Mining is the process of algorithmic operations, from the point of view of computers and codes, is the repeated execution of Hash functions and the specific process of testing the execution results. Like the discussion of algorithms, mining is also discussed under the premise of using the POW consensus mechanism.
We have been very clear that mining is from the beginning of CPU mining, to GPU mining, and finally evolved to the current ASIC(professional mining machine) mining era, this article analyzes the logic design and technical implementation.
The evolution of mining is the evolution process of hardware, but also the evolution process of software, especially the improvement process of hardware and software docking protocol, so this paper directly takes several core protocols related to mining as subheadings and in-depth discussion step by step.
When reviewing the article, it was found that the word "Miner" was used in a vague way, which is similar in English literature. In daily communication, it generally refers to people who have mining machines. This paper focuses on blockchain, and mining procedures or machines are collectively referred to as miners.
MINING
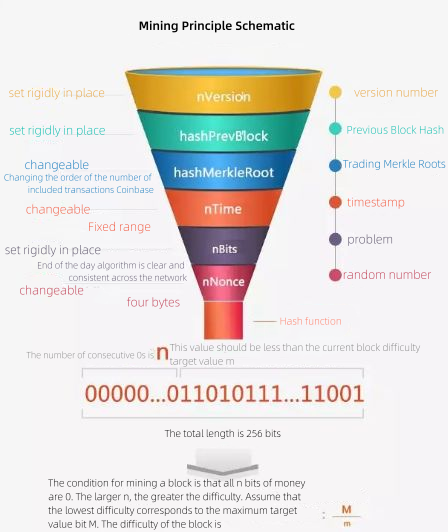
This section discusses the mining principle, first analyzes the Bitcoin Blockheader structure, we say that mining is essentially the process of executing the Hash function, and the Hash function is a single input single output function, the input data is the block header. There are 6 fields in the Bitcoin block header:
int32_t nVersion; // Version number, 4 bytes
uint256 hashPrevBlock; // hash value of the block header of the previous block, 32 bytes
uint256 hashMerkleRoot; // Contains the Merkle root of all transactions constructed into this block, 32 bytes
uint32_t nTime; //Unix timestamp, 4 bytes
uint32_t nBits; // Record the block difficulty, 4 bytes
uint32_t nNonce; // Random number, 4 bytes
As mentioned above, each bitcoin mining is to perform two SHA256 operations (SHA256D) on these 80 bytes consecutively, and the result is a fixed 32 bytes (binary 256 bits).
The above six fields are different,
nVersion, the block version number, can only be changed when upgrading.
hashPrevBlock, determined by the previous block.
nBits, determined by the whole network, are adjusted every 2016 blocks, and the adjustment algorithm is fixed.
Therefore, the above three fields can be understood as fixed, which is the same for each miner. Where miners are free to adjust are the remaining three fields,
nNonce, provides 2^32 possible values
In fact, the value space that this field can provide is very limited, because there is a reasonable block time range, this range is determined according to the previous block time, too early or too early than the previous block time will be rejected by other nodes.
It is worth mentioning that the block time of the latter block is slightly earlier than the previous block time, which is allowed. Generally, miners use the machine's current time stamp directly.
hashMerkleRoot, which theoretically offers 2^256 possibilities, changes to this field come from adding or deleting transactions included in the block, changing the order, or modifying the input fields of Coinbase transactions.
According to the Hash function feature, the change of any one bit in the three fields will result in a great change in the Hash result. In the era of CPU mining, the search space was mainly provided by nNonce. In the era of mining machines, the 4 bytes provided by nNonce were far from enough, and the search space turned to hashMerkleRoot.
Mining is the process of algorithmic operations, from the point of view of computers and codes, is the repeated execution of Hash functions and the specific process of testing the execution results. Like the discussion of algorithms, mining is also discussed under the premise of using the POW consensus mechanism.
We have been very clear that mining is from the beginning of CPU mining, to GPU mining, and finally evolved to the current ASIC(professional mining machine) mining era, this article analyzes the logic design and technical implementation.
The evolution of mining is the evolution process of hardware, but also the evolution process of software, especially the improvement process of hardware and software docking protocol, so this paper directly takes several core protocols related to mining as subheadings and in-depth discussion step by step.
When reviewing the article, it was found that the word "Miner" was used in a vague way, which is similar in English literature. In daily communication, it generally refers to people who have mining machines. This paper focuses on blockchain, and mining procedures or machines are collectively referred to as miners.
MINING
This section discusses the mining principle, first analyzes the Bitcoin Blockheader structure, we say that mining is essentially the process of executing the Hash function, and the Hash function is a single input single output function, the input data is the block header. There are 6 fields in the Bitcoin block header:
int32_t nVersion; // Version number, 4 bytes
uint256 hashPrevBlock; // hash value of the block header of the previous block, 32 bytes
uint256 hashMerkleRoot; // Contains the Merkle root of all transactions constructed into this block, 32 bytes
uint32_t nTime; //Unix timestamp, 4 bytes
uint32_t nBits; // Record the block difficulty, 4 bytes
uint32_t nNonce; // Random number, 4 bytes
As mentioned above, each bitcoin mining is to perform two SHA256 operations (SHA256D) on these 80 bytes consecutively, and the result is a fixed 32 bytes (binary 256 bits).
The above six fields are different,
nVersion, the block version number, can only be changed when upgrading.
hashPrevBlock, determined by the previous block.
nBits, determined by the whole network, are adjusted every 2016 blocks, and the adjustment algorithm is fixed.
Therefore, the above three fields can be understood as fixed, which is the same for each miner. Where miners are free to adjust are the remaining three fields,
nNonce, provides 2^32 possible values
In fact, the value space that this field can provide is very limited, because there is a reasonable block time range, this range is determined according to the previous block time, too early or too early than the previous block time will be rejected by other nodes.
It is worth mentioning that the block time of the latter block is slightly earlier than the previous block time, which is allowed. Generally, miners use the machine's current time stamp directly.
hashMerkleRoot, which theoretically offers 2^256 possibilities, changes to this field come from adding or deleting transactions included in the block, changing the order, or modifying the input fields of Coinbase transactions.
According to the Hash function feature, the change of any one bit in the three fields will result in a great change in the Hash result. In the era of CPU mining, the search space was mainly provided by nNonce. In the era of mining machines, the 4 bytes provided by nNonce were far from enough, and the search space turned to hashMerkleRoot.
Mining is the process of algorithmic operations, from the point of view of computers and codes, is the repeated execution of Hash functions and the specific process of testing the execution results. Like the discussion of algorithms, mining is also discussed under the premise of using the POW consensus mechanism.
We have been very clear that mining is from the beginning of CPU mining, to GPU mining, and finally evolved to the current ASIC(professional mining machine) mining era, this article analyzes the logic design and technical implementation.
The evolution of mining is the evolution process of hardware, but also the evolution process of software, especially the improvement process of hardware and software docking protocol, so this paper directly takes several core protocols related to mining as subheadings and in-depth discussion step by step.
When reviewing the article, it was found that the word "Miner" was used in a vague way, which is similar in English literature. In daily communication, it generally refers to people who have mining machines. This paper focuses on blockchain, and mining procedures or machines are collectively referred to as miners.
MINING
This section discusses the mining principle, first analyzes the Bitcoin Blockheader structure, we say that mining is essentially the process of executing the Hash function, and the Hash function is a single input single output function, the input data is the block header. There are 6 fields in the Bitcoin block header:
int32_t nVersion; // Version number, 4 bytes
uint256 hashPrevBlock; // hash value of the block header of the previous block, 32 bytes
uint256 hashMerkleRoot; // Contains the Merkle root of all transactions constructed into this block, 32 bytes
uint32_t nTime; //Unix timestamp, 4 bytes
uint32_t nBits; // Record the block difficulty, 4 bytes
uint32_t nNonce; // Random number, 4 bytes
As mentioned above, each bitcoin mining is to perform two SHA256 operations (SHA256D) on these 80 bytes consecutively, and the result is a fixed 32 bytes (binary 256 bits).
The above six fields are different,
nVersion, the block version number, can only be changed when upgrading.
hashPrevBlock, determined by the previous block.
nBits, determined by the whole network, are adjusted every 2016 blocks, and the adjustment algorithm is fixed.
Therefore, the above three fields can be understood as fixed, which is the same for each miner. Where miners are free to adjust are the remaining three fields,
nNonce, provides 2^32 possible values
In fact, the value space that this field can provide is very limited, because there is a reasonable block time range, this range is determined according to the previous block time, too early or too early than the previous block time will be rejected by other nodes.
It is worth mentioning that the block time of the latter block is slightly earlier than the previous block time, which is allowed. Generally, miners use the machine's current time stamp directly.
hashMerkleRoot, which theoretically offers 2^256 possibilities, changes to this field come from adding or deleting transactions included in the block, changing the order, or modifying the input fields of Coinbase transactions.
According to the Hash function feature, the change of any one bit in the three fields will result in a great change in the Hash result. In the era of CPU mining, the search space was mainly provided by nNonce. In the era of mining machines, the 4 bytes provided by nNonce were far from enough, and the search space turned to hashMerkleRoot.
Mining is the process of algorithmic operations, from the point of view of computers and codes, is the repeated execution of Hash functions and the specific process of testing the execution results. Like the discussion of algorithms, mining is also discussed under the premise of using the POW consensus mechanism.
We have been very clear that mining is from the beginning of CPU mining, to GPU mining, and finally evolved to the current ASIC(professional mining machine) mining era, this article analyzes the logic design and technical implementation.
The evolution of mining is the evolution process of hardware, but also the evolution process of software, especially the improvement process of hardware and software docking protocol, so this paper directly takes several core protocols related to mining as subheadings and in-depth discussion step by step.
When reviewing the article, it was found that the word "Miner" was used in a vague way, which is similar in English literature. In daily communication, it generally refers to people who have mining machines. This paper focuses on blockchain, and mining procedures or machines are collectively referred to as miners.
MINING
This section discusses the mining principle, first analyzes the Bitcoin Blockheader structure, we say that mining is essentially the process of executing the Hash function, and the Hash function is a single input single output function, the input data is the block header. There are 6 fields in the Bitcoin block header:
int32_t nVersion; // Version number, 4 bytes
uint256 hashPrevBlock; // hash value of the block header of the previous block, 32 bytes
uint256 hashMerkleRoot; // Contains the Merkle root of all transactions constructed into this block, 32 bytes
uint32_t nTime; //Unix timestamp, 4 bytes
uint32_t nBits; // Record the block difficulty, 4 bytes
uint32_t nNonce; // Random number, 4 bytes
As mentioned above, each bitcoin mining is to perform two SHA256 operations (SHA256D) on these 80 bytes consecutively, and the result is a fixed 32 bytes (binary 256 bits).
The above six fields are different,
nVersion, the block version number, can only be changed when upgrading.
hashPrevBlock, determined by the previous block.
nBits, determined by the whole network, are adjusted every 2016 blocks, and the adjustment algorithm is fixed.
Therefore, the above three fields can be understood as fixed, which is the same for each miner. Where miners are free to adjust are the remaining three fields,
nNonce, provides 2^32 possible values
In fact, the value space that this field can provide is very limited, because there is a reasonable block time range, this range is determined according to the previous block time, too early or too early than the previous block time will be rejected by other nodes.
It is worth mentioning that the block time of the latter block is slightly earlier than the previous block time, which is allowed. Generally, miners use the machine's current time stamp directly.
hashMerkleRoot, which theoretically offers 2^256 possibilities, changes to this field come from adding or deleting transactions included in the block, changing the order, or modifying the input fields of Coinbase transactions.
According to the Hash function feature, the change of any one bit in the three fields will result in a great change in the Hash result. In the era of CPU mining, the search space was mainly provided by nNonce. In the era of mining machines, the 4 bytes provided by nNonce were far from enough, and the search space turned to hashMerkleRoot.
Mining is the process of algorithmic operations, from the point of view of computers and codes, is the repeated execution of Hash functions and the specific process of testing the execution results. Like the discussion of algorithms, mining is also discussed under the premise of using the POW consensus mechanism.
We have been very clear that mining is from the beginning of CPU mining, to GPU mining, and finally evolved to the current ASIC(professional mining machine) mining era, this article analyzes the logic design and technical implementation.
The evolution of mining is the evolution process of hardware, but also the evolution process of software, especially the improvement process of hardware and software docking protocol, so this paper directly takes several core protocols related to mining as subheadings and in-depth discussion step by step.
When reviewing the article, it was found that the word "Miner" was used in a vague way, which is similar in English literature. In daily communication, it generally refers to people who have mining machines. This paper focuses on blockchain, and mining procedures or machines are collectively referred to as miners.
MINING
This section discusses the mining principle, first analyzes the Bitcoin Blockheader structure, we say that mining is essentially the process of executing the Hash function, and the Hash function is a single input single output function, the input data is the block header. There are 6 fields in the Bitcoin block header:
int32_t nVersion; // Version number, 4 bytes
uint256 hashPrevBlock; // hash value of the block header of the previous block, 32 bytes
uint256 hashMerkleRoot; // Contains the Merkle root of all transactions constructed into this block, 32 bytes
uint32_t nTime; //Unix timestamp, 4 bytes
uint32_t nBits; // Record the block difficulty, 4 bytes
uint32_t nNonce; // Random number, 4 bytes
As mentioned above, each bitcoin mining is to perform two SHA256 operations (SHA256D) on these 80 bytes consecutively, and the result is a fixed 32 bytes (binary 256 bits).
The above six fields are different,
nVersion, the block version number, can only be changed when upgrading.
hashPrevBlock, determined by the previous block.
nBits, determined by the whole network, are adjusted every 2016 blocks, and the adjustment algorithm is fixed.
Therefore, the above three fields can be understood as fixed, which is the same for each miner. Where miners are free to adjust are the remaining three fields,
nNonce, provides 2^32 possible values
In fact, the value space that this field can provide is very limited, because there is a reasonable block time range, this range is determined according to the previous block time, too early or too early than the previous block time will be rejected by other nodes.
It is worth mentioning that the block time of the latter block is slightly earlier than the previous block time, which is allowed. Generally, miners use the machine's current time stamp directly.
hashMerkleRoot, which theoretically offers 2^256 possibilities, changes to this field come from adding or deleting transactions included in the block, changing the order, or modifying the input fields of Coinbase transactions.
According to the Hash function feature, the change of any one bit in the three fields will result in a great change in the Hash result. In the era of CPU mining, the search space was mainly provided by nNonce. In the era of mining machines, the 4 bytes provided by nNonce were far from enough, and the search space turned to hashMerkleRoot.
Mining is the process of algorithmic operations, from the point of view of computers and codes, is the repeated execution of Hash functions and the specific process of testing the execution results. Like the discussion of algorithms, mining is also discussed under the premise of using the POW consensus mechanism.
We have been very clear that mining is from the beginning of CPU mining, to GPU mining, and finally evolved to the current ASIC(professional mining machine) mining era, this article analyzes the logic design and technical implementation.
The evolution of mining is the evolution process of hardware, but also the evolution process of software, especially the improvement process of hardware and software docking protocol, so this paper directly takes several core protocols related to mining as subheadings and in-depth discussion step by step.
When reviewing the article, it was found that the word "Miner" was used in a vague way, which is similar in English literature. In daily communication, it generally refers to people who have mining machines. This paper focuses on blockchain, and mining procedures or machines are collectively referred to as miners.
MINING
This section discusses the mining principle, first analyzes the Bitcoin Blockheader structure, we say that mining is essentially the process of executing the Hash function, and the Hash function is a single input single output function, the input data is the block header. There are 6 fields in the Bitcoin block header:
int32_t nVersion; // Version number, 4 bytes
uint256 hashPrevBlock; // hash value of the block header of the previous block, 32 bytes
uint256 hashMerkleRoot; // Contains the Merkle root of all transactions constructed into this block, 32 bytes
uint32_t nTime; //Unix timestamp, 4 bytes
uint32_t nBits; // Record the block difficulty, 4 bytes
uint32_t nNonce; // Random number, 4 bytes
As mentioned above, each bitcoin mining is to perform two SHA256 operations (SHA256D) on these 80 bytes consecutively, and the result is a fixed 32 bytes (binary 256 bits).
The above six fields are different,
nVersion, the block version number, can only be changed when upgrading.
hashPrevBlock, determined by the previous block.
nBits, determined by the whole network, are adjusted every 2016 blocks, and the adjustment algorithm is fixed.
Therefore, the above three fields can be understood as fixed, which is the same for each miner. Where miners are free to adjust are the remaining three fields,
nNonce, provides 2^32 possible values
In fact, the value space that this field can provide is very limited, because there is a reasonable block time range, this range is determined according to the previous block time, too early or too early than the previous block time will be rejected by other nodes.
It is worth mentioning that the block time of the latter block is slightly earlier than the previous block time, which is allowed. Generally, miners use the machine's current time stamp directly.
hashMerkleRoot, which theoretically offers 2^256 possibilities, changes to this field come from adding or deleting transactions included in the block, changing the order, or modifying the input fields of Coinbase transactions.
According to the Hash function feature, the change of any one bit in the three fields will result in a great change in the Hash result. In the era of CPU mining, the search space was mainly provided by nNonce. In the era of mining machines, the 4 bytes provided by nNonce were far from enough, and the search space turned to hashMerkleRoot.