Introduction

With the advent of the World Wide Web (www) in 1991, a new world order was established. The virtual world came into being and literally moved the physical world’s interactions into the virtual world. In many cases, it made life easier than before.
The not-so-great part was that the real world stealing also found its way into the virtual world. It isn’t hard to see why, after all, banking to insurance, finance to sales transactions happen online today. Where else do hackers (virtual world analogy of robbers) need to look at? Visa alone handles transactions to the tune of 56,000 per second every day. Take all the financial interactions of international trade, personal banking, and corporate banking, and we are literally talking about trillions of dollars changing hands in the virtual world.
Well, the virtual world itself expanded too. Starting in 2008, the world saw the advent of the blockchain era thanks to Bitcoin. Blockchain’s inherent strengths of decentralization, immutable ledger, no single point of failure, etc. made it a popular choice for the virtual world to transition to. But guess what? Even blockchain has its security challenges, more importantly, at the hands of the individual users who unwittingly give out their private keys.
So, in a nut-shell not only the non-blockchain based virtual world but also the blockchain world requires secure storage of important digital assets like private key and passwords.
-----------------------------------------------******-------------------------------------------------
Virtual World Security
As per Gartner, one of the leading global research companies, the spend on Information Technology (IT) security in 2018 is expected to reach USD 96 bn. It has risen from USD 82 bn in 2016. This is just one of many indicators showing that with every dollar spent on security, hackers are finding ways to breach it, and therefore, the spend keeps on increasing. Mind you, 96 billion dollars is not a small amount. If IT security was a country, it would appear 66th on the list of 190 countries based on Gross Domestic Product (GDP). That means, with the money we can literally buy countries listed from 67th onwards. That’s how big the spend is. Now, does that give readers a sense?
Here’s Gartner’s take on the increase in spend:
Overall, a large portion of security spending is driven by an organization's reaction toward security breaches as more high profile cyberattacks and data breaches affect organizations worldwide," said Ruggero Contu, research director at Gartner. "Cyberattacks such as WannaCry and NotPetya, and most recently the Equifax breach, have a direct effect on security spend because these types of attacks last up to three years.
Further bifurcation of the spend is shown below:
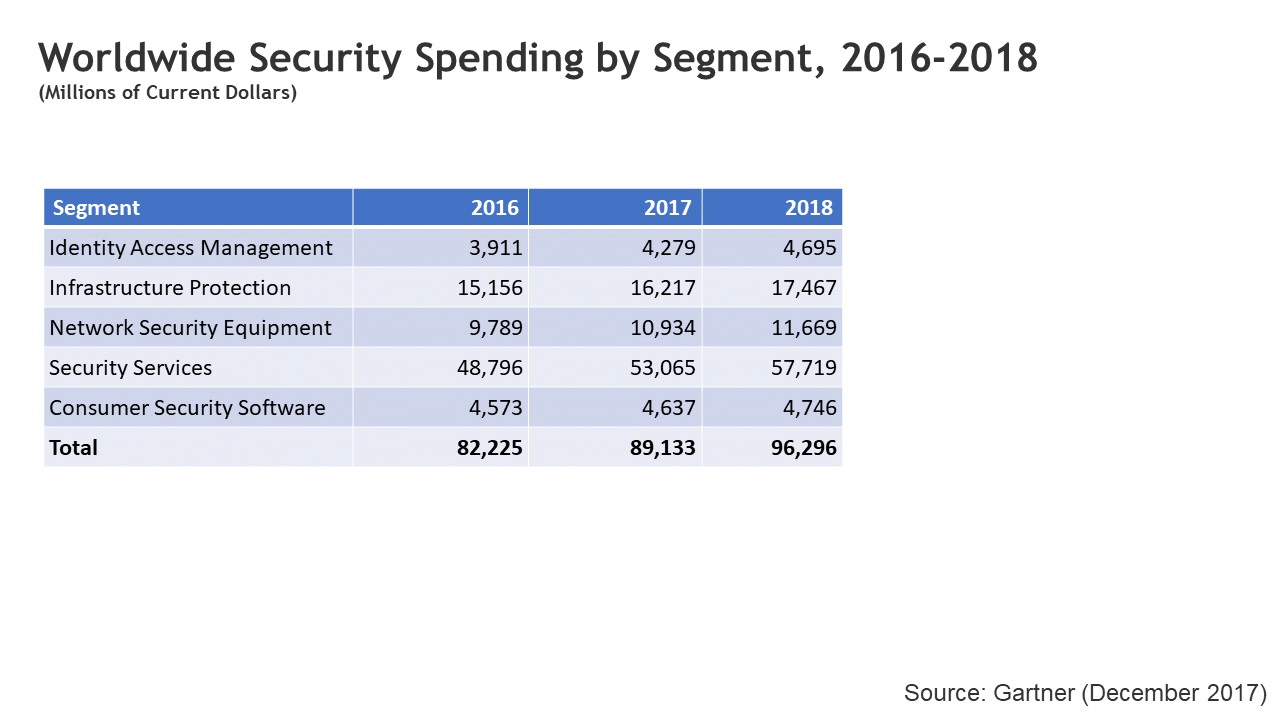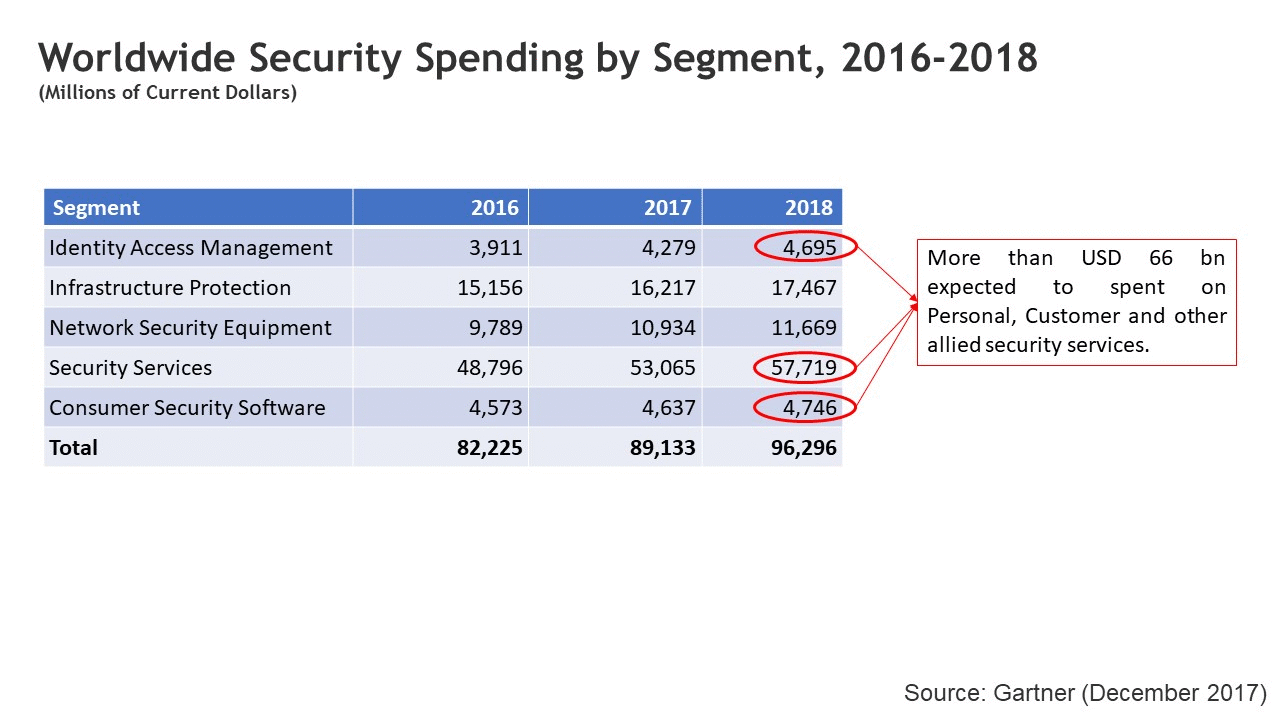
As we can see individual security and corporate security on behalf of customers tops USD 66 bn. This means that security in the current form is breachable, if not completely beatable. Besides, the numbers do not include the security spend towards the crypto-world. Last two years alone, have seen USD 1.2 bn worth of cryptocurrency being stolen. We can only imagine what would be the total security cost considering the blockchain world.
-----------------------------------------------******-------------------------------------------------
So, what’s the solution?
The solution, obviously, is the safe storage of digital assets, passwords and private keys of individuals and corporates alike. This can be done in two known ways - cold storage or hot storage.
Now, cold storage is basically storing out of the virtual world and accessing it when required. This could be an encrypted USB, a bank vault or even the humble paper, where you can write down the password or private key. The advantage is that there is no possible way of hacking these types of storages. However, challenges are physical damage (USB) or aging (paper), not to mention misplacing, and constrained access (bank vaults) in case of multiple needs per day or need to access while traveling.
Hot storage, on the other hand, mitigates all the challenges we saw under cold storage but opens the storage itself to hacking. In fact, this type of storage is what the world is trying to secure with the USD 96 bn we discussed so far.
The real solution would be something which combines the benefits of cold storage and ease of access of hot storage.
Do we have such a solution?
Turns out there is a soon-to-be-patented solution out there, after all.
----------------------------------------------******------------------------------------------------
Goldilock, let’s get to know them
Goldilock brings a storage solution which can be termed as revolutionary considering it tries to bring together the benefits of the cold and hot storage forms. So, basically, the digital assets will be stored in a wallet offline by a physical airgap between the wallet and the online medium. This technology has not been attempted by any company so far and that is how Goldilock is expecting to have it patented soon.
A pictorial representation of this flow is depicted below:
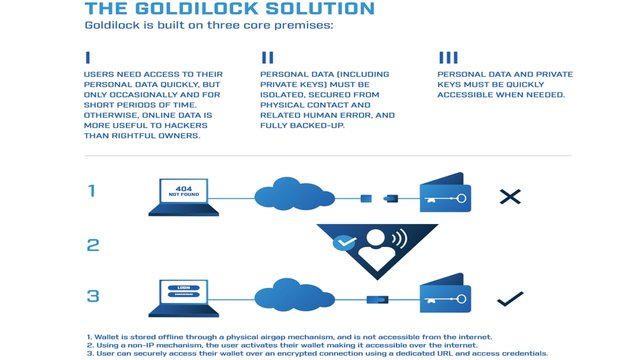
Goldilock digital token is LOCK, an NEP-5 asset on the NEO Blockchain. In fact, the inherent advantages of NEO makes it the right platform for Goldilock.
-----------------------------------------------******--------------------------------------------------
So, why is Goldilock considering NEO as the platform of choice?
At the core of it there appears to be a synergy between Goldilock’s guiding premises of a secure blockchain solution with that of NEO’s. NEO is a non-profit blockchain solution aiming to create a smart economy through digitized assets and smart contracts. NEO’s intention is of building a secure blockchain solution which could be easily adopted by governments and enterprises. So, it's not hard to see Goldilock’s choice.
NEO’s smart contract solution differs from other competitors due to the following additional benefits:
Regulatory Compliance
It is not hard to know that for governments and enterprises to adopt blockchain there is a need for them to be able to verify digital identities and transactions. NEO will be able to issue and confirm digital identify through the use of Public Key Infrastructure [PKI] X.509 standard. This helps it not only to be compliant with regulatory needs but also assures enterprises of being compliant when using NEO platform.
Superior Consensus Mechanism
NEO does away with the traditional Proof of Stake and Proof of Work mechanisms of consensus which are resource intensive but settles for an improved Proof of Stake mechanism called Delegated Byzantine Fault Tolerance (dBFT). The holders of NEO tokens vote for delegates who, in turn, reach a consensus on acceptable transactions.
Faster Transaction Processing
Because of the dBFT the verification of transactions happens from few selected nodes. This means that the transactions can happen faster and with no transaction costs. NEO can process in excess of 10,000 transactions per second. As compared, Ethereum can process only 13 transactions per second. See, the difference?
As mentioned before, these are the attributes which make it the right choice for Goldilock for choosing NEO as the base platform.
-----------------------------------------------******--------------------------------------------------
Benefits of Goldilock
To understand the benefits of Goldilock first let’s take a minute to understand its working. Goldilock Wallet can be accessed only with the LOCK token. When the user logs in, the Wallet queries the NEO blockchain to check if the user’s public key address owns a LOCK token. Only on a positive response, will the wallet launch on the user’s browser and at the same time an audit trail is created by writing the details of login to a Private Audit Blockchain. The user will have access to all his/her/their node activity while ensuring the privacy of their digital asset even from Goldilock's team.
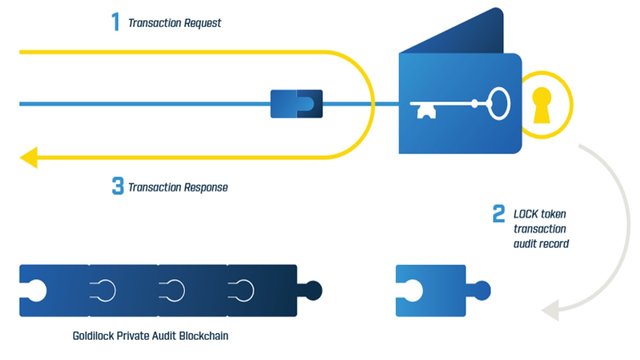
Though Goldilock will be supporting NEO, GAS and NEP – 5 token initially, it will soon branch out to support other cryptocurrencies as well.
So, what are the benefits then?
1. Audit Trail
We just discussed this part. The access to the wallet and the subsequent writing to the Private Blockchain ensures that while the contents of the wallet are secure, the access to the wallet is also monitored and secured. So, any worry on wrong doing from Goldilock team can also be ruled out.
2. Best of the Hot and Cold Storage World
The physical wallet or storage is provided to users on a private vault placed securely at a data center and kept physically disconnected from the internet. Till here it is the cold storage of digital assets. No possible way of hacking.
When the user wants to access the key, an authorized non-IP command will be issued through the Public Switch Telephony Network [PSTN] which will remotely mount the storage device and make it accessible on the net. The access will be enabled by secure web login. The user can then access their data through an encrypted channel. This is the hot storage functionality of the digital assets. However, once the user completes all transactions, the device is once again disconnected from the internet.
3. Mass Adoption
Goldilock will not only cater to the needs of the individual user but also enterprises and governments. The fact that the underlying NEO platform is secure is definitely at the core of adoption but the other aspects are also addressed by the platform. What are the other aspects? Relevance of solution.
The solution is relevant to:
3A. Industry Desiring Client or Data Confidentiality
Financial Records, Health Reports, Legal Documents and similar documents are extremely security sensitive. Custodians of such documents or storage providers of such documents can easily adopt Goldilock and its airgap technology to provide the highest level of security.
3B. Service Model
As Goldilock allows both Platform-as-a-Service and On-Premise implementations, the buying enterprise (or government) may decide its own model of engagement, making the solution flexible for clients.
3C. Hot Wallet Operators
The solution need not compete with existing hot wallet operators, in fact, such operators can tie up with Goldilock and benefit from the airgap technology. This would make them secure from hacks and at the same time improve customer confidence on their solution. The client data, as already explained, will remain secure and encrypted, thereby, alleviating any doubts of Goldilock team accessing it.
3D. Cold Wallet Operators
Incidentally, neither are the cold wallet operators the competitors of Goldilock. In fact, they too can utilize the benefits of airgap technology for their clients and in a way upgrade their solution for their customers. It is hard to see why a customer looking for a cold wallet would not be excited by Goldilock powered solution.
3E. Cryptocurrency Exchanges
Cryptocurrency Exchanges either act as custodian of user keys or leave it to the client to figure out how to store their keys. Goldilock can benefit both types of Exchanges. The ones offering custodian services can enhance the same with the airgap technology, while the ones not offering so far, can enhance their services by offering airgap custodian service.
-----------------------------------------------******--------------------------------------------------
1. Crypto Use Case
A new crypto company brings in a revolutionary idea of using idle computing power and storage space which users can share with the decentralized grid. Participants can be single users, data centers or even businesses willing to share their idle resource and earn from it. While the crypto company has used innovative technology of slicing the data and images being stored so that no single node can hack and takeover data, the data keys are still a cause of worry for users as much as the corporates. This delays mass adoption.
The crypto company comes to know of Goldilock and gets to know about their about to be patented airgap technology of digital asset safe-keeping. They tie up with Goldilock and provide the services to their users as well.
This collaboration brings about unparalleled data security and data key (access) security. Not only will the data be sliced by the crypto company disallowing any single node takeover, the hacking of the node key itself will also be impossible because of Goldilock. This gives confidence to corporates and single users and mass-adoption follows.
2. Bank
Goldilock’s current negotiations with one of the largest banks in the United States has received a feedback that the solution will enable the bank to provide a “safer and more convenient” way of doing wire transfers for their clients.
It is also possible that Goldilock may in future find many customers who operate accounts in multiple banks as a suitable candidate to adopt their solution. Such customers can store their KYC related documents in one place and use it for completing the KYC procedures in multiple banks, at differing intervals. This saves them time and effort to do the same process again and again with the same set of documents.
Conversely, banks can store the submitted KYC documents in Goldilock vaults and at the desired interval, ask customers to login and verify. And only if there are changes do they need to upload documents. For such a service, the bank can charge a nominal fee in LOCK token which a customer would be happy to pay instead of filing documents again.
-----------------------------------------------******--------------------------------------------------
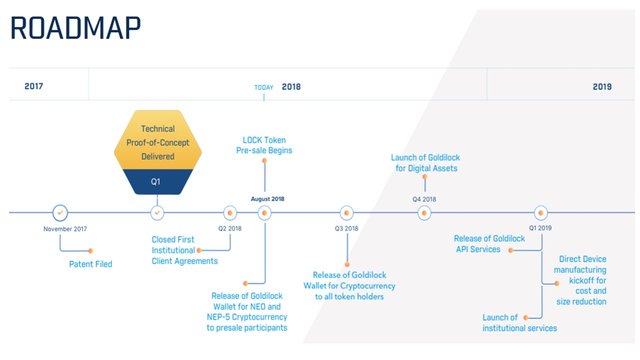
So, what next for Goldilock?
Here is the roadmap:
-----------------------------------------------******---------------------------------------------------
And the team behind Goldilock?


-----------------------------------------------******---------------------------------------------------
It is also recommended that readers understand more about Goldilock through any of the following informative resources.
- Goldilock Website
- Goldilock WhitePaper
- Goldilock Tokenomics
- Goldilock Telegram
- Goldilock Discord
- Goldilock Linkedin
- Goldilock Facebook
- Goldilock Twitter
- Goldilock Reddit
- Goldilock Github
-----------------------------------------------******--------------------------------------------------
This article is written in response to originalworks’ call on authors’ thoughts on Goldilock. It can be read here.
Image Courtesy: Pixabay and Goldilock Resources
goldilock2018
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Your post had been curated by the @buildawhale team and mentioned here:
https://steemit.com/curation/@buildawhale/buildawhale-curation-digest-08-09-18
Keep up the good work and original content, everyone appreciates it!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you @nicnas! Appreciate the mention!!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @oivas! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPDownvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Great article @oivas
Goldilock project is quite complicated, but you managed to explain everything very clerarly using intuitive examples and step-by-step explanations. Pleasant read :)
All the best
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks @crypto.piotr! :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit