
Why do we carry our documents with us?
Nowadays, it is simply common for a person to carry their personal documents with them, because if they do not, they may be barred from certain places or denied access to certain services and products because there is no way to verify that they are eligible to purchase the product/service. From all these situations, people have been motivated to always carry important documents with them to avoid this type of problem to the places they frequent or plan to go, so they are always looking for the best way to take these documents with them.
Is Internet access really necessary?
Having a document proves the occurrence of an event and can be used to document financial transactions. Currently most of us store our personal and/or work documents locally, in the cloud and on servers that are connected to a single network. However, with technological advances, the digitalization of paper documents has not simplified the task of archiving and storing them, since to a certain extent, storing and organizing documents digitally may be more complex than before, because most ways of storing documents digitally need to have access to the Internet in order to be able to fulfill their functions regarding the storage of documents without problems, limiting them in some cases due to the speed of the Internet that the user has.
Most of the techniques that have been developed for document storage today need to be connected to an Internet network to both verify your identification and let the user organize, upload and locate their documents, all in a secure way.
But what if that access to the network is compromised? A failure in one of the instances could put our documents, identity and funds in the hands of someone else without our knowledge, all this because an internet connection is necessary to access them. If something uses an Internet connection to set its security standards, it can cause unexpected damage.
The backbone of the Goldilock Security Suite is a patent-pending, user-controlled, remotely activated airgap security solution for cryptocurrency key custody and storage of sensitive digital assets.
Goldilock Whitepaper
Hot vs Cold, who is the best storage method?
This will depend on what you do. You probably use one more than the other or both equally, but how do they differ?
Hot Storage are those wallets that remain connected to the internet (also known as hot wallets). These wallets resemble a checking account, which you have for payment of services, purchase of goods, carrying out transactions or for exchanging cryptomoney, and more.
Cold storage is characterized by their high efficiency as a safety mechanism. Cold storage means storing your assets away from any device that can connect directly to the network (stay offline), so your coins would be protected against cyber attacks. They are highly recommended in the case of possessing large quantities of cryptos whose loss is catastrophic for the user.
It is important that you find the one that covers the concerns you have: security of thefts, ease of transfer, convenience, cost, or even the style of the same, so choosing one the method that best suits you may be the best investment you make for the financial future of your investments the market and data, but what if you could choose a method that uses a combination of both?
This brings us to Goldilock, a solution and efficient alternative for the storage and management of sensitve data and cryptocurrencies in a decentralized way through the use of NEO platforms.

Goldilock is a new digital asset security system that acts as remotely disconnected cold storage until such time that the user needs access to their data for its intended purpose with the use of encrypted nodes.
Goldilock is built on three core premises to insure a perfect work when it comes to protect your funds and sensitive data:
- Who uses it, will need access to its personal data quickly, but it will be in but it will be occasional so it will be for a short time, thus reducing the time the data are onlnes, preventing them from falling into the hands of third parties.
- Personal data must be isolated, protected from physical contact and related human error, and a full backup made, to fully protect the user
- Both personal data and private keys must be accessible quickly when needed.
Goldilock's patent-pending technology uses these premises to make sure personal data storage and private key custody are fully protected without complicating the access to them.
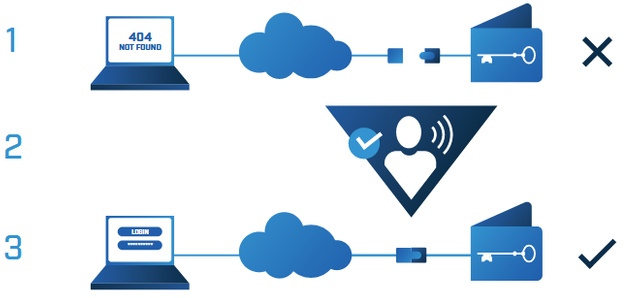
- The wallet will be stored offline with the use of a physical airgap mechanism, which is not accessible through the internet.
- With the use of a non-IP mechanism, users will activated their wallets making accessible over the internet.
- Users will be able to secure their wallets thanks to an ecrypted connection that uses a dedicated URL and access credentials.
With Goldilock, the security of offline data has benn combined with the convenience of online accessibility. Goldilock is online when you need it, offline when you don't, and available anytime from anywhere.
Goldilock Whitepaper
Application Layer
Since Goldilock's goal is to provide more opportunities to build the next generation of consumer and institutional applications in which we can put all our trust and confidence.
Goldilock Wallet for Cryptocurrency
The wallet is characterized by the purpose of storing and transacting NE0, GAS, and NEP-5 tokens, being the NE0 the most secure cryptocurrency in the actual market.
The wallet will also include a web browser authenticated over SSL, with the next features:
Keys for each wallet will be found on a specific, unique, segmented and ecrypted hardware wallet device that is disconnected from the internet.
For the wallet to be online, it's necessary to brought it online suing a non-IP command and PIN/voice verification over the non-IP Public Switch Telephony Newtwork (PSTN).
When finishing using, the wallet will be offline again.
Unique assigned URL.
For transactions the wallet will require a Two-Factor Authentication.
Goldilock API Services
The main porpuse it's enable institutions that have been using wallet solutions to make use of the Goldilock patent-pending solution for improving the security of it.
The Goldilock API Services will run on-premise, in our colocation facilities, and in the Cloud. These services will make it easy for enterprises and partners to create privacy-focused, consent driven applications. The APIs can be embedded within non-decentralized applications or into stand-alone dApps.
Goldilock Whitepaper
Thanks to the architure Goldilock is using, they will be able to service other major cryptocurrencies and not only NEO, the initial wallet.
Protecting Data/Funds with Hot & Cold Storage
We all use different methods to keep our sensitive data and funds secure, either with the use of hot storages (like the cloud, online wallets or exchanges) or cold storages (personal USB hard drives, Trezor or Ledger wallet), both of them with their own pros and cons, where the biggest problem is that both can get hacked by a third party.
By combining both methods, Goldilock adds an extra layer of security that was previously unavailable using the benefits from the existing storages methods, plus the use of the airgap solution and the use of non-IP mechanism, taking into account past experiences involving cryptocurrency and its users.
Handling sensitive data/funds
Goldilock's goal it's to provide services to its users, who need significantly enhanced security for their digital assets such as funds and sensitve data. For somebody who uses Goldilock won't be facing again problems such as losing an important USB or getting hack.
NEO Platforms, why?

NEO is a non-profit community-driven blockchain project. It utilizes blockchain technology and digital identity to digitize assets and automate the management of digital assets using smart contracts. Using a distributed network, it aims to create a "Smart Economy".
NEO's Website
Combining digital assests, digital identity and smart contracts, NEO's goal is to create a secure blockchain that is recognized by enterprises and goverments, which is the core of Goldilock's premises, since they are the first blockchain project that offers a feature that focus on enabling a regulatory compliant smart economy.
NEO features
Aims for Regulatory Compliance: NEO will make use of the Public Key Infrastructure (PKI) X.509, in order to have the ability to issue and cinfirm digital identites.
Utilizes a Superior Consensus Mechanism: "NEO uses an improvement to the Proof of Work and Proof of Stakeconsensus mechanisms entitled “Delegated Byzantine Fault Tolerance”
(dBFT)." Goldilock WhitepaperProcesses Transactions Faster: Because of the use of dBFT, there is no need to use a large amount of mining machines to complete the algorithm for the transactions verification. NEO's consensus mechanism lets the blockchain process up to 10000 in seconds without transaction costs.
Thanks to these features, Goldilock is able keep secure and efficient the way consumers make their transacctions.
Benefits of integrating Goldilock
In a simple way, integrating Goldilock to today's systems, users will be able to easily keep their data secure, because "anything connected to the internet can and will be hacked". With the integration of Goldilock to their current systems, any company will not longer be affected by the dangers of being connected to the internet, since even the biggest and most secure security system can have flaws that will that would leave sensitibe data and funds at risk, since the way this data is store will be a combination of cold and hot storage methods, specially when it comes to keep secure the client's personal records and funds
With the integration of Goldilock, not only the security it's better, the speed of transactions also increases, since it has a better handling of peak traffic periods.
This integration will also provide to leverage our remotely-automated airgap custody solution, since users will be able to to choose between and in-house proprietary license or an outsourced
service model, focusing on the hot wallet operators.
For cold wallet operators, the integration of Goldilock will ensure them an improvement to their existing technologies, allowing them an easier acces, yet
secure and remote solution.

Lock Token
Goldilock's own digital token "LOCK" will be register as a NEP-5 (agreed protocol that allows smart contracts).
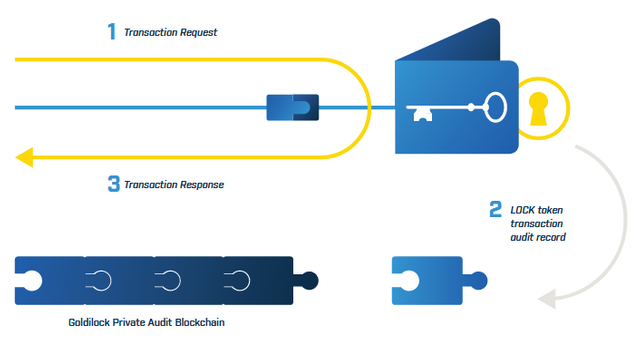
The LOCK token is required to access the Goldilock Wallet. When the user logs into the Goldilock Wallet, the Wallet will query the NEO public Blockchain to confirm the user’s public key address owns a LOCK token. If the user’s public key address owns a LOCK token, then the Goldilock Wallet will launch in the user’s browser. When the user is granted access, the Wallet will write audit information to our own Private Audit Blockchain. These audit entries will ensure that every time your private key is brought online, this access is written to immutable storage that can be queried from the Goldilock Wallet.
Goldilock Whitepaper
With this tokens, Goldilock will provide users a record of their node activity but, they will keep it encrypted and locked away from everyone, in addition, this token will be the accepted method for individual subscriptions payments on the Goldilock Security Suite.
Conclusions
What Goldilock wants to achive it will change the way cryptocurrencies and sensitive data will be stored, combining the benefits of using cold and hot storage to create the perfect method.
With this new mechanism, users will no longer have to worry about losing their data/funds to third party actions as they will know exactly how they are stored, plus offering and efficient way to make secure transactions and sers will be able to keep their data and cryptocurrencies wallte with them all the time.
If they integrate perfectly to current systems, clients and the company will not have to worry about attacks that cause them to lose millions in money and data.
Finally, Goldilock mechanism will keep secure everything you want no matter what it is in the same way.
Thanks for reading.
Team



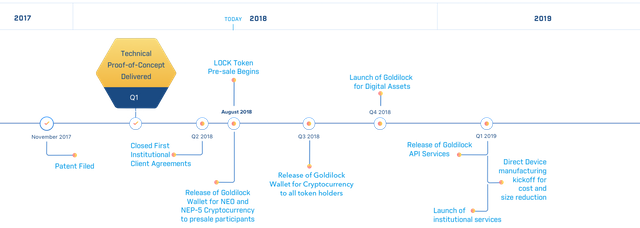
Road Map
Link to tweet here.
goldilock2018
goldilocktwitter

This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit