Preamble:
According to CISCO, by 2020 there will be more than 6.58 devices connected to each person. If Smart Hardware brings more convenience to our daily lives it also increases our security awareness and privacy protection concerns. Vendors solving these challenges will be best placed for mass adoption.
Current centralised applications have high-severity vulnerabilities
In recent years, there have been a number of serious IoT security incidents all over the world:
● In 2008, a 14-year-old Polish teenager controlled the tram system in Łódź, Poland’s third-largest city, with a modified TV remote control, resulting in the derailment of several trains and injuries.
● In 2010, a former employee remotely invaded the computer systems of car dealers in Austin, Texas, and a large number of customers complained of vehicle breakdowns.
● In 2013, the United States well-known hacker Samy Kamkar issued a video on Youtube, showing how he used a technology called SkyJack to enable a basic civilian drone to be positioned and controlled to fly nearby. The drones formed a “zombie drone team” controlled only by a smartphone.
● In 2014, 360 security researchers discovered a design flaw in the Tesla Model S automotive application that could allow an attacker to remotely control the vehicle.
● In 2015, HackPWN security experts demonstrated the use of BYD cloud service vulnerabilities to open doors, start cars, and open the trunk of BYD autos.
● In October 2016, a very large-scale DDoS (Distributed Denial of Service attack, which occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers) raided more than half of the U.S. Internet from East Coast to West Coast. Internet services in the U.S. almost went down, including Twitter, Tumblr, Netflix, Amazon, Shopify, Reddit, Airbnb, PayPal and Yelp. The hackers who launched this cyber attack used a “botnet network” consisting of 1.5 million devices. Most of these devices were webcams produced by China DAHUA.
With the popularity and large-scale application of the IoT, those vulnerabilities cannot be ignored. Currently, IoT devices are controlled under centralized networks which have very high security requirements for central servers, and the security vulnerabilities of IoT nodes will affect the whole network. Applying Blockchain technology to the IoT can solve the existing security problems.
INT and Blockchain technology
Blockchain is a decentralized distributed network ledger system. It is based on a trusted and absolutely secure model. With the cooperation of the encryption algorithm, the transaction information will be publicly recorded in the blockchain system in the order of time of occurrence, and the corresponding timestamp will be included. The key point is that these digital “blocks” can only be updated through the unanimous consent of all the people involved in the transaction. So the attacker cannot illegally operate through data interception, modification, and deletion.
Many projects are attempting to solve the IoT security problems through Blockchain technology, such as INT.
INT will filter the intent through the innovative BPK algorithm, and ensure the user’s security.
Traditional DPoS consensus algorithms have started evolving towards the direction of centralization while deviating from blockchain’s original intention of decentralization. Therefore, INT pragmatically created a new consensus algorithm called Double Chain Consensus Algorithm on the base of deep understanding into the core of DPoS consensus algorithm and on the basis of INT chain’s real application scenarios as well as current development status of the IoT devices. The basic architecture is shown in the following diagram:
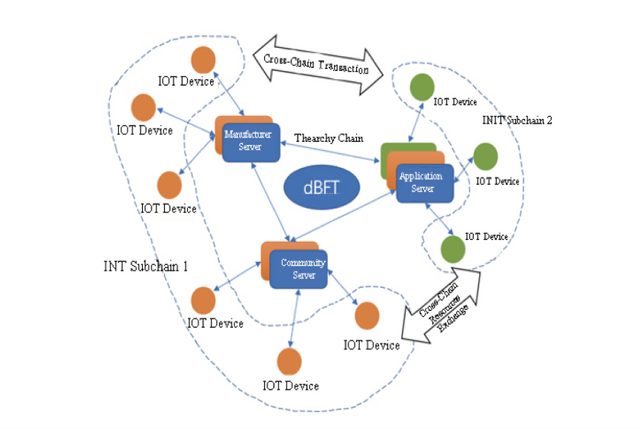
Blockchain technology has the potential to solve the security concerns around the IoT and protect its users. Whether it is protecting data privacy or using encryption algorithms and consensus mechanisms to prevent DDoS attacks on IoT devices, Blockchain technology can play a key role in recording and verifying our transaction behaviour.