
INTRODUCTION
The problem of storage is one that has always affected the tech world. The option has always been between cold or hot storage. The advent of cyber theft in the world today has plagued the lives of online investors and mangers, as it causes them to either choose to store their important documents or information in a cold hardware storage or to store them online in hot wallets.

The problem associated with either of these storages is that, if it is stored in cold storages, say a USB storage or on a piece of paper, these storages can get damaged, hence losing the files in them or probably stolen since they would be required to be with the person at all times.
So therefor, what is GOLDILOCK?
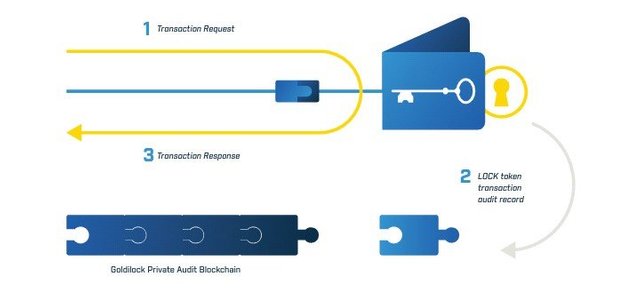
Goldilock is a revolutionary digital asset security system which acts as remotely disconnected cold storage until such time that the user needs access to their data for its intended purpose.
Goldilock is a kind of system of storage which has the characteristics of both a cold and hot storages. How?
Because it stores the information, document or keys of the user in an offline until the user brings their device online which then activates when it is online. It does not come online over the internet but rather through a non-IP command.
It is treated with the same level of security as with your sensitive information in a bank. The moment the user is done with whatever transaction that the person was performing on his node, it is then reverted to an isolated entity that cannot be assessed over the internet.
The reason for such security is because we believe that basically anything placed on the internet can be accessed given due time.
Goldilock is built around the premise that anything connected to the internet can and will be hacked.
The past few years have seen more than 3 billion data breaches across many sectors, from banking and credit, into personal health data and digital rights, through to billions of dollars stolen in the cryptocurrency industry, proving time and time again that no industry is safe from intrusion.
This statement goes to show that at various sectors of life in this modern age, there has always been the issue of data breach or data being stolen or data loss. As the years run by, the number increases even as our security is supposed to be tighter.
PROBLEMS ASSOCIATED WITH COLD AND HOT STORAGES.
There are various problems associated with cold and hot storages and they include
- the user has to be a techie
- hot storages are targets for hackers and cyber criminals.
- cold storages could be damaged easily, broken or misplaced.
- cold storage makes data inaccessible without physical device
BENEFITS OF GOLDILOCK
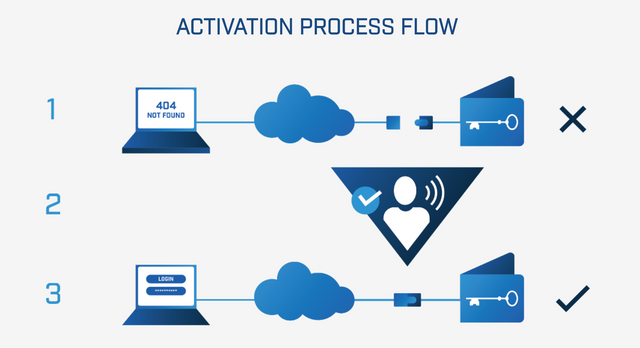
First off, let us take a look at the benefit of the airgap technology, the airgap technology, it is employed by various institutions in order to protect tightly the valuable information or assets of their customers. It does so, by ensuring that the information cannot be accessed physically or through a network/ internet. This is because it keeps the information in a kind of vacuum that can only be remotely accessed by using a non- IP command from the designated node. This helps to guarantee the integrity of the asset and information that is to be stored.
The development of Goldilock is aimed at tackling both consumer and institutionalized problems, for the consumers;
It hopes to provide better security for people who want a better security for their private cryptocurrency wallet and also for a more secure and flexible global availability for private key custody than offered by physical hardware crypto wallet (Goldilock Whitepaper Page 6)
While for Institutions, it would provide a full security for their user’s sensitive information and documents, ensuring that they completely offline when not accessed by the consumer and only grant access to the consumers at the time when they are in need of it.

APPLICATIONS FOR GOLDILOCK IN THE WORLD
Goldilock can be applied to various industries in our society;
In medicine, Goldilock can be used to store valuable information and to avoid the hospital firewall from being breached by hackers who lie about their medical insurance.
In banking, it is already being utilized and grants exclusive access to the customer only when they choose to access it.
In Research, it can be used to protect valuable information and also important researches.
In State security, it can be used to store the details and information about high ranking criminals and would ensure that their information cannot be taken down by any one. It would also help in protecting the data base of the force.
In Cryptocurrency, it can be used to store various cryptos in their wallets without fear of cyber theft.
Also in Voting machines, it would help to maintain the data and avoid corruption or manipulation of such data.
It can be utilized in Digital rights management so as to protect their digital files.
It can also be applied in various sectors of the state in as much as the security of data and confidentiality is of utmost important.
GOLDILOCK LOCK TOKEN
The Goldilock LOCK token would be registered as an NEP-5 asset on the NEO blockchain. The token would be purchased and would be the pass for a user to get access into his Goldilock wallet. The user would have to insert his public key address in order to log into the Goldilock wallet, this would be granted after the NEO public blockchain confirms that the user has a LOCK token. On the condition that the user’s public address has a LOCK token, then the wallet would be launched from the user’s browser.
The LOCK token would hold a record of the user’s node activity while keeping the user’s data encrypted and it will also be the accepted means of payment for the Goldilock security suite.
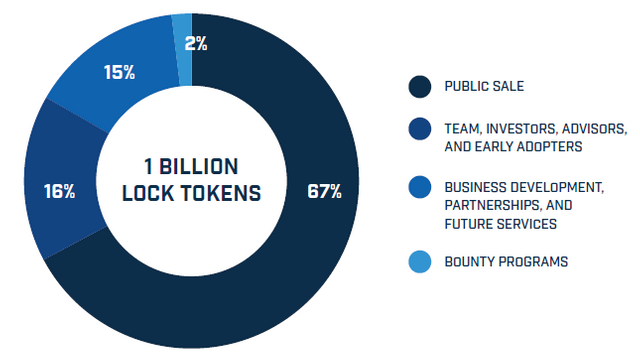
TOKEN ALLOCATION
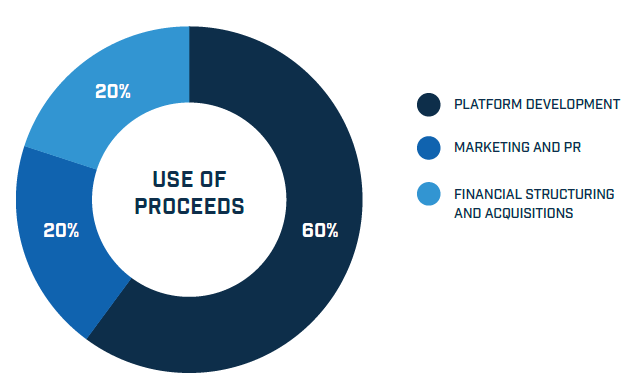
TOKEN PROCEEDS
REASON FOR THE NEO SMART ECONOMY
Because the NEO economy is a non-profit blockchain project that is community based, it helps to digitize assets by utilizing the blockchain technology and also digital identity.
It offers the following features for contract competitors:
• Aims for Regulatory Compliance:
With the utilization of the Public Key Infrastructure (PKI) X.509 standard for identity, it is able to issue and confirm digital identities. It also aids large companies and institutions operated by the government to operate on the blockchain.
• Utilizes a Superior Consensus Mechanism:
It utilizes an upgraded Proof of Work and Proof of stake consensus mechanism, which is a modified version of the Proof of Stake protocol called the DELEGATED BYZANTINE FAULT (dBFT). It makes it possible for people who have NEO tokens to vote for delegates.
• Processes Transactions Faster:
Its architecture does not require thousands of machines for mining because of the utilization of the dBFT to finish the resource-expensive algorithm to confirm transaction. This helps to ensure that at least 10,000 transactions are performed on the blockchain per seconds without the need for a transaction cost.
These are the features that make the NEO platform a secure wallet utility token .
These attributes, regulatory compliance, consensus mechanism, and speed at which transaction is processed, makes NEO the ideal platform for a secure wallet utility token.
With combining digital assets, digital identity, and smart contracts, NEO is capable of building a secure blockchain that is recognized by enterprises and government institutions, which is core to Goldilock’s guiding premises.
USE- CASE
PERSONAL
John is a cryptocurrency enthusiast who loves to invest in new cryptocurrencies as they are launched and buy their tokens. But John is having the issue of storing his various keys for his different wallets. Not long ago, his email was hacked and his private mails were exposed and though, he recovered them back, he was scared of what could happen if he decided to save his wallet keys as drafts in his emails.
So Michael, told him about Goldilock and how he could store his wallet keys without fear of it being hacked and stolen. He can store his keys and access them whenever he wants them.
COMMERCIAL
The election for the New President of the Free State was coming up and though THEGREATWALL Inc were in charge of the electoral process and design of the voting machine, they were aware of their strong firewall and had all the latest technology and best engineers on their side so as to keep security breach and hacks to a minimum.
But yet, they were scared of the consequence of an unprecedented hack and how it could affect the outcome of the votes, so an Engineer suggested that they make use of Goldilock to ensure that the data and result are beyond the reach of the hackers, hence certifying their name as THEGREATWALL.
Goldilock helped to provide a unique storage system hence the slogan; it is "not hot storage, not cold storage, just right storage." This helps to ensure that the votes of the citizens are counted properly without external interference.
For More Information:
Goldilock Website
Goldilock WhitePaper
Goldilock Tokenomics
Goldilock Telegram
Goldilock Discord
Goldilock LinkedIn
Goldilock Facebook
Goldilock Twitter
Goldilock Reddit
Goldilock Github
MEET THE TEAM:
ADVISORS:

PARTNERS:
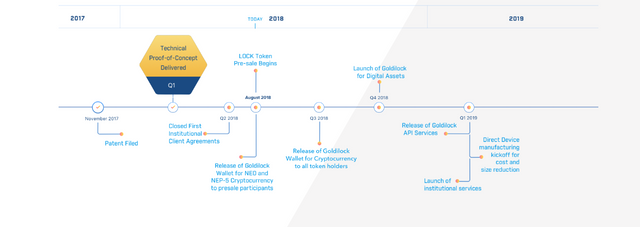
THE ROADMAP:
This is an @originalworks contest.
All the images gotten here are from the Goldilock Website and Goldilock WhitePaper
Twitter Link :https://twitter.com/Svelackddragon/status/1026981787451449344
goldilocktwitter
goldilock2018

This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit