Assalam-u-Alikum!
I hope all SIZ family are well and enjoy a happy life.

Here I show the solution
of computer virus.
Antivirus software:
A type of software that is used to detect and remove viruses is called antivirus software. Antivirus programs contain information about different known viruses. They can detect viruses and remove them.
Many antivirus programs are available in the market. But no single software can detect and remove all viruses many new viruses are invented and spread through internet continuously. Antivirus programs are also upgraded continuously to detect these new viruses. Antivirus is program not only detects viruses from computer, but also prevent new viruses from entering into the computer.
Examples:
. Norton Antivirus
. Kaspersky
. McAfee
. AVG
. NOD32
Benefits:
Some important benefits of using antivirus programs are as follows:
. Antivirus program protects important data from virus.
. It check all files before they entry computer system.
. It alert the user about the virus before it causes any damage to computer.
. It quarantines or eliminates a virus so that it may not harm computer.

Security Threats:
Data is an important and valuable asset of any organization. It is more important than hardware. There are different Threads to data security. The data can be damaged in two ways:
Intentional Threats:
A user can intentionally delete important data. The intentionally threads may occur for the following reasons.
. A hacker can delete data on a computer.
. An angry employee of the organization can delete the data.
Unintentional Threats:
The unintentional threats to data security are as follows:
. An authorized user of data may delete or change the sensitive data accidentally.
. A technical failure of the hardware may damage the data.
. A sudden power failure may also cause data loss.

Solutions to Data Threats:

Pixabay
The data can be protected using different methods. Some important ways to minimize security threats are as follows:
User Rights:*
The users must be assigned proper rights to minimize security threats. Every authorized user should not be followed to change or delete data. The user with certain rights may be allowed to delete or modify data after following a step by step process.
Periodic 🔙 up:
Periodic backup of data should be taken regularly. The backup can be used to meet the situation of some occurs.
Passwords🔑:
Another solution to these problems is the use of proper password. Passwords must be entered to use any resource. A log file should also be maintained to keep track of all the activities on data and files. Authorized users should change their passwords periodically. Very short and common words should not be used as passwords.
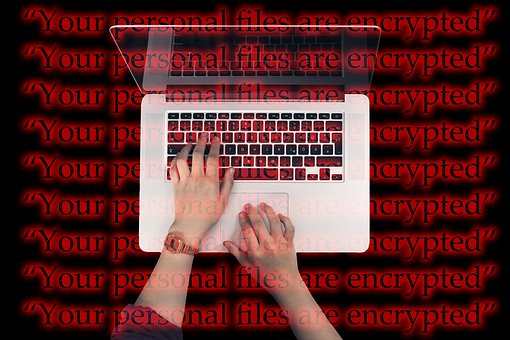
Encryption:
Some strong encryption algorithm should be used. Encryption is a process of encoding data so that only authorized user may understand and use it. If an unauthorized person gets access to the data, he should not be able to understand it.
Scanning:
The data provided to organization must be scanned before used. Proper virus scanning software should be used to scan all data. The software can detect the infected data and in the indicated message to the users.
Lock🔐:
Computers and all baking storage devices should be placed in a locked rooms. Only authorized users should be allowed to access these resources.

Cause of computer virus and its type
If you want to know part-01
follow this link below:

Cc:
@cryptokraze
@siz-official
@suboohi
@vvarishayy
Regards:@ahsansharif






You make a very good post
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for sharing this great information about virus
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you for posting in SIZ Community.
your post has been chosen for the top 5 posts of the community. We are giving you a 100% vote from @siz-official which is the community curation account. Keep sharing the quality content. Your reward of 2 steem will be with you within 24 hours.
You can delegate your SP to @siz-official and take benefit of our Delegation Rewards Offer of getting up to 200% Curation Rewards
You can also use these quick delegation links. Just click on your desired amount of SP you want to delegate and it will be done in process of 1 minute.
50 100 200 300 400 500 1000
2000 3000 4000 5000 10000
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks a lot sir for choosing my post in top 5 .
I will try to do best ☺️
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You have worked very hard to create a post. Your post has given us more information
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Every one learn a lot for this post
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit