Self Defending Network

source
The Self Security Network is a long-term strategy to protect the organisation's business processes by identifying, preventing, and adapting to threats from both internal and external sources. For many years now Cisco's integrated, flexible, and integrated network security systems have been helping organizations around the world secure their network infrastructure.
The concept of a secure network is not new. In the early 2000's, leading network vendors and security vendors such as IBM [1] and Cisco [2] used the term to describe the network as a platform. A collection of network and security services that work together as a single unit to protect themselves from cyber attacks by continuously adapting to stay ahead of online threats.

source
10 years ago, the technology and tools needed to bring together more vendors to build defensive networks were very limited. Moreover, the cost of building such a system was prohibited, and the whole market was not yet ready. Many security vendors had closed systems that did not have the ability to integrate with other third-party systems. Protective networks were more mythical than reality as organizations did not have a mature enough network and security ecosystem to use it.
Things have changed. Today, the technical glue for bringing different devices to the homogeneous frame is mature, and the market is ready. Advances in data analysis, Robotic Process Automation (RPA), Machine Learning, Artificial Intelligence, and Application Programming Interfaces (APIs), incorporate all the ingredients needed to build defensive networks.
What a self defending network is ?

source
Overall, self-defense networks include technologies, processes and people. From a technical point of view, the ability to manage, monitor, organize, automate and respond to cyber attacks quickly and efficiently is at the center. All protective network components are assembled using a set of automated tools and processes that provide glue to all networks and security layers.
An effective horizontal protection system also called deep protection ensures that all components work together as one. Devices that provide anti-virus, proxy, firewalling, VPN, storage detection, IDS / IPS, risk assessment, pool management, SIEM, policy compliance, route, and switching are fully integrated. All of these components are integrated and tightly integrated using a distrust vendor approach to provide deep monitoring, management, singing and automatic response to effectively protect against cyber attacks.
A trader-centered approach is needed to ensure that corporate security investments are protected in order to effectively protect current and future threats. Depending on the needs of the organization, over time, vendors and technologies can be modified as needed, without stitching, to ensure minimal disruption to the entire security infrastructure.
Objectives of the secure network.
The main business objectives of a secure network or network-like platform include:
(1) Ensuring that security procedures and policies are in line with business needs
(2) Ensuring that security operating costs are manageable
(3) Reduce complexity and simplify the overall network and security infrastructure in order to increase efficiency
(4) Prompt detection and response to online threats.
How do defensive networks work?
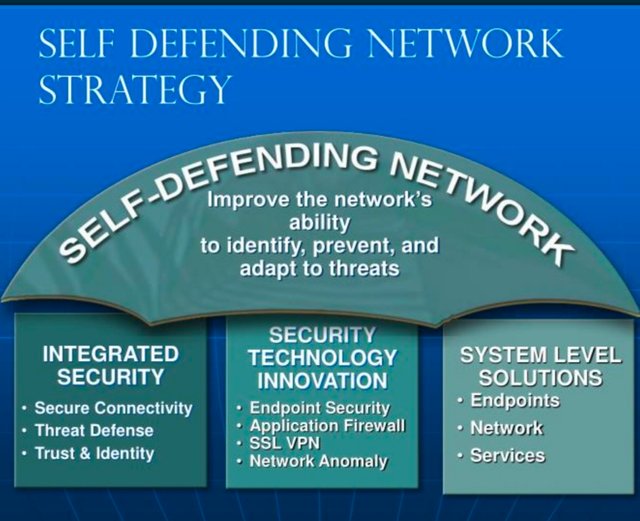
source
The main components of a secure network can be divided into 5 key categories: central management, monitoring, automation, orchestration and response.
•Central management and deep integration:
In order to enforce an organizational goal, central management is needed to bring all the different components into a cohesive ecosystem. One command and control look ensures that policies and procedures b
In order to enforce an organizational goal, central management is needed to bring all the different components into a cohesive ecosystem. The central management engine implements the organization's security policy at the international level.
• Ongoing monitoring:
Monitoring is essential to ensure visibility throughout the ecosystem. The SIEM solution is used as a centralized search engine for all logs and events collected from devices. That data is then sent to the engine for compilation and storage. By using Big Data and security statistics, event affiliates can be used to give the entire network a more defensive intelligence.
•Orchestration and Automation:
Automation refers to the use of playbooks and rules that provide the removal layer needed to develop response systems. Using a variety of tools and technologies such as RPA, automation allows processes to be well organized. Low network operations can be automated to free up valuable time for security teams so that they can focus on critical events. The rules are consistently pushed into devices that enforce a deep defense mechanism where protection is applied in a few stages in order to be more effective against cyber attacks.
•Immediate response to an attack:
The end result of an effective defense network is the ability to respond faster than current systems can. Through deep integration with devices that are part of a secure network, playbooks and rules are used to perform specific actions. For example, ransomware is detected at the end point device, not only is that threat reduced in the end, but nearby network switches can block the device by blocking the hole until a successful fix is used. Importantly, the organization can significantly improve Mean Time To Detect (MTTD) and Mean Time To Respond (MTTD).
Why is a self-defensive network needed?

source
Businesses around the world are facing increasing challenges to protect their digital assets against a growing number of cyber attacks. The global shortage of skills in cybersecurity does not make it easy.Cybercrime is growing rapidly around the world. Global cost is estimated at $ 6 trillion annually by 2021 . Businesses continue to look for ways to stay ahead of cybercriminals by ensuring that their network and security infrastructure is able to detect and take immediate action against cyber attacks before any damage occurs. Doing this effectively and economically remains a challenge for all organizations around the world.
There is no shortage of technology to protect against cyber attacks. What is missing is a fully integrated ecosystem that can ensure that people, processes, and technologies work better together in a harmonious way to defeat even the most persistent and well-resourced attacker.
Of course, technology alone is not the answer to cyberbullying. Glue between people, technology, and processes must be present. Protective networks can help achieve that.
Benifits of self defending network

source
• Integration of security across all network components
•Interoperability processes between a variety of security and network features that allow to measure performance and services in need of customers
•The network's ability to adapt to new threats as they emerge
•Performance has a small impact on existing route and change infrastructure, partitioning and access control strategies, and other organizational structures that support these programs.
•Reduced distribution and impact of attack on a system that always works
•Independent systems can respond quickly to attacks with little or no intervention.
•Improving infrastructure availability and reliability.

Special Thanks to
@cryptokraze
@siz-official
@suboohi
@vvarishay and all siz staff for support.
Regards,
@ansooch

Good post dear friend keep it up dear friend and keep learn with our steem fellows and friends.
Regards, Faran Nabeel
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit