A lot of people choose ICO's nowadays as a red-hot fundraising tool and where there is money, there lies the eyes of the hacker. Blockchain itself is secure, but the fundraising mechanism is sometimes way too vulnerable to compromise. We have seen a lot of reports on ICO security breach in last few months. A recent report of Fortune states, Hackers Have Stolen $400 Million From ICOs since 2015. The following table was enough to encourage me to dig more into ICO's.
| Name | Stolen amount | Date | Description |
|---|---|---|---|
| Etherparty | Not Revealed | 01/Oct/2017 | Hacked into website and altered the donation address. |
| Enigma | 0.471M USD | 20/Aug/2017 | Hacked into slack, website and email newsletter accounts and manipulated users to send funds to hackers wallet. |
| Coindash | 7M USD | 17/Jul/2017 | Hacked into website and altered the donation address. |
| Apex | 0.15M USD | 29/Jan/2018 | Hacked into website and altered the donation address. |
| Seele | 2M USD | 5/Feb/2018 | Hackers compromised telegram admins account and lured users for a private presale. |
| Veritaseum | 8.4M USD | 26/Jul/2017 | Unauthorized transaction from wallet. |
From the above table, we can see that in most of the cases weak protection on DNS and Hosted server was the main reason for ICO hacking. There were some cases where there was backdoor on smart contract, but nowadays most of the companies copy solidity codes of other popular and secure ICO's. So the chances of smart contract hacking are negligible in this case.
This is Tarek Siddiki, a Bangladeshi security enthusiast. I worked with various bug bounty platforms and helped hundreds of companies to patch a lot of vulnerabilities in past few years. I continued my bug bounty approach in ICO's and in this blog I will talk about my experience with a few ICO's. In most of the case the company acted promptly and welcomed the approach, but there were few who really deserves to get sued because of their negligence on security.

Hacking into ICO's
I have tested a lot of ICO's since November 2017 and I successfully exploited few of them. Here, I am going to share the story of those 5 ICO's, what did I find, how did I find, what was the impact, how I reported to them and what was their response etc.
I have decided to publish the names and details of the vulnerabilities of those ICO's who successfully completed their fundraising, the one with asterisk marks are those who have not yet launched their ICO's.
Story of Fundyourselfnow
FYN was my first successful ICO hack. I was able to get the admin panel access during their ICO. I used blind XSS payloads in my KYC form. A few moments later an admin went to validate the submission and my payload triggered. I received an email with the canvas screenshot and cookie of the admin user. Those were enough to access the admin panel.
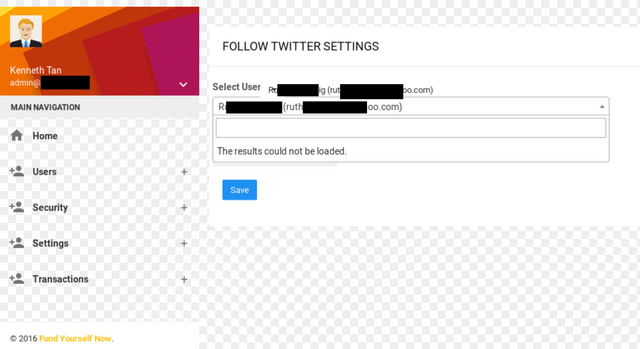
Reaction and Impact
The team was very surprised with this kind of vulnerabilities within their system. They implemented a patch within an hour and later conducted a thorough security audit on their platform. No other vulnerabilities were discovered and there was no sign of any other breaches at that time.
Story of Agrello
Agrello suffered from the same vulnerability as FYN. Both portals were using CodeIgniter framework and XSS payloads were not filtered. I used a blind XSS payload in my KYC details. As soon as an admin tried to validate my details, the payload fired and I got the cookies and canvas screenshot.
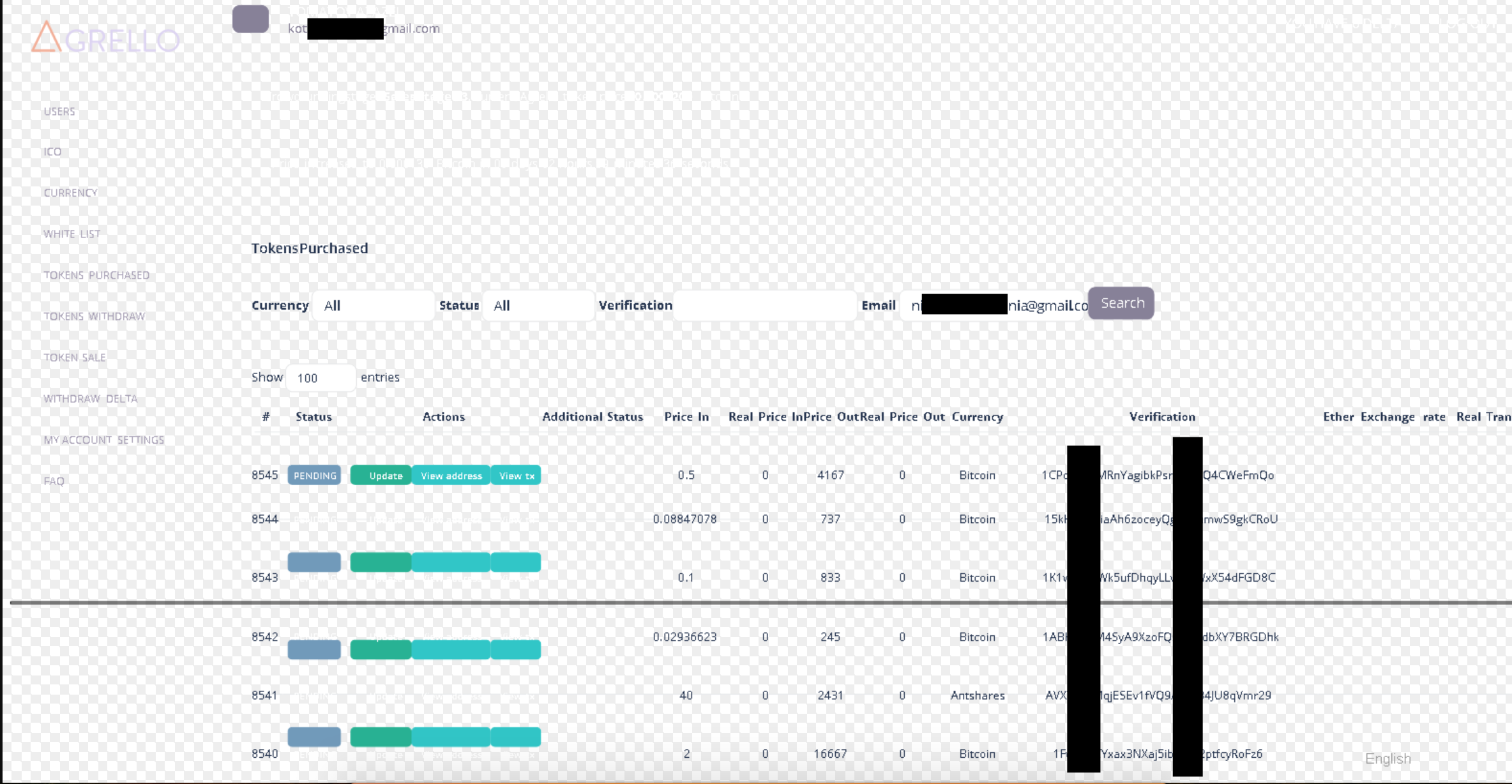
Reaction and Impact
Admin panel could be accessed by the attacker and details of all incoming transactions and all participating users could be monitored. Agrello rewarded a handsome amount of bounty for this disclosure and they were prompt to resolve the issue.
Story of Zeepin
I am a fan of NEO and it's ICO's. That's why I decided to look into Zeepin. Within first 5 min, I identified an error based SQL injection vulnerability on its KYC portal. I was able to enumerate the database and all its tables. The tables included KYC details, user details, bounty details etc. I tried to check whether I could dump database entries or not and successfully dumped the first two row of the zeepin_upload table as a PoC.
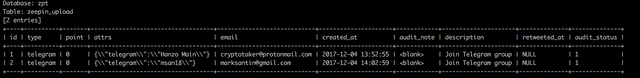
Impact
It was possible to read all the database tables, which includes all participants personal information, email, password, deposit address, bounty details etc.
Reaction
I contacted one of their telegram admin to get a proper point of contact to disclose the vulnerability. That guy redirected me to another telegram admin and I disclosed the vulnerability to him. They were prompt to resolve the SQL injection cause normal users were having trouble because of my test! But when I discovered another XSS on the KYC application, the telegram admin said this:
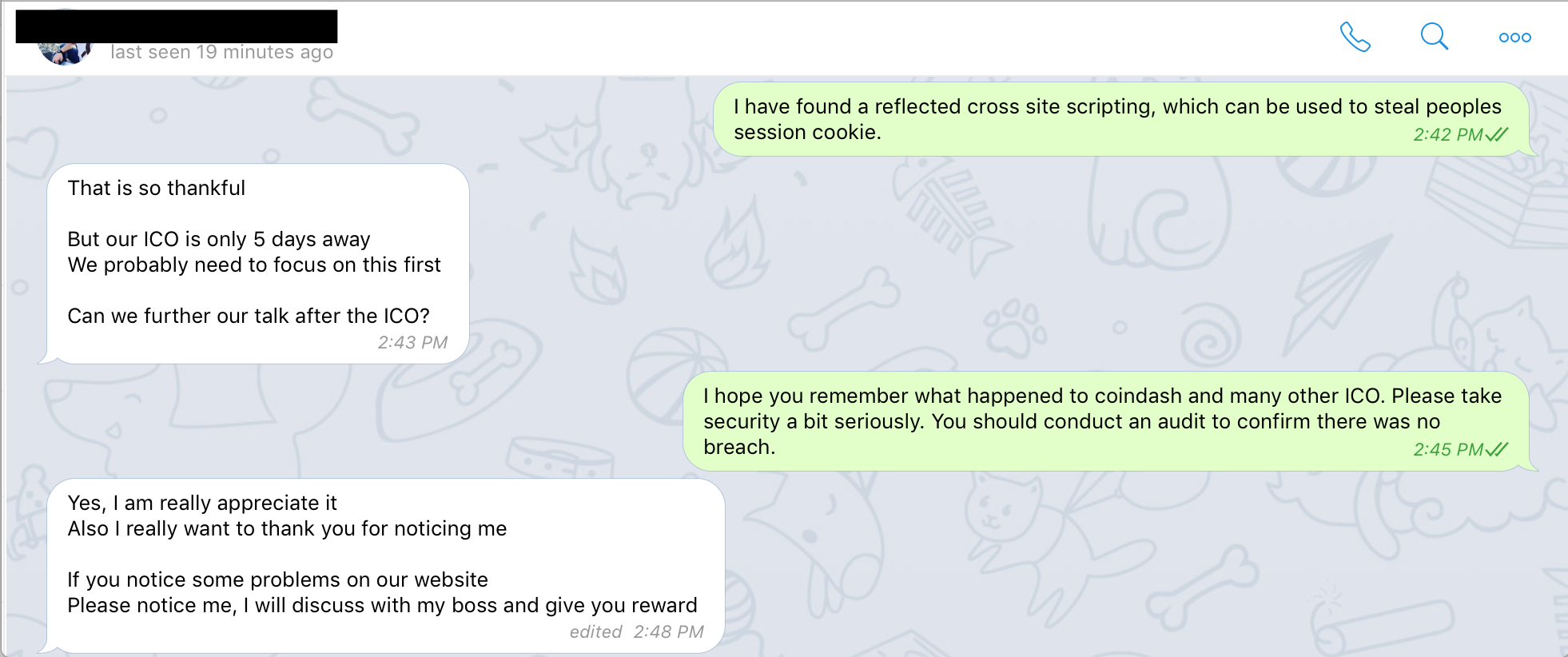
You are collecting 60M USD+ NEO from peoples and keeping all their sensitive KYC documents unprotected. When I tried to help you, you were more passionate to grab peoples money rather than securing the process! The height of negligence surprised me. I have never encountered such thing in my entire life from a company where millions of dollars were at risk. Luckily there was no other hacker poking into this and they escaped.
Later when I asked them about the permission to write this blog, they replied:
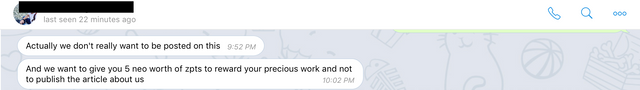
It's true we, the bounty hunters take bounties after disclosing security issues. But the way they handled the whole thing, made me bound to reject the offer.
Story of ******
This one is so far my most favorite finding. The company neither launched its ICO, nor the KYC is open for public. So, apparently there was no interface where an outsider could poke the services. Fortunately, their demo application was hosted on the same server where the main business website was hosted.
I found an interesting RCE in the file uploader on their demo application.
<?php
$destination_path = getcwd().DIRECTORY_SEPARATOR."upload".DIRECTORY_SEPARATOR;
$dataURL = $_POST["image"];
$imgID = $_POST["uid"];
$parts = explode(',', $dataURL);
$data = $parts[1];
$data = base64_decode($data);
$file = $destination_path . $imgID;
$success = file_put_contents($file, $data);
print $success ? $file : 1;
?>
You may wonder how did I get my hands on this piece of code! As I said, there was an RCE and I was able to read/write anything on the server. I was also able to read the .my.cnf file to gain access to the cPanel and DNS settings.
Impact
They are trying to raise ~25M USD for their product. As I had the access to their DNS and Filesystem, I could've changed the donation address, I could've intercepted the incoming and outgoing emails, I could've accessed thousand peoples KYC documents.
Reaction
The team respond very quickly and was pleased to take my help to identify all the potential threats (I tried my best). Now they are looking to make long-term partnerships with one bug bounty platform to continuously have hundreds of eye on their production application.
How can this be remediated?
We, the bug bounty hunters suffered from a managed platform for bug bounties on our earlier days. Later, services like HackerOne, Cobalt, Bugcrowd and Synack came into force and the scenario changed drastically. In blockchain arena, Hacken is offering a crowdsourced security audit of smart contracts and applications. These services can drastically change the poor scenario around blockchain-sphere. But above all, the companies need to be aware that they lack security. Overconfidence can be very harmful, blockchain is secure but implementation can go wrong. People are trusting countless ICO's and putting their sensitive documents for the sake of KYC. But there is no one to look after the security of those papers. If this situation doesn't change, the future of ICO's will be questioned and identity theft will see another new level!
Courtesy
I used xsshunter.com to test blind XSS. Thanks, Matthew Bryant for developing xsshunter!
Thanks for sharing! This is the reason all ICOs and exchanges should do audits and bug bounties, and Hacken is a great partner to do this.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You are most welcome.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for sharing bhai.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
welcome brother.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Since i joined steemit,this is the most captivating article. KYC is a no for me
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @siddiki! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard!
Participate in the SteemitBoard World Cup Contest!
Collect World Cup badges and win free SBD
Support the Gold Sponsors of the contest: @good-karma and @lukestokes
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @siddiki! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit