What Are Evil Twin Hotspots
Evil Twin hotspots are rogue Wi-Fi hotspots that are created and used for deception and harvesting users’ private information. One the of the main security dangers when using open/public Wi-Fi is the Evil Twin. Think of it this way, in addition to the Wi-Fi access point that you regularly use each time you connect to Wi-Fi at Starbucks¹; there may be an “access point imitator,” a.k.a. Evil Twin that cannot be distinguished from the “real” access point. You most likely would not know if you connected to the actual access point or the fake imitator.
How Evil Twin Hotspots Trick Users
The last time you used an open/public Wi-Fi hotspot, did you pay any particular attention when connecting to the hotspot? I expect that the majority of us did not, it is like flipping on the light switch at home. It just works and rarely does one consider what is taking place. Therein is the first danger of the Evil Twin. Most users are too naive about Wi-FI security, assuming that since Starbucks offers the service, it must be safe. That is simply not true! That misinformed idea is why the Evil Twin concept works so well.
I am writing this post at a Starbucks, and when I first connected to the hotspot, I had many choices from all the overlapping local Wi-Fi networks. Having connected to Starbucks before, I knew I was looking for a Google hotspot like this:
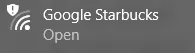
I have connected to Starbucks hotspots hundreds of times and never have had a problem. But I also wondered about the presence of an Evil Twin and carefully considered what I was doing. From experience, I know that Starbucks’ hotspots follow the naming convention of “Google Starbucks²,” if I happened to see two hotspots with that name, that would throw up a big red flag and I would not connect to either and would contact Starbucks or Google support. I would also stay away from any open/public hotspot that is named using any other combination of Starbucks, Google, coffee shop, etc.. Also, I never connect to any open/public hotspot that is available that I do not recognize or know something about, doing such is just asking to be hacked!
The Evil Twin trick is it looks like a legitimate and expected hotspot name.
So what can be done to minimize risk when using open/public hotspots?
The first thing to consider is always using an encrypted connection. This type of connection is becoming more and more common, and I expect soon it will be the default browser connection. For instance, when you log onto Gmail, by default you are using a secure encrypted “https” connection.
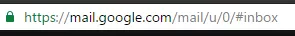
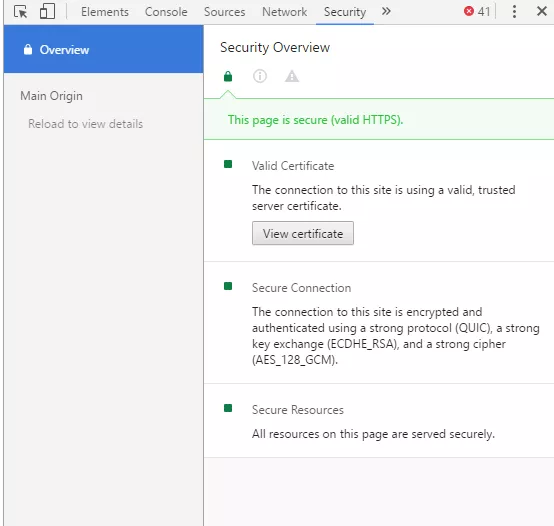
However, it is a good idea to verify that the connection is secure by clicking on the “lock” icon in the URL area³ to review details about the SSL certificate.
Another way to securely encrypt all traffic is by using a VPN (Virtual Private Network). In a nutshell, a VPN connection securely sends all the traffic through an encrypted tunnel. But, and this is a big “but,” even VPNs are not 100% secure. Once your requests hit the VPN server as encrypted requests, they leave the VPN server in an unencrypted mode. But as the request is answered and comes back to you the originator, it is encrypted once again at the VPN server and delivered to you. This means in the Starbucks example, all traffic leaving and returning is encrypted. That is the nature of VPNs, so always use a reputable VPN service. There is some trust that must occur.
Secondly, a wise step is to never auto-connect to open/public hotspots, even if recently used.
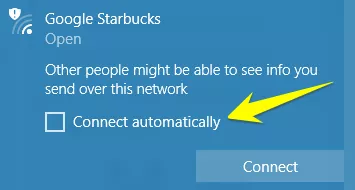
Although a convenience to auto-connect, it is not prudent to do such. That allows you to review the access points available and manually select the best choice. I add another step here, I never connect to an access point, even a trusted one, with my browser open and waiting where last left off, i.e., for example with my email page open, just in case somehow I get connected to an Evil Twin. I always connect, then start a browser that I do not use as my default (Mozilla in my case) and allow the hotspot terms and agreement page to come up and I accept it there. I then connect my VPN and open my default browser, Chrome, and begin working. It may seem like a lot of trouble, but it soon becomes routine, and this practice has kept me safe thus far.
I also use a Chrome extension called HTTPS Everywhere. The explanation below comes directly from their website:
“HTTPS Everywhere is a Firefox, Chrome, and Opera extension that encrypts your communications with many major websites, making your browsing more secure. Encrypt the web: Install HTTPS Everywhere today.
HTTPS Everywhere is produced as a collaboration between The Tor Project and the Electronic Frontier Foundation. Many sites on the web offer some limited support for encryption over HTTPS, but make it difficult to use. For instance, they may default to unencrypted HTTP, or fill encrypted pages with links that go back to the unencrypted site. The HTTPS Everywhere extension fixes these problems by using clever technology to rewrite requests to these sites to HTTPS. Information about how to access the project’s Git repository and get involved in development is here.”
Other things that can tip one off a user that something is awry, i.e., connecting to an Evil Twin, are unusual pop-ups occurring about unencrypted connections, requests to download something that you did not initiate or an unusual slowness to your computer and/or your connection.
And lastly, if I have any concerns with the security of the available hotspots, I just turn to the hotspot on my Android phone.
¹ Evil Twin access points are not limited to Starbucks; they can exist on any public or free Wi-Fi hotspot.
² The standard naming convention for Starbucks hotspots could be different in your area and may be subject to change. Keep that in mind and ask if you are not sure.
³ This example is from the Chrome browser.