
This Was Apple's Terrible, Horrible, No Good, Very Bad Week Of Shoddy Software Issues Macbook
This has been a staggeringly loathsome week for Apple's working frameworks. It's not regularly that we such glaring security issues prop up from the Apple camp, however the people in Cupertino truly failed with amazing gusto - in a manner of speaking - with regards to macOS High Sierra.
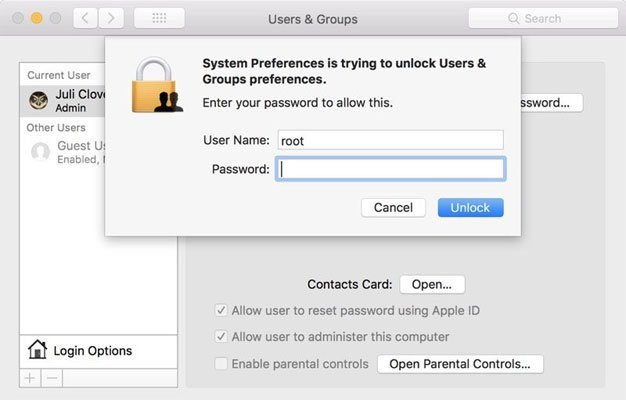
As we gave an account of Wednesday, engineer Lemi Ergin found a huge security weakness in macOS High Sierra that would permit anybody with coordinate physical (or remote access) to a Mac to sidestep manager validation and login without providing a secret word. The means expected to effectively exploit this weakness were amazingly simple:
Open System Preferences
Snap Users and Groups
Tap the bolt for changes
Sort "root" into the username field
Leave the secret key field clear
Snap open
After the adventure was conveyed to Apple's consideration, the organization hurried out a fix in under 24 hours to plug the vast security gap. However, that wasn't its finish, the fix to settle the macOS High Sierra abuse require up breaking document sharing for some Mac clients.
When this most recent programming screw up was conveyed to Apple's consideration, it distributed another help report to walk clients through some [relatively] straightforward strides to repair document sharing. Starting at now, there is no product fix to repair the document sharing screw for regular macOS clients that might be uneasy about messing around in Terminal.
You'd feel that would be the finish of Apple's product inconveniences during the current week, yet you'd not be right. Another report from Wired has uncovered that clients who were still on macOS High Sierra 10.13 - and introduced the surged security fix for the root misuse - saw the impacts of the fix totally fixed by moving up to macOS High Sierra 10.13.1.
"It's extremely genuine, in light of the fact that everybody said 'hello, Apple made a quick refresh to this issue, yippee,'" Innogy programming engineer Volker Chartier in an announcement to Wired. "Be that as it may, when you refresh [to 10.13.1], it returns again and nobody knows it."
"I introduced the refresh again from the App Store, and checked that I could at present trigger the bug. That is awful, awful, terrible," said MalwareBytes analyst Thomas Reed. "Any individual who hasn't yet refreshed to 10.13.1, they're presently in the pipeline set out straight toward this issue."
Evidently, the best way to really take care of the issue for clients that were "late" to refresh to the most up to date form of macOS High Sierra is to introduce 10.13.1, reboot, at that point introduce the root security refresh.
iphone ipad
While things were sufficiently terrible on the macOS side of things, iOS wasn't invulnerable to programming buggery this week. It was uncovered that some iPhone clients running iOS 11.1.1 or 11.1.2 were seeing their gadgets delicate reset today (December second) after 12:15am. As per reports, the issue originated from applications set to convey every day or rehash notices would maximize the CPU and make the gadget delicate reset.
Subsequently, Apple pushed out iOS 11.2 before toward the beginning of today to squash the bug. Apple doesn't normally discharge significant programming refreshes throughout the end of the week (they typically turn out on Tuesdays at 1PM EST), yet this delicate reset bug constrained the organization's hand.
Notwithstanding settling the reset bug, iOS 11.2 additionally conveys 7.5W remote charging to the iPhone 8/iPhone 8 Plus/iPhone X and support for Apple Pay Cash.