PCAP is Packet Capture
- Packet capture is a vital tool used to keep networks operating safely and efficiently. In the wrong hands, it can also be used to steal sensitive data like usernames and passwords. In this post, we’ll dive into what a packet capture is, how it works, what kind of tools are used, and look at some sample use cases.

The term can also be used to describe the files that packet capture tools output, which are often saved in the .pcap format.
Capturing packets is a common troubleshooting technique for network administrators, and is also used to examine network traffic for security threats.
Following a data breach or other incident, packet captures provide vital forensic clues that aid investigations.
From a threat actor’s perspective, packet captures might be used to steal passwords and other sensitive data. Unlike active reconnaissance techniques like port scanning, capturing packets can be accomplished without leaving any trace behind for investigators.
How does the capture work?
There’s more than one way to catch a packet! Packet captures can be done from a piece of networking equipment like a router or switch, from a dedicated piece of hardware called a tap, from an analyst’s laptop or desktop, and even from mobile devices.
Many enterprise-grade switches and routers now have an embedded packet capture function that can be used to quickly troubleshoot right from the device’s CLI or web interface. Other types of networking equipment like firewalls and wireless access points also commonly have packet capture functionality.
If you’re performing a packet capture on an especially large or busy network, a dedicated network tap might be the best option. Taps are the most expensive way to capture packets but introduce no performance penalty since they are dedicated hardware.
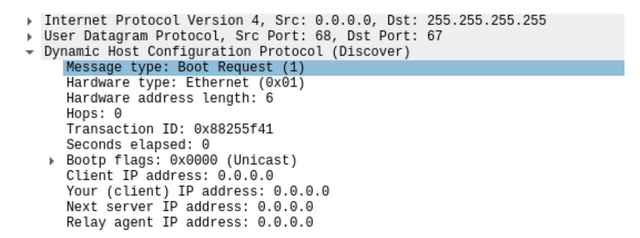
packet captures will always consist of a payload and some headers. The payload consists of the actual data being transferred – this could be bits of a streaming movie, e-mails, ransomware, or anything else traversing a network. Packet headers contain all the critical information that helps network equipment decide what to do with each packet.
Most important are the source and destination addresses, but IP packets have a total of 14 headers covering everything from Class of Service to Protocol Type. A professional network analyst will have detailed knowledge of all of these fields, but a general understanding of packet structure is all it takes to get started troubleshooting performance issues or learning more about how networks operate.
For unencrypted types of traffic, packet sniffers can dig deeper than just the headers and inspect the actual payload. This can be incredibly useful for troubleshooting network issues but is also a potential security issue when sensitive data like usernames and passwords are present. Understanding the meaning behind a packet’s payload can require knowledge of the protocol in use.
Packet capture and network analysis applications frequently include tools to filter, visualize, and inspect large amounts of data. These tools allow for analysis that isn’t possible through manual inspection of a packet capture. Capture files can also be fed into an Intrusion Detection System/Protection Systems (IDS/IPS), Security Information and Event Management System (SIEM), or other types of security products to look for signs of an attack or data breach.
Some of these packet capture tools that will capture and analyze the data coming across your network include. . .
Wireshark With a straightforward GUI and tons of features for sorting, analyzing, and making sense of traffic, Wireshark combines ease of use and powerful capabilities. The Wireshark package also includes a command-line utility called tshark.
tcpdump Lightweight, versatile, and pre-installed on many UNIX-like operating systems. This open source tool can quickly capture packets for later analysis in tools like Wireshark but has plenty of its own commands and switches to make sense of vast sums of network data.
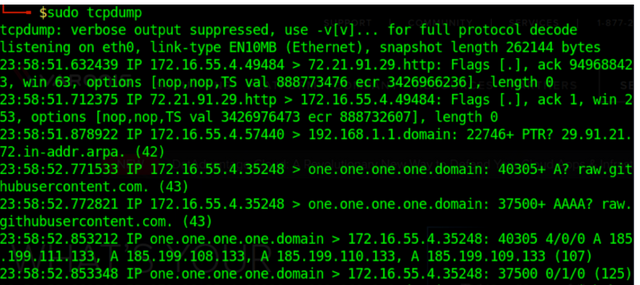
- SolarWinds Network Performance Monitor has long been a favorite for its ease of use, visualizations, and ability to classify traffic by application. Though the tool only installs on Windows platforms, it can sniff and analyze traffic from any type of device.
This was interesting!
https://steemit.com/informationwar/@artistiquejewels/archived-facebook-frames-will-it-stay-u-s-spaceforce-new-cybersecurity
Here is a Facebook Frames on this you can click through, fully sourced!
https://www.facebook.com/melissa.mcgarity.14/posts/10222672291570460
In this case, it appears that the code was intended to be used in a targeted way as its exploitation requires manual intervention.
We’ve been advised that the nature of this attack indicates that it may have been conducted by an outside nation state.
So SolarWinds claims they were the victim of SUNBURST. Were they?
You be the judge if the information overlords will allow you. Will they or will they continue to censor verified info?
Is there more to the story?
Wonder why this happened. . .
According to Yahoo Finance CEO of Solar Winds stepped down and sold off his shares as YF reported.
See more information in the article link.
Other connecting articles,
- Kismet is another PCAP tool. A utility devoted to capturing wireless traffic and detecting wireless networks and devices. Available for Linux, Mac, and Windows platforms, this tool supports a wide range of capture sources including Bluetooth and Zigbee radios. With the right setup, you can capture packets from all of the devices on the network.

Packets are sent back and forth constantly with any amount of jumps or networks in between, theoretically anyone could capture the packets along the way and access your online banking password along with other sensitive material.
Now why isn’t everyone’s online bank account getting hacked every day by people who decide to run packet capturing software?
Because of this security layer which encrypts data prior to transmitting it over the network.
According to CodeMonkeyZ [Ron Watkins from 8kun]
How Would Mike Lindell Obtain Election-Sensitive Data Packets, Such As Votes?
“Now let’s think for a second about Mike Lindell’s PCAPs. If Mike Lindell has PCAPs that prove there was a cyber operation that targeted the election networks, then first we need to think about how he got the PCAPs.”
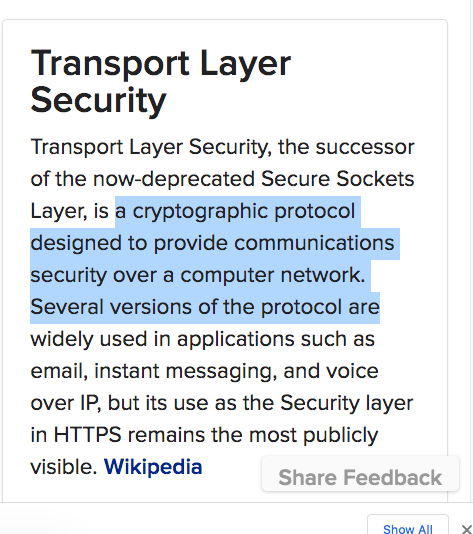
“If we assume TLS was enabled, then Mike Lindell would only be able to get intelligible PCAPs if the person logging the packets was either the sender, receiver, or cracked the encryption of the packets.”
“If Mike’s team was able to crack TLS then we will have a major problem for anybody who uses the internet. There are man-in-the-middle techniques which could grab packets thought to be end-to-end encrypted but very few groups are in position to do so. (see: nsa, cloudflare, etc).”
“Now let’s assume that the sender/receiver of the packets didn’t use TLS. If Mike’s team was able to run the packet capturing mechanism somewhere along the network routes that the election data took, and TLS was not enabled, then we can essentially conclude that He. Has. It. All.”
“The barrier to entry to use TLS is very low. It takes but a minute to enable on a server or software, and takes seconds as an end-user (https is TLS, http isnt). If election management software sent packets over the internet without at least enabling TLS, then that indicates that they are careless at implementing security at the least, and might even be potentially malicious.”
“I have not seen Mike Lindells PCAPs and don’t know the circumstances and data he has, but this could potentially be HUGE if he is able to verify and properly analyze what happened on the networks on election night.”
“Mike Lindell’s PCAPs are very important and might be absolute proof of a cyber operation that targeted the election.”
“I say ‘might’ because PCAPs are a very specific thing and would need to be proven with analysis before we know for sure.”
It is important to note that TLS is only One security measure that is used to protect packets.
A Key Question IS. . .were there election machines that Did have internet capability rather than being private and closed off as they were supposed to be?
You decide!
How sloppy are alleged cheaters?
According to the Gateway Pundit, they not only had internet access, but also had remote login capability.
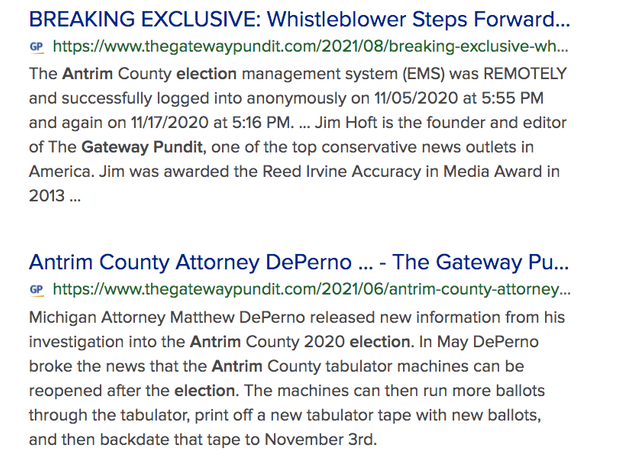
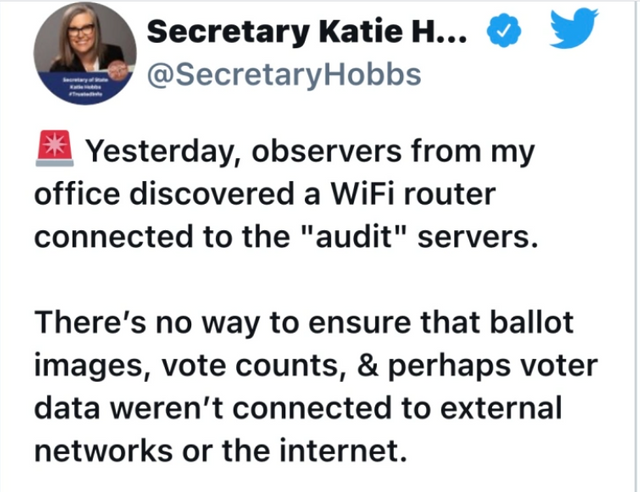
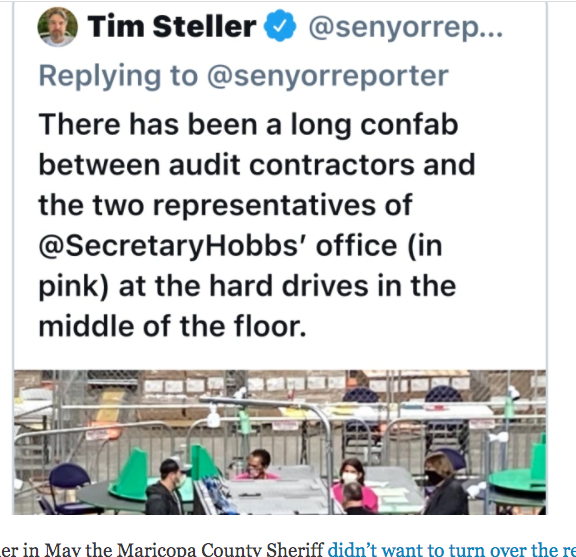
This means the routers must have been used for the voting machines. Otherwise the County would have said that the voting machines were simply not router-connected.
It also means they must have been Internet-connected voting machines.
Why would there be danger of data risk UNLESS those election machines were internet capable?
Pretty curious the sheriff there stated this. . .
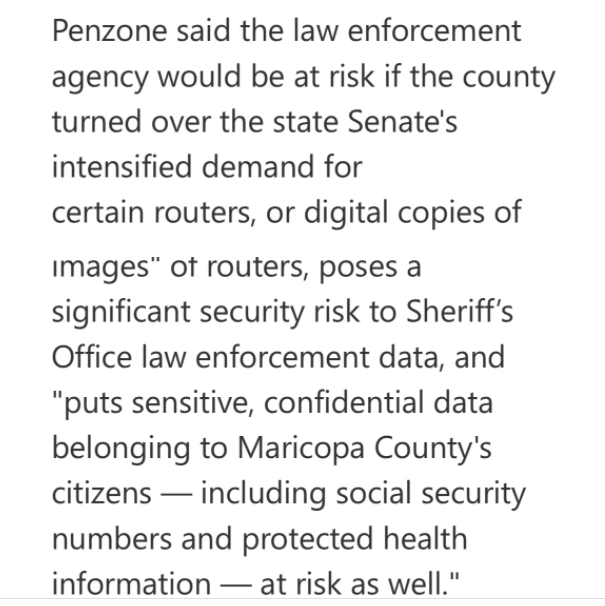
Which is interesting because they don't mind trying to Demand health information from people when they try to force their agenda, contact tracing and health passports. Interesting!
So What was the POINT of Mike Lindell's Cyber Symposium?

But Not just attention from Patriots/Warriors/Truth Tellers, but also those who think of themselves as the "normies" and wouldn't Dare venture far from their Gatekeeper approved Mainstream info all supported by their corporate owned fact checkers for extra security in the programming on their Tell a Vision Boxes!
Did Lindell Purposely want to freak out the other side?
Did he set them up?
You decide!
Did the other side hack into his symposium in an attempt to get the data?
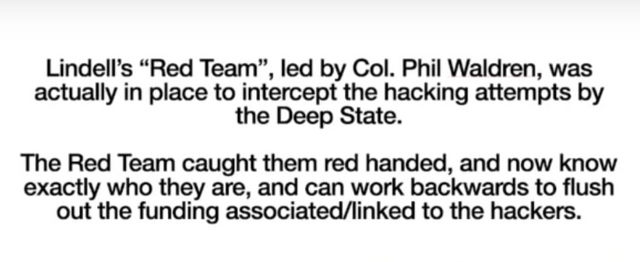
Can they now work backwards and #FollowTheMoney to find the culprits?
You decide!
Sting Op?
Did it work?
Did it make them Think we had the PCAPS and make them desperately attempt to get in?
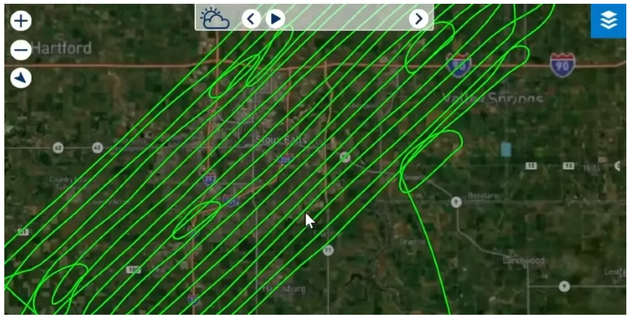
Where did the planes come from that Monkey Werx was talking about?
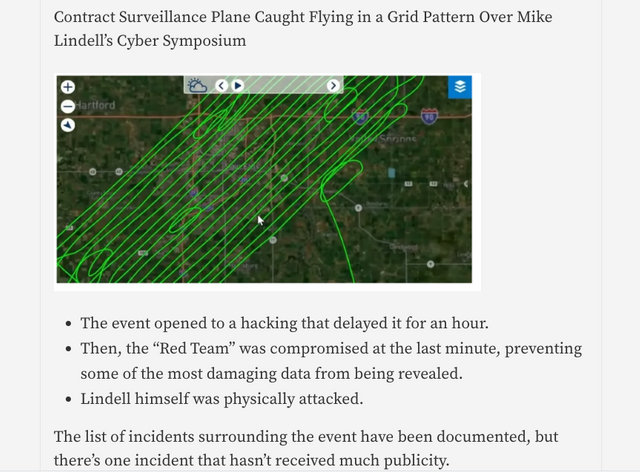
Contract Surveillance Plane Caught Flying in a Grid Pattern Over Mike Lindell’s Cyber Symposium
- The event opened to a hacking that delayed it for an hour.
- Then, the “Red Team” was compromised at the last minute, preventing some of the most damaging data from being revealed.
- Lindell himself was physically attacked.
The list of incidents surrounding the event have been documented, but there’s one incident that hasn’t received much publicity.
According to Monkey Werx there was a contract surveillance plane over the Cyber Symposium flying in a common grid pattern indicative of aerial data collection. In other words, someone was spying on the event from the sky. Here’s his analysis, starting at 5:19
See his SITREP here
Over Sioux Falls Wednesday, August 11, 2021
Check out all the activity from these surveillance planes during the entire time of Mike Lindell's Cyber Symposium.
Do you find this interesting?
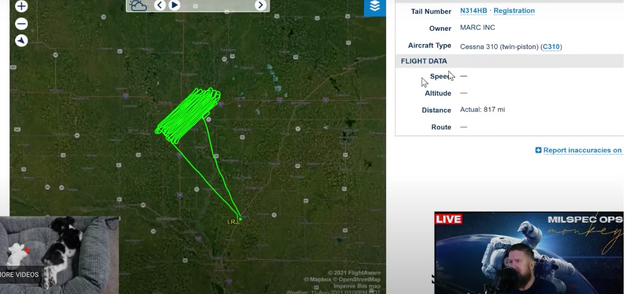
This plane registered as N314HB is registered to Marc Inc.
Here is verification from a local news station in Ohio as to who they are.
Back in March of 2019 there was a plane crash and from the following report you can find. . .
Officials are still investigating what might have caused David Sapp, to crash the plane he was piloting into a Madiera home Tuesday afternoon.
His plane was registered to Mississippi-based MARC, Inc., a company that advertises itself as "North America's largest provider of specialized contract aircraft and flight crews for airborne GIS, survey and surveillance projects,” according to our news partners at WCPO.
RadarBox, a website that tracks air traffic, showed Sapp had been on his way back to the Lunken airport at the time of the crash.
See news report here,
https://www.whio.com/news/local/crews-responding-reported-plane-crash-near-cincinnati/VUAsKG2ehpUWjm2Z2KWWNP/
https://pilotcareercenter.com/Air-Carrier-PCC-Profile/4160/MARC,-Inc
You can see where that local news station got their info here,
http://marcflightservices.com/
Note this on their site. . .
Rapid Response
Because we own and operate our fleet of aircraft, we can usually respond to your data acquisition project within hours. Our dispatch reliablility is excellent and supported by back-up aircraft.

Also from their site under Sensors. ..notice the URL to verify this is from their site,
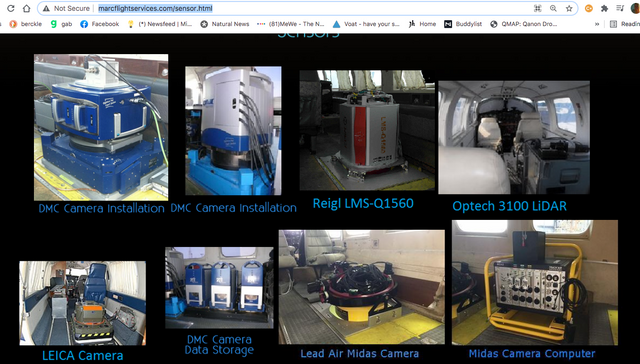

Note who they have provided service to. ..

Go check. ..same thing happened over Arizona when they were doing the audits.
Was the only other person able to have that information. . .the data on the election results which were classified?
Besides President Trump and Mike Pence. . . that only leaves Ezra Cohen Watnik.
Why were
Ezra, Chris Miller and Kash Patel were appointed just two days after the Frankfurt, Germany Raid.
https://iotwreport.com/rumors-trickle-out-on-frankfurt-raid-reads-like-spy-thriller/
It was on November 8, 2020, so only 5 days after the election.
Do you remember what happened to Gina Haspel of the C_a?
Do you remember the CI_ defending those servers at Frankfurt? Why did they do that do you suppose?
Did the Military Intelligence located the servers?
Did they get them and pass off the data and classify it immediately?
When data is classified do you have indicate upon classification Who gets it?
Who did Watnik give the election results to on January 9, 2021?
He wouldn't have by any chance given them to Mike Lindell would he? Or Would he?
You decide!
Are the numbers Mike Lindell put on the screen during the Symposium accurate?
If they are. . .did he receive the data from Watnik?
Were the packet captures released to Lindell at the direction of President Trump?
Was he told to give the SCIF data. ..[Sensitive Compartmented Information Facility U.S. Department of Defense term for a secure room.It can be a secure room or data center that guards against electronic surveillance and suppresses data leakage of sensitive security and military information].
Was anyone involved Fighting on the side of Good given a heads up?
You decide, then ask yourself how was this information know years prior?


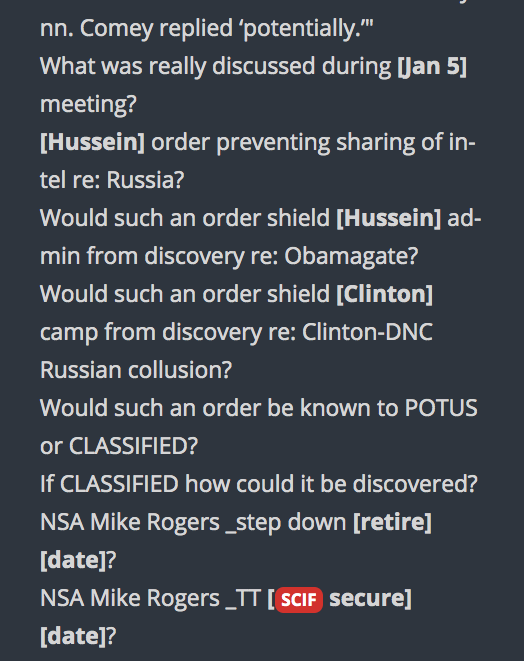
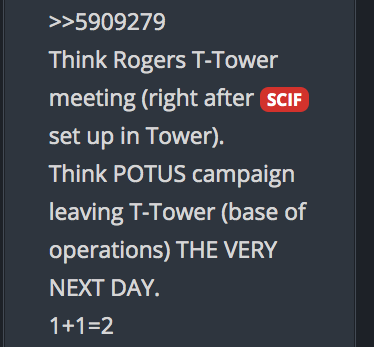
Note the Date. . .
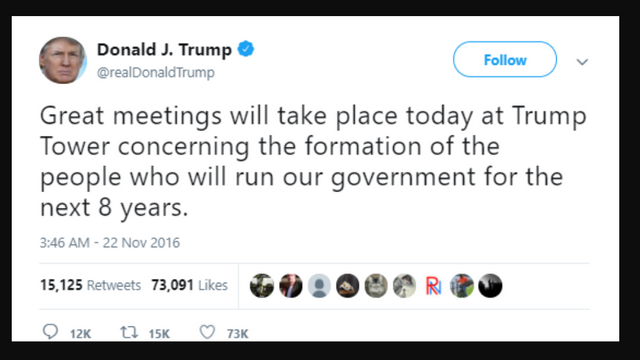
Was this Bait?
You decide!
Did President Trump KNOW they were going to steal the election?
Had they already boasted and indicated this?
You decide!
What is being covered up and Why? Will there ever be a day of reckoning? How long must we wait?
https://www.minds.com/blog/view/1199349759762124800
Did Mike Lindell say he had received the election data on Jann. 9th?
Was Congress given a chance on the 6th to do the right thing?
Why did they refuse even in the face of blatant evidence?
After seeing the Exact totals at the Cyber Symposium. . .Dominion knows without a shadow of a doubt Lindell has those numbers because they knew the Exact, Correct numbers also.
So do they realize now we have that Data and it is not just a poker face?
So was that Symposium for anons/warriors/guardians or was it for the "normies" and those who do not engage on telegram, but rather only listen to mainstream media and what their gatekeepers want them to hear/see?
Did the normies on a higher rung of the totem pole get to see the hard evidence all of us have seen?
In other words the people from the left who are interviewed by the corporate owned mainstream media?
So we are talking government officials. . .for most First Time seeing the actual hard evidence without the hostile telling them they Couldn't look at it.
Do they Now have renewed energy to go back to their state and make this fair and just for their constituents?
Only time will tell!
Are committees being formed on Election Integrity?
Why would the left be opposed to transparency and integrity? You know why!
Will they develop a plan?
Will the voice of the people rather than the controllers finally be heard?
Was the data intercepted at the SCIF?
Was that how they knew it was going to Frankfurt, Germany?

Did you notice what Ezra said when he was appointed as Under Secretary of Defense for Intelligence?
Ezra Cohen Watnick Speech - Civilian Special Ops Under Acting Secretary Of Defense
Transcript of his speech
Today the department of defense
has started the process of formalizing
what we have long done the fundamental role
of US special operations in defense and foreign policy
by elevating special operations forces
to a level on par with military departments.
As authorized and directed by congress
as we enact these reforms we follow the vision
of president John F Kennedy, who
predicted the rise of special operations
nearly 60 years ago.
He foresaw another type of war new in it's intensity,
ancient in its origin that would require
a whole new kind of strategy a
wholly different kind of force.
Forces which are too unconventional to
be called conventional forces
which are growing in number and
importance and significance.
President Kennedy gave these remarks at
the opening of the nuclear age
when the pentagon was primarily
organized to plan
and direct large conventional operations
against superpowers not special
operations short of overt declared
conflict.
the global demands for special operations forces
then and now has confirmed
President Kennedy's foresight.
And now under the leadership of
President Trump
we are fully realizing president Kennedy's
prescient [vetted definition. ..knowledge of things or events before they exist or happen view of special operations forces].
It is fitting that we are again entering
an era of great power competition
as we gather to infer affirm the
the special operations community then as
now I know special operations forces will
play a vital role
and by the historic reforms we have
enacted today
we will ensure special operations forces
as a civilian advocate commensurate
to the secretaries of the other military
departments.
As authorized and directed by congress
as we enact these reforms we follow the
vision of president John F. Kennedy, who
predicted the rise of special operations
nearly 60 years ago
he foresaw another type of war new in
its intensity,
ancient in its origin that would require
a whole new kind of strategy a wholly different
kind of force.
Forces which are too unconventional to
be called conventional forces
which are growing in number and importance and significance.
President Kennedy gave these remarks at
the opening of the nuclear age
when the pentagon was primarily organized to plan
and direct large conventional operations
against superpowers not special
operations short of overt declared conflict.
The global demands for special operations forces
then and now has confirmed President
Kennedy's foresight.
And now under the leadership of
President Trump
we are fully realizing President Kennedy's
prescient view of special operations forces
it is fitting that we are again entering
an era of great power competition
as we gather to infer affirm the
importance of
the special operations community then as now!
I know special operations forces will
play a vital role
and by the historic reforms we have
enacted today
we will ensure special operations forces
as a civilian advocate commensurate
to the secretaries of the
other military departments.
I am honored to serve as your Service
Secretary.
Thank you very much!
https://www.minds.com/blog/view/1198785072206217216

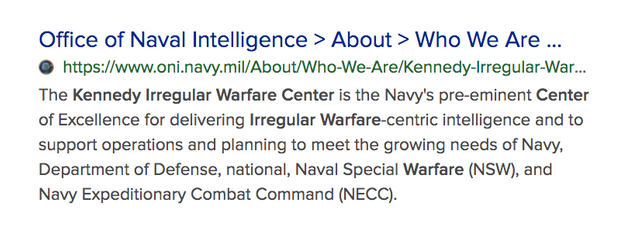
The Kennedy Irregular Warfare Center is the Navy’s pre-eminent Center of Excellence for delivering Irregular Warfare-centric intelligence and to support operations and planning to meet the growing needs of Navy, Department of Defense, national, Naval Special Warfare (NSW), and Navy Expeditionary Combat Command (NECC). The command blends a unique, all-source analysis reachback capability with an ability to deploy intelligence analyst operators alongside naval forces confronting asymmetric challenges around the globe.
Kennedy’s total force concept includes a diverse cadre of multi-discipline intelligence professionals, both military and civilian, versed in operations, analysis, targeting, collection management, directing intelligence collection platforms and unique capabilities rooted in the demanding world-class training and specialized development provided to its workforce. Kennedy professionals develop a thorough understanding of irregular and expeditionary mission sets in the CENTCOM, PACOM, AFRICOM, EUCOM and SOUTHCOM operating areas. Kennedy analysts are often called upon as Directors of Intelligence, Chiefs of Intelligence Operations, All-Source Senior Analysts, Collection Managers and Intelligence, Surveillance and Reconnaissance (ISR) Directors. They are versed in IC analytical tradecraft, targeting, human intelligence support, and further specialized skillsets requested by NSW and NECC operators to provide vital support to unique missions around the world in order to protect national interests.
- Kennedy offers its customers a total intelligence solution ready to deploy globally.
- Kennedy provides its customers with a proven advantage (analytical depth and subject matter expertise), often resulting in by-name requests to support national missions.
- Kennedy analysts routinely assist senior NECC and NSW decision makers in confronting Irregular Warfare challenges.
- Kennedy utilizes cutting edge analytical tools and techniques to provide their customers with a decisive advantage through tailored, specialized intelligence.
NECC Navy Expeditionary Combat Command
organizes, trains, equips and sustains Navy Expeditionary Combat Forces to executive combat, combat support and combat service support missions across the full spectrum of naval, joint, and combined operations.
https://www.necc.usff.navy.mil/

NSW Naval Special Warfare


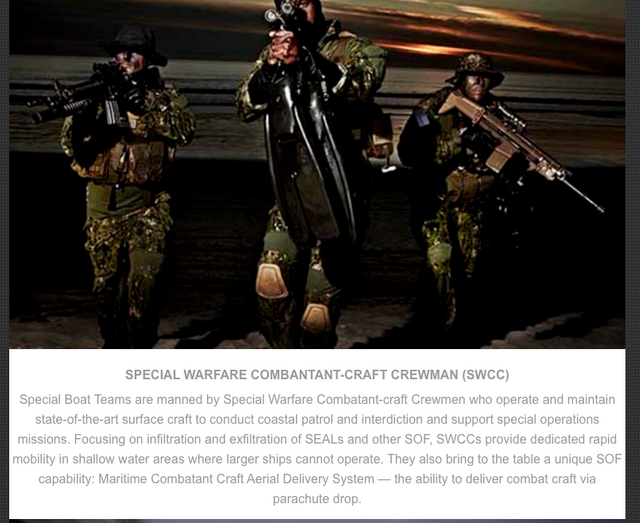
Special Operations Forces are the elite commandos of the U.S. military.
https://www.military.com/special-operations
Special Operations (SO) encompass the use of small units in direct or indirect military actions focused on strategic or operational objectives. They require units with combinations of trained specialized personnel, equipment, and tactics that exceed the routine capabilities of conventional military forces. SO are characterized by certain attributes that cumulatively distinguish them from conventional operations. These operations are politically sensitive missions where only the best equipped and most proficient forces must be deployed to avoid detection and possible mission failure that can result in damage to US prestige and interests.
Four Factors For Successful Special Operations
� Clear national and theater strategic objectives.
� Effective command, control, communications, computers, and intelligence (C4I) support at the operational level.
� Competent tactical planning and execution.
� A force trained, equipped, and organized to conduct Special Operations
https://fas.org/irp/agency/dod/socom/sof-ref-2-1/SOFREF_Ch1.htm
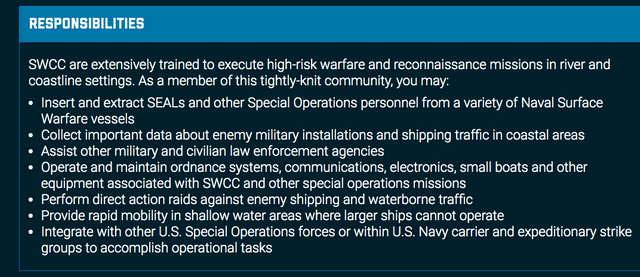
SWCC Special Warfare Combatant-Craft Crewmen
Do you remember John F. Kennedy's role in the Navy?
Read JFK's story in here. . .
How about Kennedy Island?
Were you aware Plum Pudding Island is named after JFK?
It was there in the Solomon Islands where a young John F. Kennedy swam ashore when his PT boat was hit by a Japanese destroyer in 1943.
PT-109, part of the Pacific Ocean theater of World War II. In August 1943 it was to this island that the crew of the PT-109, commanded by then Lieutenant Kennedy, swam after their craft was rammed and wrecked by the Japanese destroyer Amagiri. Two American sailors died in the incident.
Plum Island- how many are there? Super Prison for deadly animal diseases? Can they affect us? Some seem to think so concerning what everyone is Fearful of Right Now from 2019-2021
How about JFK and the Green Berets?
Why were the Green Berets so important to JFK and Jacquelyn? Was JFK Jr part of special training? JFK Jr's tattoo and an Army SF Q Course. The Lancer, the Lark and VF info. What about the Family Ghosts?
See a report that goes over this here,
PHILADELPHIA EXPERIMENT PRECURSOR TO MONTAUK. JFK'S SEVERED SHIP AND HIS ISLAND PLUM PUDDING
https://www.bitchute.com/video/bsH5VNewPITT/
More info here,
FINAL COUNTDOWN NAVY FOOTAGE SHOWING UNIDENTIFIED AERIAL VEHICLES WILL FULL DISCLOSURE COME?
https://www.bitchute.com/video/tCVyeym2Hsyz/
Many connections in here in under 13 min.
IT'S BEEN A LONG ROAD! THE MONTAUK CONNECTION! HAVE YOU SEEN THE SCRIPT?
https://www.bitchute.com/video/LCKnqgVFMJ47/
Now JFK believed there would be a different kind of warfare.
Does this remind you of what General Flynn said here?
Gen. Flynn: An Army of Digital Soldiers and Citizen Journalists To Combat An Insurgency Of The Media
He calls it an Insurgency. ..Irregular warfare at it's finest in politics!
He states, "The journalists we have in the media did a disservice to themselves actually more than they did to this country. . . . because they displayed an arrogance that is unprecedented!"
So were Procedures in place for defense for this irregular warfare put in place by President John F. Kennedy?
Good afternoon. I’m Chris Miller, Acting Secretary of Defense, and I am here today to update you on President Trump’s plan to bring the wars in Afghanistan and Iraq to a successful and responsible conclusion, and to bring our brave Service members home.
From Kabul to Kandahar, and from Mosul to Fallujah, hundreds of thousands of America’s finest sons and daughters who selflessly answered the call to serve in the Army, Navy, Air Force, Marine Corps, and Coast Guard, have brought us to this point. Their efforts and sacrifice will go down in history as epitomizing the strength, commitment and empathy of a force that is unlike any the world has ever seen.
What is Giant Voice. Tweeted prior to PreZ Trump's Suspension. Military Mass Comm System? Here is the evidence. History, Power and Reach of FEMA.
https://www.minds.com/blog/view/1199417708385587200
Mission
The Kennedy Center provides products and services to meet Navy, DoD, National, NSW and NECC maritime Irregular Warfare intelligence requirements and performs other functions and tasks as assigned by higher authority.
This is a Very Telling video on ACTORS and how they have used Admiralty Courts and laws. . . which just give the Illusion of power, yet they are able to Trick people into believing in said Fake power.
Admiralty vs Navy
For example if you look up Admiralty you get this. . .
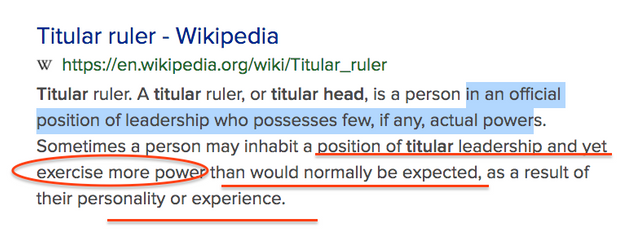
See an interesting video on this here,
Thank you Great Warrior Matt Dentino for the following informative Must Watch Video link!
America's elections HACKED! This expose is a MUST WATCH.
Retired U.S. Army Colonel Phil Waldron breaks down how the entire U.S. election system is controlled by private equity firms and foreign money
Word out is due to Biden and Sons wheeling and dealing. . .he doesn't Want these investigations, transparency and the clean up of our elections.
See a video that goes over this and many connections in under 7 min. here,
GINA HASPEL/THE BIDEN CORRUPTION TIMELINE/EVIDENCED CRIMES/LEADS TO EPSTEIN/SETH RICH WAS HIS NAME!
https://www.bitchute.com/video/bhZvdvOEN92H/