Horizons Week 4:
Web App Authentication and Further Crypto Adventures

A very busy, yet exciting week. I have structured this article the same way as the previous three:
- What I Learned
- What I Ate
- What I Did
In case you are a week or two behind in this Chronicle of My SF Coding Bootcamp Adventures, here are links to the previous week's articles:
What I Learned
Authentication, Security, and Better Servers
Passport:

Initially, we dealt with login and user details ourselves. Unfortunately, that is cumbersome and generally insecure. So, we integrated PassportJs into our web applications this week. Passport essentially handles all the login details for us; all we have to do is install the package, define our login strategy, define the serialization and deserialization functions, and initialize passport. Then, Passport does the rest for us. Really cool!
Local: the first of Passport's two authentication schemes is "local." Local allows us, the developer, to write our own login strategy. This works well if you just want a simple username and password login.
OAuth: However, if you want to take advantage of 3rd party login strategies, you can use trusted third parties through OAuth... this is basically Facebook login, something used by MANY, MANY applications today. OAUTH makes our lives easier because now, not only do we not have to deal with user details and sessions, we don't even have to write our own login strategy. It's as if all the work is done for us.
Secure passwords: we upgraded from plain text passwords to salted and hashed passwords this week. One small step for man, one huge step for newbie full stack developers.
Basic security issues: during Wednesday this week we dealt with common security issues:
- Client Side vs. Server Side: any aurthentication done on the client side is very dangerous... you are relying on the client to protect himself/herself. In today's world, the average user is a) not too concerned with protecting himself/herself and b) not aware of what it takes to protect himself/herself. So, as programmers, we are responsible to doing what we can top protect our users. One easy way to do this is to rely as little as possible on the client. So, we move as much authentication as we can to the server.
- XSS: XSS stands for cross site scripting. If you aren't careful, someone may inject JS into your website and cause some serious damage. We learned some basic safety precautions against this.
- CSRF: Cross site request forgery is when someone forces someone else to run an action they don't want to run. These don't result in data loss, but undesired action. Ex) Bob forces Alice to send him $10, but Bob does not know/steal Alice's financial info. Often this is done with some clever social engineering, tricking users to click on a link that may steal their cookies (and thus their online identity for all the sites they are logged into).
Webhooks:
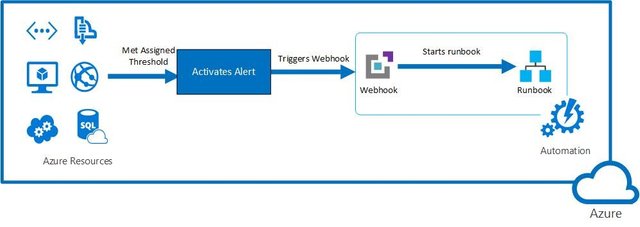
Put very simply, 3rd party calls to your server. Say you want Twilio to send SMS messages to you, well then setup a route that handles that call and let Twilio know what route to use. Thus, every time Twilio receives a text, it will make a call to a specific route on your server and your server will act upon that request.
What I Ate

If you haven't heard of MealPal and you live in a large city, you're truly missing out. Check them out here and if you signup we both get a $50 Amazon gift card: https://secure.mealpal.com/signup?invite=6ljASSK22CgIVRJ-.
MONDAY: Tu Lan

Link:https://www.yelp.com/biz/t%C3%BA-lan-san-francisco-4
TUESDAY: Dinosaur's Vietnamese Sandwiches

Link: https://www.yelp.com/biz/dinosaurs-vietnamese-sandwiches-san-francisco-3
WEDNESDAY: Publico Urban Taqueria

Link: https://www.yelp.com/biz/publico-urban-taqueria-san-francisco-3
ThURSDAY: Elmira Rosticceria

Link: http://www.elmirasf.com/
FRIDAY: Mathilde's French Bistro

Link: https://www.mathildesf.com/
What I Did
SF Ethereum Meetup at Reddit: Storj, Rakugo, and Curio Cards:

A nice detour from the usual talk of Plasma, the Raiden Network, and sharding, this week SF Ethereum brought in Storj, Rakugo, and Curio Cards. The three offered very different blockchain use cases, but ultimately they shared a common theme: content on the blockchain.
Storj: Storj has been around for quite a while, and in fact are the only project to do 2 ICO's. They are a decentralized storage company and have successfully migrated from Bitcoin to Ethereum. Sean Wilkinson, their founder, spoke like a Blockchain veteran, quick to dismiss certain recent events as anything too unique and was always quick to bring up Bitcoin's past. It was a very reassuring point of view, one that was more "we have something here, let's see it play out" than "this is the best thing every, X blockchain is going to the moon, it you blink you'll miss it."
Rakugo: honestly, not 100% what these guys offer. They started with a sort of content creator talent matchup community and then went into making abstract smart contracts. Personally, I think the abstract smart contracts sounds pretty cool. A few weeks ago Ethereum standardized ERC20 tokens, so these guys aren't too far off the mark... unfortunately though, standardization needs to build off a successful base implementation. As Ethereum undergoes changes for Metropolis and people continue to experiment with this new technology, I don't believe we will come across that standard, basic successful contract any time soon.
Curio Card: these guys seek to take art and make it a rare, digital asset. I'll admit, this seemed cool, but I could not understand the use. They basically create these tokens that represent these cards and then only release a certain number of them. I guess the idea is that they are tradable and collectable, but I'm not sure I'd ever want one.
Reddit HQ: an outstanding venue. Would love to work there.
Made Progress Planning SF Ethereum Meetup!

It may be early, but here are a few details about the upcoming meetup:
Location: we are looking into a venue that will allow 100+ people ( the biggest Steemit meetup outside of SteemFest?????)
Date: we are looking at October 16th
Event: we are in the talks of possibly having a certain Steemit founder come and speak. This may or may not be a really cool event because a certain paper detailing certain tokens by the name of SMT may have just been released. But, these are all maybe's :)
AND LAST BUT NOT LEAST a very good reason to show up is to see me in the coolest (possibly tackiest) Steemit shirt ever:

Just ordered it from @thesteemitshop
Conclusion
I hope everyone had a great week last week. AGAIN, if you're in SF during October (or ever, message me @cryptorob on Steemit.Chat). I would love to meetup and chat crypto!
Have a wonderful Monday, Cheers and Steem on!
Damn, dude! Looks like you've been staying out there and staying busy! Gettin' it done!
You ever thought about starting an EOS meetup? They're calling for 'em right now if you're interested in something like that. If so, check the resources page out: https://eos.io/resources/
Also, side note, I may be in SF in the next few months so I might just hit you up! My cousin lives there working for Cisco/Meraki.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I did think about the EOS meetup... but I've been trying very hard not to over commit this time around LOL
Definitely lmk if you're ever in SF. Could show you a good time here!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
just a small addition, since I am here:
voilà
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Very true, thanks for pointing out my error!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit