
Author: Lindsey O'Donnell
White-hat hackers will now have the chance to win $20,000 for sniffing out remote code-execution flaws in industrial control systems.
Industrial control systems (ICS) used to manage critical infrastructure and manufacturing will be the main target in next year’s popular Pwn2Own’s annual hacking competition.
Over the past few years, Pwn2Own – a hacking contest that draws in white-hat hackers looking for fame and fortune through finding bugs in various products – has diversified its threat-hunting surfaces from merely focusing on browsers and operating systems to include new areas, including mobile and IoT devices targets.
Now, the contest is offering more than $250,000 in collective prizes for sniffing out flaws in ICS and associated protocols. The event will take place next year (Jan. 21 to Jan. 23) during the S4 Conference in Miami, according to the Zero Day Initiative, which organizes Pwn2Own.
“As with our other contests, Pwn2Own Miami seeks to harden these platforms by revealing vulnerabilities and providing that research to the vendors,” said Brian Gorenc, in a Monday post. “The goal is always to get these bugs fixed before they’re actively exploited by attackers.”
Pwn2Own Miami offers various prizes for vulnerabilities across five ICS categories, listed out below.
Control server solutions, which provide connectivity, monitoring and control across disparate programmable logic controllers (PLCs), which monitor inputs and outputs and make logic-based decisions for automated systems.
OPC Unified Architecture servers, essentially the “universal translator protocol in the ICS world,” which integrates the functionality behind various OPC Classic specifications into one extensible framework.
DNP3, a set of communications protocols used between various components in ICS systems (the primary protocol in the North American Electric Grid).
Human machine interface (HMI)/operator workstations, which connect machine operator to the various hardware components of the industrial control systems.
Engineering workstation software, which directly communicates and can configure primary control equipment such as PLCs, and also configures role-based mechanisms.
Hackers will have an opportunity to focus on specific equipment to find various vulnerabilities – including unauthenticated crash or denial-of-service flaws, information disclosure glitches and remote code-execution vulnerabilities.
control server pwn2own ICS
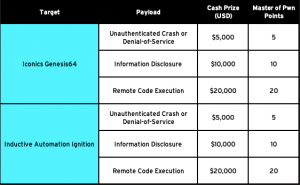
Pwn2Own prizes for control server flaws.
Remote code-execution flaws will have the highest payouts, with prizes of up to $20,000 for finding them in products like the Iconics Genesis64 (a control server) or the Triangle Microworks SCADA data gateway (a DNP3 gateway), for example.
The new focus on ICS may come as no surprise given the continual disclosure of security bugs in the manufacturing, power and water plants, the oil and gas industries – such as recent flaws found in the Delta enteliBUS Manager and the Rockwell Automation industrial drive.
In fact, a recent Kaspersky report found that a full 41.2 percent of industrial control systems were attacked by malicious software at least once in the first half of 2018.
“As the worlds of IT and OT [operational technology] continue to converge, the threats facing critical infrastructure will only increase,” Eitan Goldstein, senior director of strategic initiatives at Tenable told Threatpost. “The expansion of ICS into hacking competitions is a worthwhile initiative. It shows a growing awareness of the exposure gap around ICS and the increasing importance of extending proven security practices into OT environments. It’s also great to see that ICS vendors are willing to engage with the security community on this type of research. It’s important that researchers and vendors continue to work together to secure the systems we all rely on.”
Gorenc said that interested hackers can contact ZDI (via email at [email protected]) to begin the event registration process for the event.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit