A mysterious lab based out of Israel named CTS-Labs notified AMD of five potential flaws in the Ryzen product line 24 hours before it was disclosed. This is typically done 90 days to give the tech companies a chance to fix any flaws before public disclosure in the interest of not having vulnerabilities publicly disclosed in an amount of time that puts people at risk that use them. In the 90 days investigations can occur, and they can try to have a solution ready for the time public disclosure is released.

Not too long ago the Meltdown and Spectre problems were found that impacted Intel far more than AMD and the required fixes are known in some cases to result in a 50% reduction in efficiency of the processors. That was a normal announcement with patches and plans in place at the time of disclosure. This is not the case with this CTS-Labs exposure.
CTS-Labs registered the website that they put the information on February 22nd, and the graphics level are sufficient on the site to indicate they were aware of the problem for some time. They chose to build up a fancy website and prepare for the announcement rather than notify AMD. Ask yourself, why would they do that?
In addition, to these details CTS-Labs also hired a PR firm to handle incoming requests for information. CTS-Labs was started in 2017, and this is the first report they have released to the public.
This was brought to my attention as I read the following Anandtech article, though I also have reviewed other material which I will provide.
Security Researchers Publish Ryzen Flaws, Gave AMD 24 hours Prior Notice
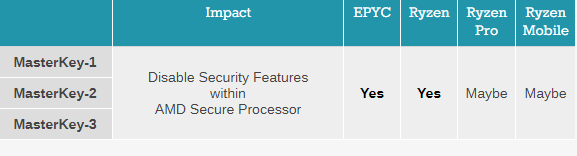
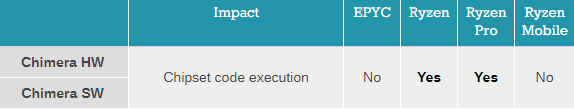
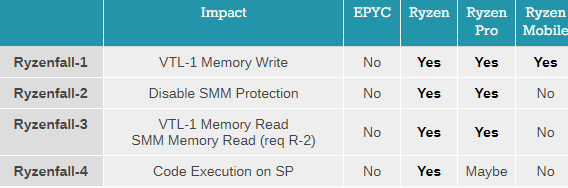
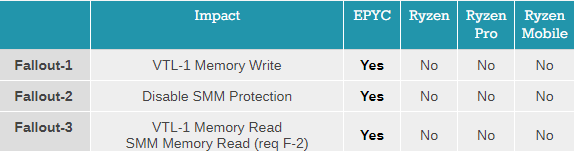
It is worth reading the updates and comments on that particular article. The tables above are screen captures from that article.
Assassination Attempt on AMD by Viceroy Research & CTS Labs
2 possibilities:
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
It actually seems to be more likely Viceroy (investment firm) has more interest in this. The video I embedded is thorough and covers a lot of details. Intel may not be behind this at all, but it is worth considering. Especially, since some of the exposed vulnerabilities would pretty much apply to any computer.
If you already have root access then it is rather moot from that point.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Likely the typical Intel tactics to torpedo its competition. Even if the "flaws" are baseless, AMD has to respond to such allegations.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
My best guess on this is that CTS is frontrunning cover for Israeli intelligence by releasing exploits they are using in order to create plausible deniability for Israeli intelligence, presumably because they are about to do something dramatic with those vulnerabilities.
The financial skulduggery in the background is just generally how such dirty scumbags operate, not the primary intent of the release. If you look back to the assault Georgia undertook on S. Ossetia in order to impel Russian response that would engender seizure of the Baku oil pipeline just over the border, massive derivatives were deployed to profit from the expected Russian actions.
This is typical of such intelligence services, whose players are practically universally self-aggrandizing scumbags that think they're too smart to be wrong, or caught.
Thanks for bringing this to my attention.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
you create a great post....i like it..and waiting for your next post..
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
i like your post.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
To find something good, you need to know a lot better.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Subterfuge and deceit in the chip manufacture industry? Nah, couldn't be.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Do you think this would apply to a AMD Threadripper?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Probably but the exploits seem intentionally sensational. To make them work you already have to have root access... if they have that you're kind of in trouble already.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Root.... reminds me of the TV show "Person of Interest"
That show played out where everything is headed.
Thanks for the insight. If that's the case it is just another day in the park. You would have to be hacked and if you are hacked who cares what kind of a processor you have.
So the headline should have been "if you get hacked and they gain root access, this is what can happen to your AMD Ryzen device."
I was a little skeptical... but we bought a new 16 core 32 thread threadripper.
It actually is the smoothest running machine we have ever owned. It can handle anything we throw at it. So far anyway. Here is the post the wife made about it here.
I would have built it, and did search out all the components we wanted? For the price Cyberpowerpc.com could build it cheaper than I could even get the components. Heck I could not even find 2- 11gb graphic cards for less than 1400 each.
We have not started mining at the current lows it is not worth the electricity.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit