First, look at this dumb infographic:
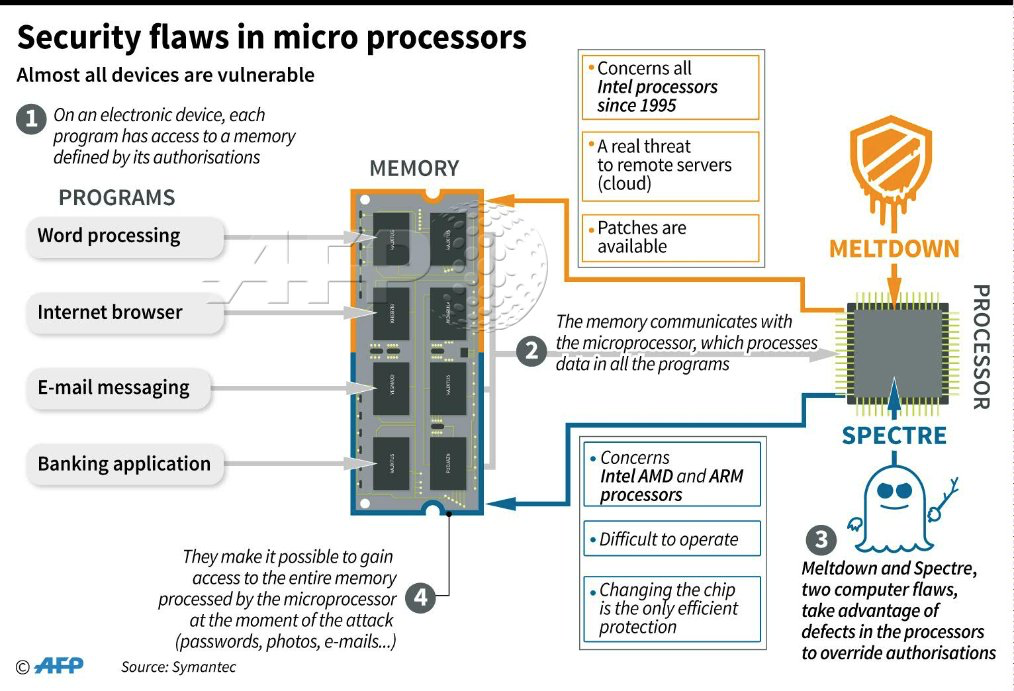
So here's my idea. Spectre can read whatever it wants from memory. So let's give it something to read. Load memory with a bunch of Bitcoin private keys that have zero balance. Know what already does that?
https://github.com/samr7/vanitygen
while (!vcp->vc_halt) {
if (++npoints >= rekey_at) {
vg_exec_context_upgrade_lock(vxcp);
/* Generate a new random private key */
EC_KEY_generate_key(pkey);
.
.
.
}
Vanitygen is a tool for creating a bitcoin vanity address. Say you want an address that starts with 1337h4x0r. Just run vanitygen and let it brute-force an address into existence.
While it's doing that, it'll also created a bunch of garbage for Spectre to trigger on. If it triggers on bitcoin private keys, it'll have hundreds of thousands to sift through at any given time, which will keep it busy for years.
But our CPU itself will get overloaded if we exploit the spectre bug ? Ie assuming that first we exploit - which is very difficult and then we use it to run something like above, our CPU itself will waste CPU cycles ?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
It would be wasteful. But you could also run it with low priority to minimize the impact.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
But then if you are an attacker, you will write your TSR/worm/virus with slightly more priority which will first preempt the first process and still the attack code will be able to run ? Or is it that there is a way to acquire critical section like a lock / semaphore preventing other processes to exploit the issue ? I didn’t really looked deep as CPU architecture was quite scary for me ... could manage only some PIC based RISC assembly 🤓
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You raise a good point. While the malware could ask for more priority, that doesn't prevent vanitygen from creating bogus keys. Just a fewer of them.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
ie, the malware will not be able to get more CPU cycles at any point in time - sounds more like chemo-therapy :-)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
From you accessment of Spectre, stated here, is it that Spectre is have some issues with reading memories, or is it that it sometimes provides false information?
Then how will it trigger these private keys you mentioned?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
No one has identified any exploit that does this yet. I’m just speculating a possible way to mitigate it.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Wow that's really bold, it may become complicated even if it's possible
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Considering intel has a MInix based IME and Now this, I feel it’s something planned ? Like a lawful interception module ? I haven’t came across anything that connects IME and MELTDOWN.... spectre seems to be an entirely different case with the super vetto capacity
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I made your picture better
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Ok, I will say it just for giggles. Is it possible this was all intentional? If so what is the probability that it was intentional? In addition, this sort of thing always makes me wonder if there will be a day when we wake up to find out that China et. al. track every single keystroke we make via hidden backdoors they build in while producing our chips . #conspiracytheory
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Intentional, personally, I doubt it. If they intended to do this, then they really thought ahead on plausible deniability. In order to trigger this exploit, you have to train the CPU to act up first. It just smells like a normal oversight to me.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Well, that is super boring and therefore probably correct. I still think China knows our every keystroke :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
i think its a grate post...i learn many think from your post...and i waiting for your next post...keep it up
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
That's really smart......loading an empty balance bitcoin private keys...so, with the aid of this Vanitygen spectre is going to be prevented by giving it some trash to work on and therefore help to prevent necessary information.....i think that is really smart.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
and the networks these processors comes with are so entirely different and amazing..thanks for your elaboration @inertia ...am glad this never skipped my notice
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
our CPU itself will get destroyed if we exploit the spectre bug ? Iet consider that first we exploit - which is very hard and then we use it to run something like above.
we can also try this code:
while (!vcp->vc_halt) {
if (--npoints >= rekey_at) {
else(++npoints>=rekey_at) {
vg_exec_context_upgrade_lock(vxcp);
/* Generate a new random private key */
EC_KEY_generate_key(pkey);
.
.
.
}
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
deleted
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
That's a great news of intel...thanks a lot for sharing intel information ..Carry on your activity....
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
great circuit design...
a microprocessor is made many works...
a computer most important processor...
nice post
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I will try it, crome support it?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
What an evil thing to do! But I can't see anyone actually doing this haha
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hello @inertia!
I apologize for what I write in this post.
I wrote a comment for your post, but probably due to the age of the post you don't saw my comment. Please have a look here.
Thanks!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Related to all this fuzz built around the discovered vulnerabilities (probably known by the manufacturers, but leaked only recent) AMD declares that its Ryzen processors have “an artificial intelligence neural network that learns to predict what future pathway an application will take based on past runs” [3, 5], implying even more complex speculative behavior. "
As a result, while the stop-gap countermeasures may help limit practical exploits in the short term, there is currently no way to know whether a particular code construction is, or is not, safe across today’s processors – much less future designs.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
They say it's a neural network, but it's probably just a sophisticated heuristic, not true AI.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I like your idea. Here's hoping the new CPU's coming out over the next few years will not have the Spectre issue. Are there any newer AMD cpu's that don't have the issue or is it all completely screwed?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Flagged for disagreement on rewards.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit