
Foundation
From my own examination, the worm seems to spread with no novel adventure. Contaminated gadgets essentially scan for different hosts with open port 5555/tcp and recognize if the Android Investigate Extension (ADB) daemon is tuning in behind the port. On the off chance that the port is open and an ADB daemon is tuning in, the worm will endeavor to pick up a superuser charge line interface (a root shell) on the gadget and, on the off chance that it is fruitful, duplicates its documents to the defenseless framework.
This root shell gives for all intents and purposes boundless access to the gadget's working framework to the remote aggressor. That incorporates, yet isn't restricted to, introducing unsigned Android programming bundles, taking screen captures and live accounts of the gadget's screen and some other ADB capacities.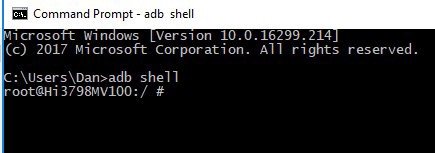
Once the gadget is contaminated, the worm introduces various projects which start mining the Monero cryptographic money, co-picking 98– 99% of the gadget's CPU assets for the undertaking. Utilizing its system get to, the traded off gadget likewise starts checking for and bargaining other helpless gadgets.
The Defenselessness
Up until this point, NetLab has not discharged particular data about what gadgets are powerless, however in light of my constrained research most, if not all, of the contaminated gadgets are Huawei Hi3798MV100 IPTV set-top boxes, display EC6108V9, running a conveyance of the Android 4.4.2 (KitKat) working framework. Android-shrewd clients will take note of that, regularly, associating with an Android gadget by means of the troubleshoot daemon triggers a notice to the client before conceding access, as portrayed by Google here: When you interface a gadget running Android 4.2.2 or higher, the framework demonstrates an exchange requesting that whether acknowledge a RSA key that permits troubleshooting through this PC. This security component ensures client gadgets since it guarantees that USB troubleshooting and other adb commands can't be executed unless you're ready to open the gadget and recognize the discourse.
On account of these powerless Huawei IPTVs, this isn't going on. Anybody can clandestinely interface with one of these defenseless gadgets and pick up root access without contribution from the end-client. Since at any rate January 2016, an adventure has been freely accessible to exploit this situation utilizing Metasploit, an infiltration testing system created by Rapid7, alongside an expansive gathering of open-source givers.
Subsequent to checking on the filesystem of a tainted gadget, I discovered executable doubles named droidbot, sss and nohup. Additionally present is droidbot.apk, which is introduced onto the tainted Android framework by means of the nearby Android Bundle Administrator, pm. Once introduced, the APK is referenced as com.android.good.miner and incorporates the JavaScript Monero digger, CoinHive. An Android WebView is incorporated into "good.miner", with JavaScript empowered, alongside a few scrambled SQLite databases. The databases have all the earmarks of being encoded utilizing the AES figure with a 256-piece key length.
The dominant part of CPU use on a contaminated framework gives off an impression of being originating from droidbot, which is using about all accessible CPU assets on the gadget consistently. Additionally incorporated into the/information/nearby/tmp registry are two more Monero mining executables: xmrig32 and xmrig64. Since this assault has all the earmarks of being focusing on 32-bit ARM frameworks, it is obscure why one would likewise incorporate the 64-bit xmrig double or two totally unique mining techniques (CoinHive and xmrig) on similar gadgets.
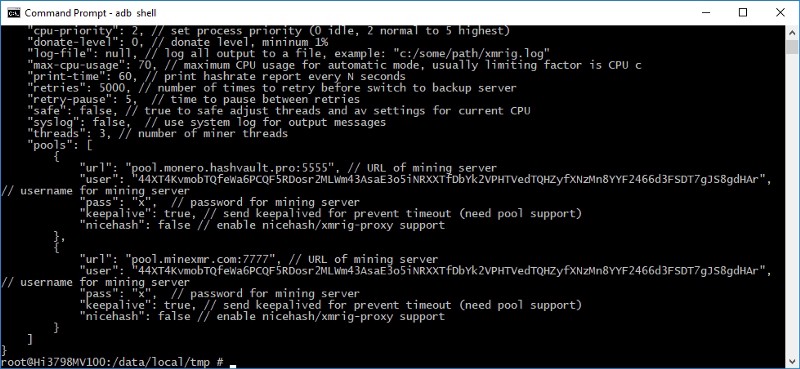 The attacker's minning configurations
The attacker's minning configurations
MY ADVICE TO READERS
At the present, the best proposals I can give is to guarantee shrewd TVs and spilling gadgets are legitimately firewalled and to debilitate ADB on advanced mobile phones and other Android-fueled gadgets. At the point when associated with the cell arrange or the web, an open ADB port can turn into a simple assault vector, especially on more seasoned working frameworks, inadequately changed redistributions and unpatched gadgets.
As continually, keeping your gadgets refreshed will go far in ensuring the normal client. Blocking DLNA/UPnP ports in your firewall (or impairing the administrations altogether) is additionally savvy counsel, when all is said in done.
Contact your equipment merchant or do some online research to decide whether your gadget has ADB empowered and open and request that these sellers 1) leave the investigate interface incapacitated on creation gadgets and 2) not expel the wellbeing instruments Google set up in Android to keep the troubleshoot interface from being clandestinely gotten to and manhandled.
Thank you very much I hope you liked what you read. If you did please don't forget to follow me and please comment and upvote if you did liked it.