Grant West, a 25-year-old UK man, has pleaded guilty to stealing customer details from 17 major websites and reselling the information on the darknet. He admitted attacking Uber, T-Mobile, Groupon, Vitality, Coral Betting, AO.com, the British Cardiovascular Society, Mighty Deals Limited, Truly Experiences Ltd, Ladbrokes, Asda, Argos, Nectar, M R Porter, RS Feva Class Association 2017, Just Eat, and Sainsburys. Cybercrime investigators alleged that West used bruteforce to access website login forms and then sold the harvested credentials on the darknet as “fullz.”
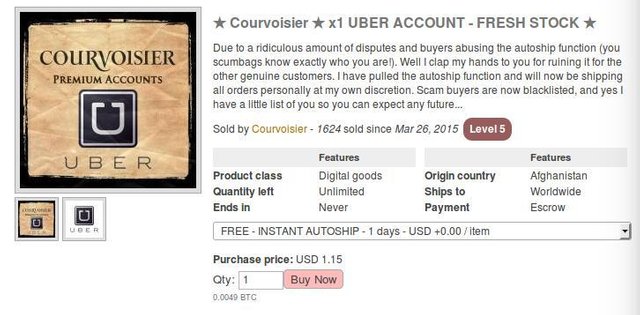
At Southwark Crown Court, West pleaded guilty to conspiracy to defraud the online food and delivery service, Just Eat, between July and December 2015. Investigators accused West of stealing the credentials and user information of 165,000 Just Eat customers. After his arrest for the Just Eat attacks, West continued to attack websites and steal user data. He sold the “fullz” on the darknet under the username “Courvoisier.” Investigators accused the 25-year-old of selling marijuana on the darknet shop, as well as user credentials and “fullz.”
In 2016, during a raid on West’s house, police found the drugs he had been accused of selling on the darknet, along with roughly $33,000. He had earned that money, the court believes, through selling both marijuana and “fullz” online. “Fullz” is a slang term for “full credentials.” It often refers to, instead of simply a username and password, a much larger set of stolen information. This includes usernames, passwords, emails, DOBs, names, and sometimes Social Security Numbers or a country’s equivalent.
West, at Southwark Crown Court in early December, pleaded guilty to two counts of conspiracy to defraud and one computer hacking charge. He also pleaded guilty to four counts of the possession and the supply of marijuana, one count of money laundering (via Bitcoin), and two counts of possessing criminal property.
A spokesperson for Just Eat spoke to the press following completion of the hearing. “We were made aware of a phishing scam which took place in 2015 and at the time took steps to mitigate this, he said. “This particular attack affected both Just Eat customers and non-customers. At no point were Just Eat systems compromised or breached.” According to the spokesperson, Just Eat has a dedicated infosec team to protect user information. West allegedly caused $266,000 in damages to Just Eat, even though he did not manage to steal any financial information.
Judge Joanna Korner QC will sentence West at an unknown date in the future, but until then, West will remain in custody.