Microsoft forgot to remove DNS redirection from an old web service. A stupid mistake that allowed to redirect his domain name to another content, potentially malicious.
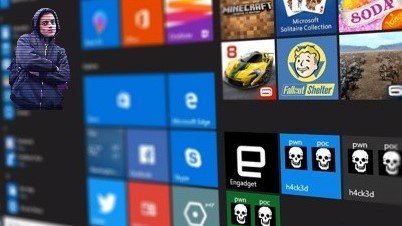
Windows tiles are under influence - Hanno Böck / Martin Wolf
The info
The hacker Hanno Böck has successfully hacked Windows Live Tiles, a technology that Microsoft introduced with Windows 8 that allows websites to display notifications in Start menu tiles using XML tags.
These feeds could be created through a Microsoft web service that is no longer active but whose domain (notifications.buildmypinnedsite.com) still exists and could be hijacked to other potentially malicious content. The hacker took the opportunity to display skulls.
This technique is usually known as "subdomain takeover," an important attack vector that can usually be found in the way most online services allow their users to run web apps or blogs with a custom domain name.
"We have informed about this problem but have not received it yet," Böck said. "Once we cancel the subdomain a bad actor could register it and abuse it for malicious attacks."
What does this entail
This domain hijacking is possible because Microsoft has created a DNS delegation of notifications.buildmypinnedsite.com to azure.com, where the web service was actually hosted. But after closing his service, the publisher forgot to remove this delegation that anyone could use on his behalf.
It was enough to create another web service on azure.com and associate it with notifications.buildmypinnedsite.com, because the Microsoft cloud service does not offer any verification procedure. According to Hacker News, this delegation has since been removed.
The context
This diversion type is a classic. It is even on the rise because the websites integrate more and more third-party services like forum or online store, which only rely on a DNS delegation. But the day publishers remove these services, they no longer think about this redirection.
You wanna try?
- Video that simply show how to do it.
- And this is the web page that allows creating the corresponding meta tags which is still online
Sources: Golem.de and Hacker News

I've made a lot of articles with tools, explanations and advises to show you how to protect your privacy and to secure your computer, GO check them out!
This is my guide to secure your PC after a fresh installation of Windows
If you think that your phone or your PC has been hacked, you have to check it right now!
That's how you can be more Anonymous on the internet!
The future of Cyber-Security, what to expect?
The best crypto debit card – Wirex!
These are the best VPN to protect your numeric life: NordVPN, ExpressVPN and CyberGhost!
Your PC is slow? That's why!
Why is it important to be discreet on the Internet
Feel hot? Your computer also!
How an adware works?
That's how you should guard against Trojan!
What are the different types of hackers?

Gracias por esta valiosa información
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit