
The technology of the network opens an infinite world towards possibilities; she has changed the world and has revolutionized the limits of communication, has made it possible to shorten distances and today we can hardly imagine a world without internet. During the last years, another phenomenon has been on the scene and it is the revolution of the block chain that has given way to a world of multiple opportunities based on decentralization.
Nowadays the need to keep our wallet secure has become very much desired by the users and companies that daily manipulate it, since they know that data is exposed hacker and to give solution to this problem. Goldilock presents the new online alternative that meet the expectations of all.

Goldilock , solution for security

Security is translated into trust and Goldilock clear objective is to change the way in which data is stored and secured through innovations that allow the individual and institutions to keep their digital assets secured in storage through their physical disconnection system the network until the moment in which the user decides to make use of it. Goldilock stores a huge database of hundreds of thousands of users and companies and knows in depth the value of the protection of the information.
Goldilock security suite is a patent-pending, remotely activated airgap security solution that is alternated by a non-IP command, although blockchain is designed to be a secure additional accounting technology, the reality is that it is also susceptible and vulnerable to cyber attacks .
Goldilock leverages the authentication of multiple factors to keep your wallets safe and away from the existing hacks in the cryptocurrency industry.

What is Goldilock

It is defined as a storage system that acts at the moment in which the user needs to access their funds or data, the platform works through remote physical disconnection and employs a biometric authentication system, cryptography and triggering regressive technology. Goldilock philosophy is based on the idea that if you are connected to the internet then you are prone to hacking affirmations that turn out to be true.
For the user to access their data, Goldilock provides a secure connection with a time limit through non-IP technology with multiple layers of authentication.

Because Goldilock is the solution for data security
Actually, traditional storage solutions are not the answer to provide investors with an adequate key management solution, access and USB keys are often lost, damaged or stolen and the cold storage solution with encryption features they offer other companies do not cover most of the needs.
Many are the disadvantages that protecting data and assets when using state financial institutions,"banks"because although they can offer an acceptable level of security bureaucratic processes usually take days to complete; any data or cryptocurrency assets that have access to the network with total security will be vulnerable to possible attacks.
Only in the last 2 years, more than 4. thousand million electronic records and accounts banks and credit cards have been affected and more than 1.2 million in cryptoactives have been stolen during that same period.
Goldilock security suite offers its firm commitment through its limited remote activation software and through a series of security filters that the user must approve to have access to their information the security program includes:
Goldilock wallet: designed for investors in cryptoactive whose financial movements are constant.
Integration through the API: Designed for those institutions that need to take advantage of remotely operated airgap technology to store sensitive information, such as keys and digital assets.
Storage: distributed in physical vaults in central data and oriented to institutions that require direct control over their servers.
Local implementation: For institutional or personal domestic use operated under the safety of airgap.
The applications offered by Goldilock are endless because their commitment to security and trust with all their users and institutions is a crucial issue for the company's credibility.

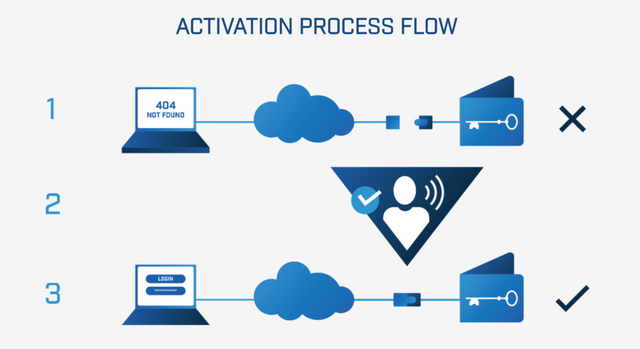
How Goldilock works
Goldilock works through bridge and security blockade offline and online, this allows data storage
- The wallet is stored offline through the physical airgap and can not be accessed from the internet.
- Through the non-IP mechanism the user activates his wallet making it accessible through the internet.
- The user accesses securely through an encrypted connection using a unique URL and through access credentials.
source image

When to use Godilock
Goldilock is positioned to promote a consumer service to institutions that require a significant improvement of their security system providing essential solutions in the security of their keys, cryptocurrencies and relevant data. Goldilock takes advantage of a completely offline system when it is not in use, but provides immediate access when the person requires it, the system can take advantage of it to store private cryptocurrency codes, banking and credit information, personal identity, health data, digital media and signing and approval keys; The Goldilock wallet always remains online to perform the necessary operations required by the user, being a highly reliable and proven system.
Goldilock transforms technology and changes the way data is stored.
- Exchange of cryptocurrency
The frequent flow of exchange of cryptocurrency makes possible the loss of this by theft or fraud and this can come to represent billions with the integration of the central custody solution, the exchanges become a key solution of custodian to account of wallet individual with remote security.
- Secure digital vaul
Goldiloc keeps all the information secure by means of physical disconnection of storage, the tokens lock can only be manipulated by the owner of the account, previous approval and verification of the authentication codes.
- Credit Reporting Agency
The technological application of Goldilock eliminates the need to have personal credit information online in the moments that require its use with prior authorization; the transfers will now be more secure and convenient thanks to the secure back-end solution, to manage accounts and transactions.
- Copyright management
With the application of Goldilock technology, authors can afford a better distribution and administration of their rights and contents, which translates into benefits and control over publications, improving availability and distribution, to allow millions of people to access content authentic.

Reason why Goldilock makes use neo

The use of Neo intelligent contract is due to the integration with pre-existing decoding programming languages that will facilitate individual digital key and signatures. Neo as a blockhain project creates digital identity to manage digital assets through smart contracts by combining digital assets, digital identity and smart contracts
Neo plans to develop secure and recognized blockhain by serious companies and government legislation that is what Goldilock is looking for. Neo as a platform offers features focused on enabling an intelligent economy that complies with regulations; This feature is consistent with Goldilock's mission, which establishes an efficient and possible secure transaction guarantee among blockchain consumers.

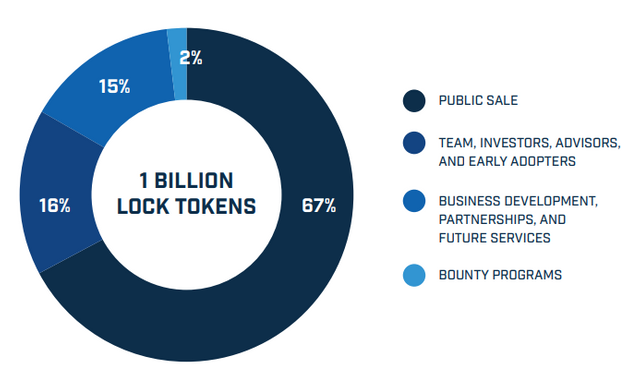
The Lock tokens and their participation
The lock tockens can be acquired through bitcoin (BTC), Ethereum (ETC), NEO and USD to weigh the project and protect its taxpayers, all the founders and advisers are under a blocking obligation contract for a period of 6 months on the assets of their tokens. The sale of the tokens will have a maximum limit of 50 million US dollars to finance the acctions of the companies.
.png)
Source

In conclusion
Although blockchain-based storage services offer an optimal level of security by simply staying on the network, it is susceptible to being hacked and corrupted data; This situation has been studied and analyzed by the team of professionals that make up Goldilock, through the development of the Goldilock security suite application, which seeks to resolve those risk situations that generate an impact on trust and damage, to cryptocurrency assets that have millions of users.

Goldilock Website
Goldilock WhitePaper
Goldilock Tokenomics
Goldilock Telegram
Goldilock Discord
Goldilock Linkedin
Goldilock Twitter
Goldilock Github

This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
edu mis saludos como estas ?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hola duque gracias muy bien y tu?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Como siempre muy buena tu publicación @edurley
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hola amiga agradecida con tu visita y apoyo, saludos
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for sharing.
Have a nice day
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hola amigo muchas gracias, igualmente feliz día
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Excelente información y muy bien planteada
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hola muchas gracias por pasar por mi post, saludos!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Excelente, muy buen post :o
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit