Assalum-o-alaikum, hope you all are doing good! Every one of us browse various websites on daily basis, some websites ask for our confidential data such as emails, passwords, and other details, have you ever wondered how this confidential piece of data travels from us to website server without getting leaked or hacked by any scammer, here cryptography comes into play.


What is cryptography
It is the study of techniques to make the data secure for safe communication in the presence of malicious third parties.
In simple words, cryptography provides us the way to convert plain text to unintelligible text or vice versa. It provides the solution for the safe travel of data on big networks without being compromised. If you want to transfer your password string from your PC to some server, you need to use cryptographic techniques, so that in case someone intercepts the communication, he still would not be able to decipher what that data meant.

Basis of cryptography
There are three parts of cryptography fundamentals: C I A
Confidentiality (C):
It aims to provide confidentiality to the information transmitted from one place in the ciphered form to another, so even if someone gets access to your data he still could not decipher it.
Integrity (I):
Integrity means to make sure that the data that we transmitted has not been modified/altered. Failure in maintaining data integrity results in corruption of our data. To keep track of whether our data has been changed or not, hash functions are used.
Availability (A):
Availability means that the data should be readily available to its users at all times. To make sure that data is available the network admin always maintains hardware and does regular system upgrades has a backup plan for failure, and prevents bottlenecks at all costs in a secured network.

Steps of cryptography
There are two basic steps to do cryptography:
- Encryption
- Decryption

Encryption
Encryption means converting plain text to unintelligible text, using this technique sender ciphers his message into such form that even if someone intercepts and gets access to data he will not be able to truly understand what that data meant. Different sorts of algorithms are used to convert plain text into ciphered text.
I demonstrated the process of encryption in the following python code.
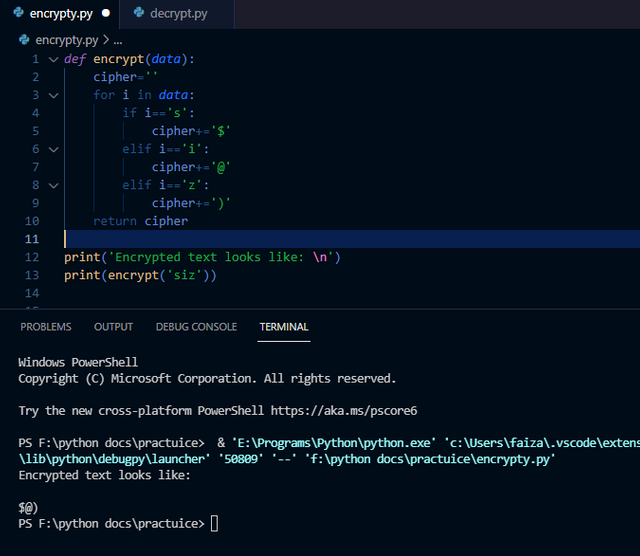
When "siz" is given as argument to our algorithm, it gets converted into "$@)" which is impossible to decipher if the unintended receiver receives it.

Decryption
The second part of cryptography is decryption. Decryption means deciphering the ciphered text back into plain text so when the message is received by the intended user, he successfully understands what the sender meant. Deciphering is also done using algorithms.
I demonstrated the process of decryption in the following python code.
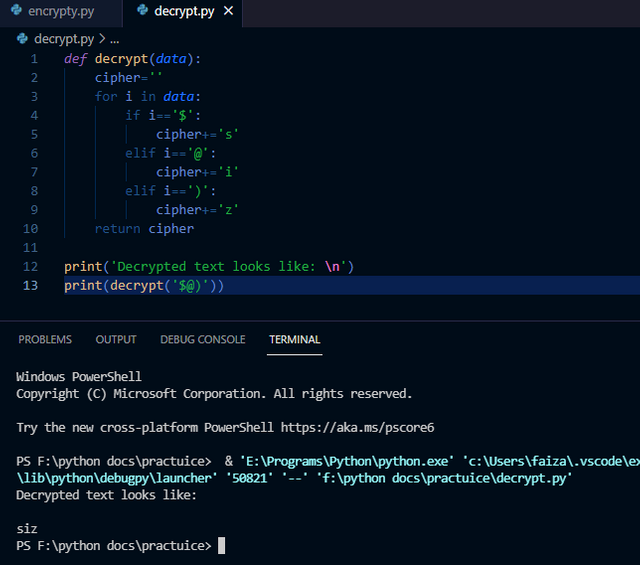
When "$@)" (the ciphered text) is given as an argument to our algorithm, it gets converted into "siz" (plain text) which is easily understandable when the intended receiver receives it.

Conclusion
I hope you find this post interesting and useful. I hope now you all know how our data stays safe on the web. Let me know if you want me to post more content like this. Hope you guys learned something from my post.
Regards, @faizan2sheikh
Thanks to:
@cryptokraze
@siz-official
@vvarishayy
@arie.steem
@suboohi
Thank you for reading my post!

if write our community name in algorithms that's it will write as "$@)" ..your study is very interesting bro thanks for sharing with us.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit