCESS
- Password Attacks
- Social Engineering
- Viruses
MAINTAINING ACCESS
- Os BackDoors
- Trojans
- Clears Tracks
SECURITY IN THE NETWORKING

{Source }(https://blog.finjan.com/network-security-objectives-and-attack-modes/amp/)
Assign IP address : Two ways :
Statically: The IP address is assigned by the user to host.
Dynamically: The IP address is assigned by the DHCP server automatically.
The target can be protected from hacking by changing the IP addresses of the different Hosts.
REQUIRED SKILLS OF AN ETHICAL HACKER
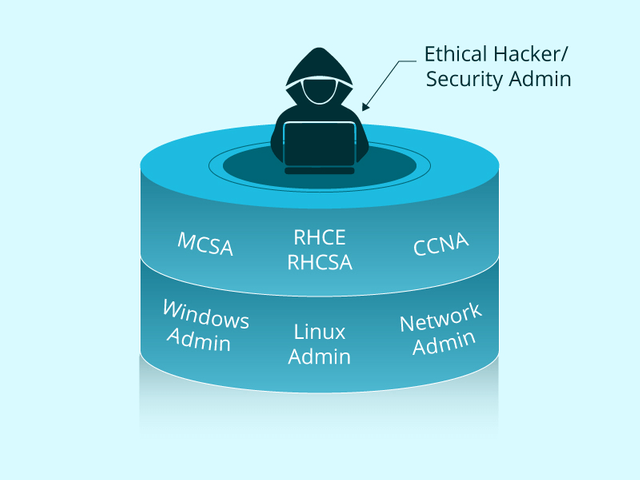
{Source} (https://texceed.in/i-want-to-be-an-certified-ethical-hacker/)
- Linux : Language of linux/ Unix ; security settings, Configuration and services.
- Firewalls : Configurations and
operation of intrusion detection system. - Routers : Knowledge of routers, routing protocols and access control lists.
- Mainframes : Knowledge of mainframes.
- Network Protocols : TCP/IP ; how they function and can be manipulated.
- Project Management : leading, planing , organizing and controlling a penetration testing team.
DEEP WEB MARKETS
- Similar to e-commerce websites or Amazon
meant for buying illegal things, - While Accessing
Anonymous Operating System. - Install the Tor browsers on your computer's.
- Use VPN
- Cover your camera by a thick peice of paper.
Great information, calling the police in my country is going to be a waste of time because they can do almost nothing about it since majority of them have very little knowledge about technology.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You are right, nowadays calling the police in every country is just wastage of time as they are not aware about the knowledge of technology, as per my opinion only technology can beat technology.
well thank you for your reply.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
With the rapid rise in hackers nowadays, we must be very careful of valueing security
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Yeah you are right and thank you for your reply
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit