
"This Problem Threatens to Destroy the Blockchain and the Cryptocurrencies"
Let's talk a little bit about the current reality in the Blockchain ...
MONDAY, JANUARY 29, 2018
This week dawns with a terrible and devastating news.
"Spectacular theft of 530 million dollars in cryptocurrencies from the Coincheck page of Japan, the largest of all so far"
The news is spread like wildfire by different means of communication. And headlines appear how ...
"Vulnerated Coincheck's security ..."
"The hackers win again ..."
Millions of dollars stolen in cryptocurrencies, and the price of Bitcoin plummets, falling on its knees.
At that time begins an accelerated decline in the price of Bitcoin that falls from approximately 18,800 in December 2017 to $ 11,000 on January 19, 2018. The losses are multimillion-dollar and the panic is widespread, producing nervous sales causing the price to continue falling .
Can we prevent this Pearl Harbor from repeating itself?

MONDAY, FEBRUARY 17, 2018
"Group of 'hackers' steals personal data from more than 100 million people"
The hackers have stolen from the US company Equifax the data of 143 million people that include Social Security numbers, addresses and, in some cases, credit card numbers.
What about security?
Are the hackers smarter?

MONDAY, MAY 28, 2018
"A new cyber attack threatens large companies around the world"
Companies from Ukraine, Russia and Denmark have seen their activity affected and the threat could be extended. It is a new ransomware attack. At the end of May, a cyber attack put global security in check. The hackers hijacked files and asked in exchange for a ransom in bitcoins.

I know what you're thinking…
And maybe you say ... but I do not have millions of dollars, or thousands of Bitcoin for hackers to notice me, nor do I have a big company
Maybe it's true but even so you do not want to miss this news ...
"Citizens are the main objective of the new cyber attacks"
Cyber terrorism has turned cyberspace into its new arena of struggle, with rescue programs, such as 'ramsonware'. Hackers have become sophisticated, becoming a very serious threat.
In 2016, these modern pirates, without a patch or stick leg managed to cheat almost 900 million euros in computer rescue.
And this money was not stolen from large companies, banks or financial institutions, but from ordinary citizens, from people who live on a check every 15th and 30th of every month.
A sample of it are the two global attacks, the one of 'wannacry' and the variant of 'petya', in only one month, this has triggered the alarms.
According to the British security company Sophos, ransomware attacks are on the rise and 2018 will be one of the peak years of this scheme of cyber-extortion.
What will you do, isolate yourself from the world or reinforce your security?
Okay, what can I do?
To answer that question is GOLDILOCK


WHAT IS GOLDILOCK?
"Goldilock is a new type of storage system, which acts as a cold storage until such time as the user needs to access their funds / data."
"When a user needs access to their private data, the physical device that stores their information connects to the Internet and the user is granted limited time access through non-IP technology with secure authentication layers."
Safety first of all
For this reason Goldilock uses a revolutionary digital method of "physical disconnection of the air" that does not require physical equipment.
What is the advantage of this?
Simply that if it is not connected, it can not be hacked, but not satisfied with this Goldilock gives you the fabulous advantage of unlimited access to your data and your money, whenever you want and from wherever you are. And without the need of any physical device.
Currently to use the "cold shutdown"
• The user has to be proficient in this technology, and needs ...
• Acquire a physical device, without which it is impossible to access your accounts or your data
This has the disadvantage that if the mechanism is damaged or lost, the possibility of recovering your data or your accounts disappears
With Goldilock, users would be granted access to their documents by request.
At the time of the request, the data will be temporarily connected to the web and will be delivered to the user through a trigger mechanism that is not IP.
After the user has finished performing their identity verification, the data is again out of line, inaccessible for anyone to see or access them.
Goldilock is maximizing the benefits of cold storage (Security) and hot storage (Availability), incorporating a novel additional physical layer of security previously nonexistent in the market. Our solution interweaves as a web a completely new combination of the most encrypted and secure security layers and protocols, totally unknown by hackers, but best of all, user-friendly, no matter if you are new or advanced.

FLOW OF THE ACTIVATION PROCESS
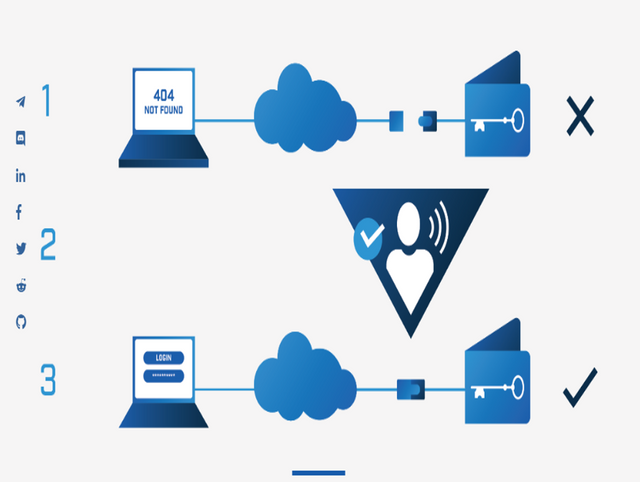
1. Wallet is stored offline in an encrypted data vault, physically disconnected from the Internet.
2. Using a mechanism other than IP, the user activates his wallet by making it accessible through the Internet.
3. The user can securely access his or her wallet through an encrypted connection using a dedicated URL and access credentials.

PENDING TECHNOLOGY OF PATENT
Supported in a framework of proven technologies and innovative processes, Goldilock offers a unique solution for key custody and data storage, which includes:
Disconnection of physical airgap from electronic networks
Dedicated hardware per user to process the storage of encrypted data
Regressive connectivity and non-IP signal processing
Biometric gateways
Device recognition
Personal generated codes
Scalable solutions for segregated physical connectivity
Two-factor authentication
Optional multiple signature security
Secured physical vaults
Backup encrypted data from multiple sites
Secure dashboards and live reports on access and use
Guarantees of third parties fully insured for the extraction and delivery of data to the owners upon request or in case of business interruption

USE CASES
John and his team have just been selected to present a blueprint on software that helps a dairy company improve its performance. His team consists of 12 people and is spread in several cities in the country and in three different countries. Coordinating everyone's work requires total security in communicating and sending data, John has already had a previous bad experience when part of his work was hacked by the network and he does not want to relive this unpleasant and expensive experience.
You wonder how to make your data and codes travel safely through the network.
In this search, he stumbles upon Goldilock, which, with its unique key storage and data storage solution, offers the security of cold storage, without having to invest in additional physical equipment and the connectivity of a wallet.
That way John and his team with the security that Goldilock provides them, are committed to winning their contract, without the stress of being hacked.

Mary is nervous, she has not been able to sleep well for days and her restlessness is affecting her husband William's dream. She is not really sick, her problem is simpler even though she has a certain complication. Surprisingly Mary has turned out to be a good poker player, and she has been participating in some online competitions that pay in cryptocurrencies. She did not expect to do so well in the competition, she did not expect to earn so much money, she plays as a hobby. But there she is, with a few thousand dollars earned in cryptocurrencies, which she must keep until the end of the competition, for which she still needs fifteen days. But it turns out that some of the players have stolen their cryptocurrencies and that is killing Mary's peace of mind, because that money falls very well at that time.
Mary looking for a solution enters an online forum and there she discovers that a platform called Goldilock has launched to the market a great solution for such problems. With no loss of time, she acquires this revolutionary system and to her surprise, she finds that, despite how safe and reliable the system is, it is also easy to manage, even for a newbie like her.
From that day Mary and her husband William go back to sleep deeply.

TOKEN LOCK OF GOLDILOCK
"LOCK is the utility token that will be used to power Goldilock's services."
"The LOCK token will allow account holders to securely approve the sharing of their data and can act as an approval mechanism and custody of transactions between various parties."
"LOCK will also give users a history of the activity of their nodes!"
NEO will be the first blockchain to integrate, and others will do so shortly.

WHY NEO?
"Goldilock chose the NEO network for the LOCK token because of our alignment with their vision and philosophy about the future of blockchain. His focus on Governance and Compliance, Digital Assets, Digital Identity and Intelligent Contracts provides a solid foundation for Goldilock Security Suite. "

IN CONCLUSION
• Goldilock to be able to guarantee the total security of the data and the money saved in the blockchain will change the way people handle their confidential digital data.
• Goldilock combines the best of cold and hot storage, your data is not connected to the network, just as if you had invested in a physical device, but at the same time you can access your data and your money wherever and whenever you want, without restrictions, just by using your personal password.
• One of the biggest drawbacks to the massive adoption of cryptocurrencies is that people usually distrust how secure their money is, the truth is that they needed that special piece that could guarantee that you and only you had access to it, and that is precisely what Goldilock does.
• I insist on the use of "airgap" technology. It gives you the benefit of additional security, by keeping your account data and your personal information out of line, and available only when you want it. But the best thing is that you do not need a physical device to do it, you only need a Goldilock account
• Banks, clinics, insurance companies, universities and other institutions can benefit from the integration of Goldilock technology with their existing systems. Since the system can be used to store private keys for cryptocurrencies, banking and credit information, personal identities, health data, digital media and signature keys, smart contracts or approvals in process.

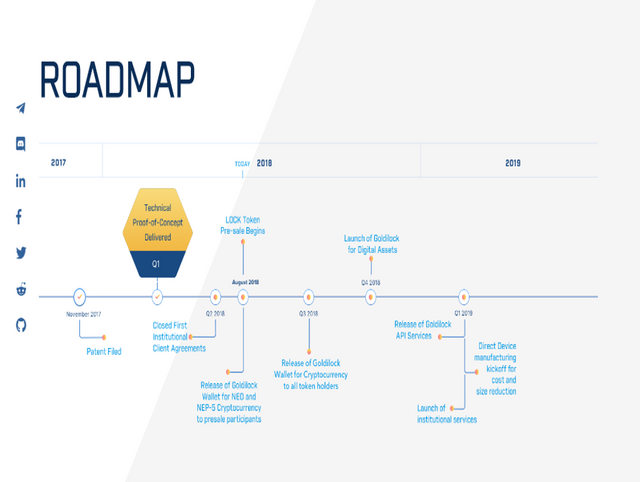
ROADMAP

THE TEAM

ADVISORS
PARTNERS

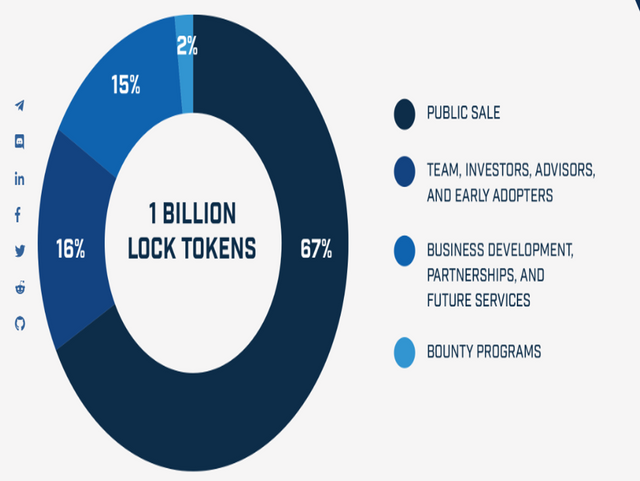
EXTRA INFORMATION OF TOKEN
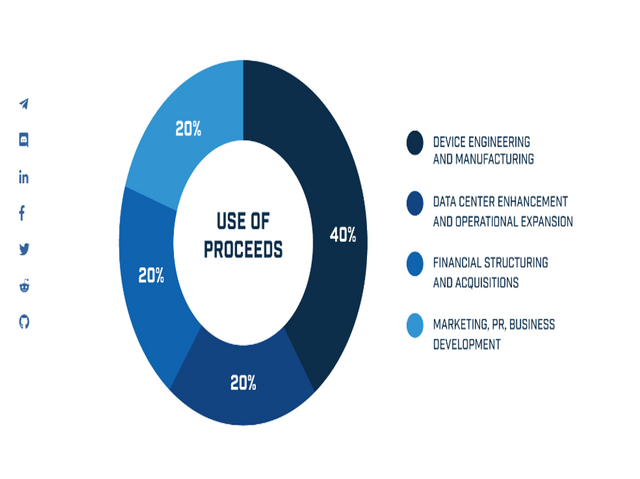
More Information & Resources:
- Goldilock Website
- Goldilock WhitePaper
- Goldilock Tokenomics
- Goldilock Telegram
- Goldilock Discord
- Goldilock Linkedin
- Goldilock Facebook
- Goldilock Twitter
- Goldilock Reddit
- Goldilock Github




Congratulations! This post has been upvoted from the communal account, @minnowsupport, by trituratusmiedos from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit