assalamualaikum
Good night and greetings to all of you. And my best regards to @siz-official, @suboohi and @cryptokraze. On this occasion this night I would like to discuss how to Handling and Prevention of Ransomware Incidents. Here's a little about the meaning of Ransomware.
Ransomware is a particular type of maliciois software that demands financial ransom from a victim by holding onto assets or personal data. Ransomware distribution activities are carried out by attackers or Treat Actor with the main objective being financial, therefore Treat Actor makes personal data a threat.

1. Introduction
Ransomware is the name of a class of malware consisting of two words, ransom and malware, which aims to demand payment for personal data/information that has been stolen, or data whose access is restricted. Today, malicious software has diversified the way they extort money from victims.
The emergence of ransomware has become a global epidemiology as it continues to take its toll on the world, forcing a company to decide between trying to restore data from backup and paying a large ransom to hackers.
Based on the picture above, the Ransomware attack begins with malware arrival which is marked by activity from the user, either by clicking a malicious link or malicious software. Any malware that has been clicked by the user, automatically connects to Command and Control which is a center for malicious software activities to send commands and control Victim. Each targeted file will be encrypted and a file note will be displayed containing the attacker's email address and payment account number to be able to decrypt the file. locked.

2. Ransomware Type
Based on the type of ransomware can be categorized into 4 types, namely:
- Encrypting Ransomware
This type, once executed, will secretly search and encrypt important files on the victim's computer system. Then a message will be displayed to a user containing a ransom request in order to restore the locked file. After the ransom is paid, the victim will be given a key or code for the description, which can be run specifically to describe important files on the victim's computer system.
- Non-Encrypting Ransomware
In contrast to this type, this type of ransomware can lock user access to a computer system without encrypting the file system and display encryption on the file system and display a message for the attacker to demand a ransom or request action from the user who needs money to unlock the lock.
- Leakware or Doxware
While this type is different from the previous one, this type does not block access to the victim's computer system or any information. On the other hand, they secretly collect sensitive information from computer systems and use them to blackmail or blackmail victims. The information that has been collected is then stored on servers or other infected machines and they threaten the victim that the data will be disseminated if the payment is not made.
- Mobile Ransomware
This ransomware targets mobile devices and targets the sensitive data of device users. They restrict access from users to the victim's data, and display information about the details to be paid along with the attacker's information on the victim's device.

3. Handling Ransomware Cyber Incidents
In handling this incident, it is necessary to conduct a search related to the cause of malicious software resulting in the locking of user data. This activity can be carried out according to the following steps:
a) Preparation Stage
At this stage, policies, procedures, technology and human resources must be fully prepared, so that they are used in the incident handling process. Responding quickly to an incident is a basic preparation for handling ransomware cyber incidents. Here are the steps that can be taken:
set up a cyber incident rapid response team which can be internal or external.
prepare a supporting document for handling incidents.
Coordinate with related parties.
prepare tools that can be in the form of License Tools, Open Source Tools and other open sources.
b) Identification and Analysis Phase
Identify and analyze the system in order to get the root cause of the incident that occurred. Here are the steps that can be done:
identify the type of ransomware for further analysis.
check the antivirus is working normally or not. This is because there is malware that can destroy the anti-virus installation.
perform identification and analysis on the system environment that is useful for searching for persistent mechanisms or digital artifacts resulting from attacks carried out.
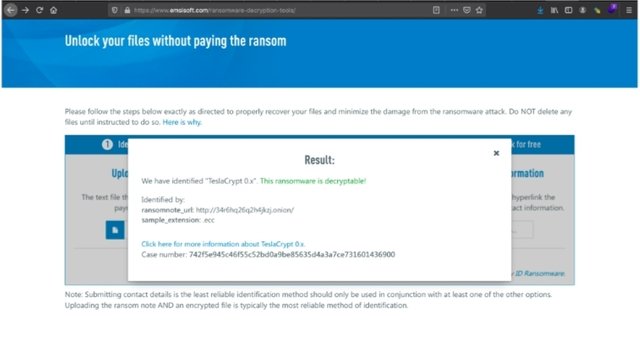
Identification and analysis can run, for example using process explorer tools to identify malicious running on your computer system.
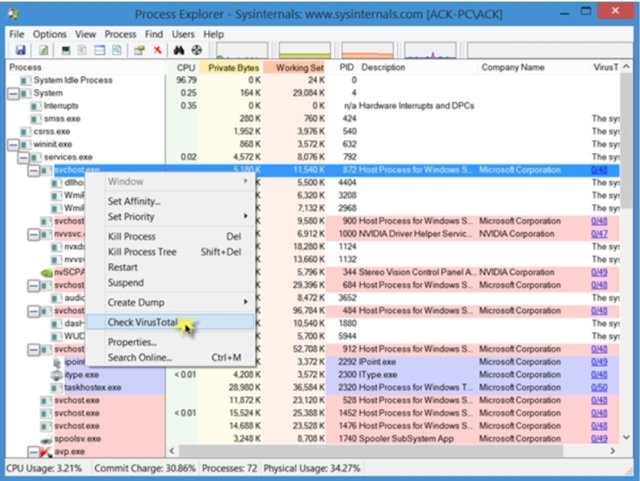
Identification and analysis of communication networks using Netstat tools to identify malicious connections both with listening status.
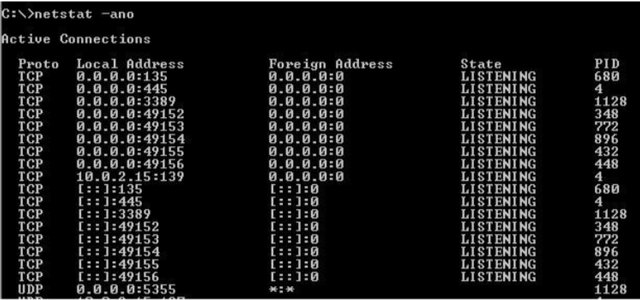
Identify and analyze registry, startup applications, scheduled services, browser history by using Autoruns Tools to identify affected systems.
Identification and analysis of system logs to find the history of attackers in carrying out attacks on the system.
c) Retaining Stage
This containment phase aims to prevent the spread of ransomware. This procedure is carried out at the detention stage as follows:
isolate the affected system so that the ransomware cyber incident does not spread through the network, for example by closing access to the network.
change the routing table configuration on the firewall to separate infected systems.
perform data backup on the affected system.
identification of similar symptoms on other systems to prevent the spread of attacks.
d) Elimination Stage
This removal stage is a stage where several different techniques are used to analyze the malware and remove the malware from the infected system. Here's the process:
stop processes infected with malicious processes.
remove suspicious autostart processes from autostart application results.
remove unknown users to avoid malware re-entry.
do a full scan of the system using an updated antivirus signature.
e) Recovery Stage
This recovery stage is the stage of returning the affected system to its normal condition as before. Here's the process:
perform a description of the affected files using the available decryption tools.
perform system validation to ensure that there are no corrupted or infected applications or files.
perform monitoring activities to monitor the connected network.
rebuild from the last backup file of the system owned.
do updating / patching computer systems and antivirus.
f) Follow-up Stage
This stage is the stage where all documentation of activities carried out is recorded as a reference for the future. Here's the process:
Create documentation and reports related to handling cyber incidents.
provide analysis and explanation of what should be done so that similar incidents do not happen again.
write down the evidence found.
make evaluations and recommendations.
increase knowledge about handling ransomware incidents.
implement a monitoring system for detection.
increase system defense.
improve procedures for handling cyber incidents based on incidents that occur.

4. How to Prevent Ransomware Incidents
Here's how to prevent these incidents from happening:
- always make sure your computer gets the latest patches and the latest updates.
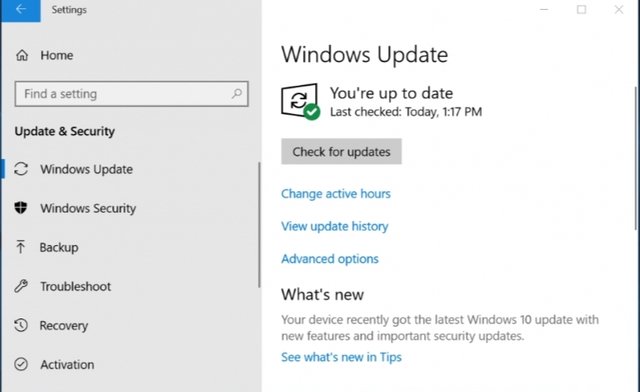
To get a computer system, make sure you get the latest patches and the latest updates, it is necessary to do the Windows Update feature activity. This feature will always check for the latest updates on the computer system data center. Every update received will be installed on the computer system, try to do a backup before updating the system.
- Perform Computer Scanning Using the Latest Antivirus
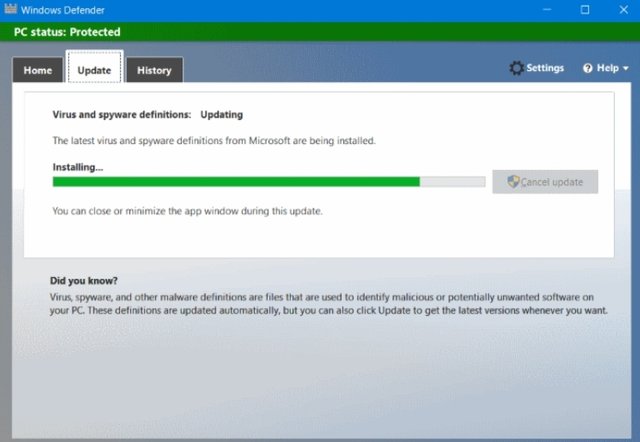
Antivirus that is available by default from Windows computer systems is Windows Defender. This serves to help the computer system to find out the presence of unknown applications or have links with malware. Make sure to always scan the system and update the antivirus.
- Be Alert On Every Link Received
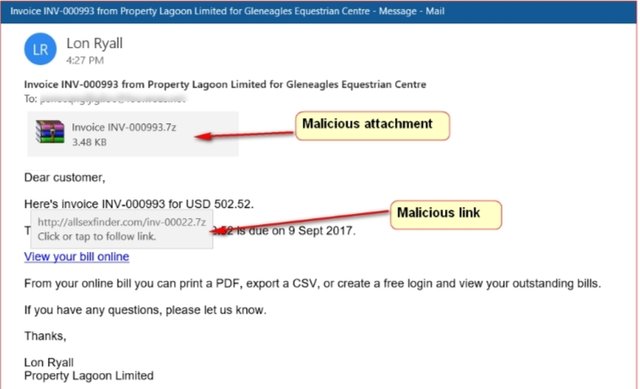
Always be aware of spam emails that enter a link to be clicked on or download a file. It would be nice if you first check each link using VirusTotal, in order to get information that the link is safe or not.
- Always Enable Firewall On Computer
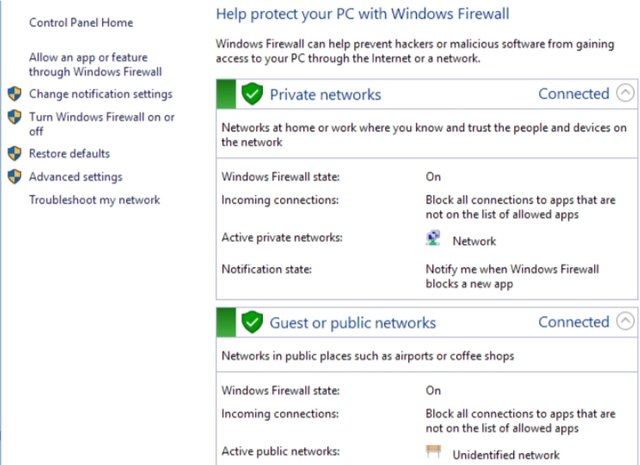
Windows Firewall is one of the most important windows of the Windows OS. Windows firewall features continue to be improved, such as controlling outgoing connections from applications and users as well as being able to manage Windows Firewall quite easily. This program in windows will be easily set up automatically and create a rule in the windows firewall so that the program can update.
- Activate the Save Browsing Feature
This save browsing technology can check billions or trillions of URLs per day for unsafe sites. Every time Google discovers thousands of new unsafe sites, most of which are legitimate sites that have been compromised. If the site is detected, Google will display a warning and can search to see if the site is currently dangerous or not.
- Do Backup Important Files Periodically
Perform regular backups of important files by backing up data on external storage media. This is useful to prevent if the data is damaged, it will be possible to restore the last system to do a backup.

So, that's my article on how to handle and prevent ransomware incidents, I hope it's useful and thank you.
.jpeg)
.jpeg)
.jpeg)
.jpeg)
.jpeg)
.jpeg)
.jpeg)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Good tutorial post dear friend keep it up bro and keep learn with our steem fellows and friends.
Regards, Faran Nabeel
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Very detailed and informative post. Keep growing with steem.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit