A security researcher has shown that it is possible to bypass any access control alert on macOS Mojave and thus obtain the highest privileges on the machine. No patch is available to date.
Source
On Monday, Apple announced a new version of macOS, called Catalina. However, the firm did not comment on a new zero-day flaw in its macOS Mojave operating system, which security researcher Patrick Wardle revealed the day before at a conference.
This vulnerability allows malware to generate false clicks and, therefore, to validate certain security alerts, such as camera or microphone access, or the installation of a kernel extension.
For an attacker who has already successfully installed his code on a machine, this is a good way to raise his privileges to the highest level.
.png)
Source
An useful function, but easy to divert
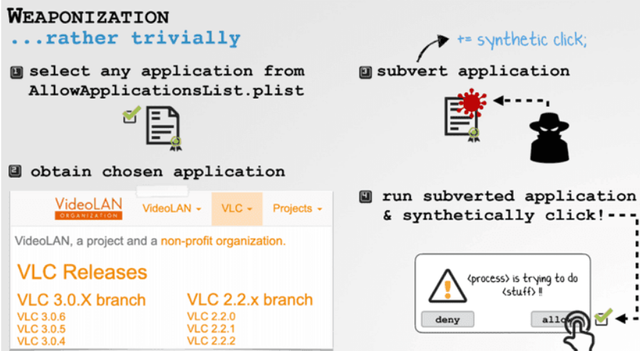
The exploitation of this flaw is based on a macOS functionality that allows to generate virtual clicks. This is used by some applications for accessibility or automation purposes. The applications authorized to make these virtual clicks are registered in a white list.
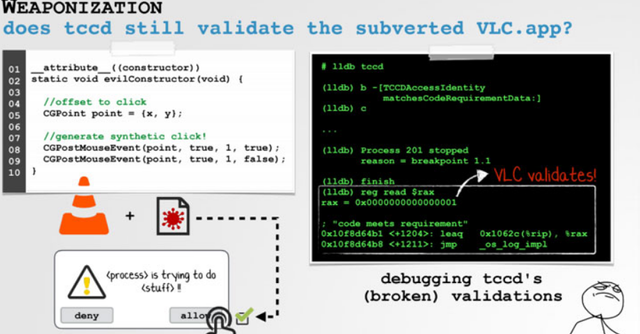
Unfortunately, the underlying verification procedure is flawed. According to Patrick Wardle, all you have to do is take one of the applications on this list, for example VLC, and insert malicious code.
The macOS system sees nothing and allows the fake VLC application to use the virtual click feature to bypass security alerts.
"It's like booking a flight and, when security passes, I only give a piece of paper with my name written on it to identify myself," explains the researcher at the Decipher information site.
No patch is available to date for this flaw.
.png)
.png)
.png)
This is not the first time Patrick Wardle has undermined the protection that security alerts are supposed to provide. Apple introduced this type of access control in macOS exactly one year ago, in June 2018.
Since then, the researcher had already found two ways to bypass them. These flaws have been fixed, but obviously the procedure has not been audited from top to bottom. Too bad.
Source: The Hacker News

I've made a lot of articles with tools, explanations and advises to show you how to protect your privacy and to secure your computer, GO check them out!
This is my guide To Secure your PC after a fresh installation of Windows
If you think that your Phone or your PC has been hacked, you have to check it right now!
That's how you can be more Anonymous on the internet!
The Future of Cyber-Security, what to expect?
The best Crypto debit card – Wirex!
These are the best VPN to protect your numeric life: NordVPN, ExpressVPN and CyberGhost!
Your PC is slow? That's why!
Why is it important to Be Discreet on the Internet
What Do Tech Giants Know About You? A New Tool To Get An Idea!
Feel hot? Your Computer also!
How an Adware works?
That's how you should guard against Trojan!
What are the different Types of hackers?
