
Peer Mountain
Peak of Security
Peer Mountain also gives users control over their identity, which is cryptographically secure. It is an end-to-end application ecosystem that facilitates the trading and secure exchange of digital and physical services.

PEER MOUNTAIN is the first mobile distributed trust system and the Decentralized Protection Trust. Peer Mountain also uses cryptographic protocols to enable individuals and institutions to create and maintain trusted records that include digital identity, trust relationships, and evidence of activity. Even the most demanding centralized data storage and transmission methods are vulnerable to external attacks.
We have also submitted emblems for Peer Mountain and Peerchain ™ brands below EUIPO 017282931 and 017350182. This may be our intention to release the Peer Mountain Consumer SDK for Golem and iOS as an open offer and to open the Peer Mountain Attestation Engine SDK offering. We also tend to send the Peerchain Protocol to the RFC to develop open standards that can be used as much as possible in any economic context.
Peer Mountain is also a peer-to-peer response that offers you management, personally and securely. They will use your personality to do business and sign illegally binding documents, documents that fit ZertES9. Peer Mountain is hospitable to every service provider. You can access the services directly from security sources and easily review any services you consume anytime, anywhere. The RSA 4096-bit key of your primary key.
Peer Mountain gives users more control over their secure cryptographic identity and provides an end-to-end application ecosystem that facilitates the trading and sharing of digital and physical services. It enables the trust and sharing of secured information with independent parties across a wide network, while ensuring traceability and compliance at the end of each data transfer. Peer Mountain is the first decentralized peer-to-peer trust. The market that connects the identity owners with the appropriate service providers and opens new paradigms on how and where individuals and organizations do business.
At an abstract level, the scheme allows people and companies to confirm facts about themselves and prove (ie verify) the claims. This is often very valuable for monetary facilities as a result of which can significantly reduce the price of hiring buyers in accordance with your customer (KYC).
This article discusses this in the Peer Mountain section of KYC and Compliance. For organizations in sectors other than monetary services and markets, Peer Mountain may even offer a sizeable price as a trusted fact-based platform (for example, workers will state that they are ill and 60 minutes can prove this, if confirmed by a medical certificate).
Ecosystem participants are only aware of their public key (much like cryptocurrencies work) and can accept some people who are basically public keys that are derived from their key roots. Personas are helpful in interacting with different external parties and cling to very different needs and needs. For example, an individual is also a student and a banker.
In general, universities need knowledge different from that required by the bank. However, once a student applies for a loan or a grant, he does not need the university to understand that he is a designated banker. By using completely different roles, the students manage their privacy.
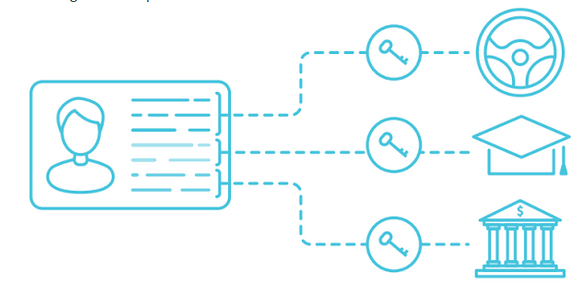
Decentralized trust and protection
Even the most advanced centralized information storage and transmission paths are vulnerable to external attacks. Businesses are looking for cost-effective, compliant ways to protect their customers’ personal information.
Peer Mountain enables secure transactions between individuals, businesses and governments while protecting privacy and preventing data exposure to third parties.
MARKET POSSIBILITIES
The world grows by accessing data and documents whose identities are determined by distributed ledger technology. Last year, there were numerous successful offers from teams that developed the platform for self-identity, in particular Civic2. There are also many new and established offerings in Know Your Customer (KYC), identity verification and trust, including Mitek3, Jumio4, AriadNext5, WorldCheck6, KYC37 and LexisNexis8. Now is the right time for the existing ecosystem in different platforms and entities, while it is satisfactory. Peer Mountain offers the full potential of this emerging paradigm.
SOLUTION: Buy MARKETPLACE in SELF-SOVEREIGN IDENTITY ALL
Peer Mountain uses Blockchain technology to provide people and organizations with a comprehensive, secure identity and, for the first time, to securely shareinformation with organizations and anyplace else. Peer Mountain enables rapid deployment of services through its blockchain framework. Identity can be the core of Peer Mountain, but this can not be linked in care. Peer Mountain Identity Platform is an associate in Nurse application programs designed to facilitate the trading and sharing of digital and physical services.
Private organizations using Peer Mountain can use delegates to demonstrate ownership and management. Peering mounts will then provide a verifiable record of the facts that can be shared with the organization or person that should be most famous. Certain authorities, such as Company registration or trade approval authorities may use approval machines to confirm this fact.
High scalability
Because of their consensus mechanism, blockchains require higher data throughput. Blockchains, however, are unable to process large transactions at the same time.
Peer Mountain provides secure and transparent service segmentation for blockchain implementations. This means that an organization can provide services that require a large amount of real-time transactions in a deliberate peer-mountain block while applying the rest of their services to the usual peer-mountain block.
For example, a bank may operate separate demand deposits, certain types of credit cards and car loans. This setup divides transactions between large and micro transactions and allows banks to achieve higher cross-throughput data for different services and data compatibility between different samples. This means that banks can use information from customer credit card documents in the form of car loans and checking accounts.
Secure transaction without compromise
Peer Mountain individuals and their organizations can securely exchange information with any application in the Peer Mountain ecosystem. By combining sovereign identities and organizations, Peer Mountain creates a secure and efficient marketplace in various companies in the global economy.
Efficient Clear Transactions
The latency in the communication between blockchain node nodes as a result of the setup agreement within the chain limits their group responsiveness. This means that blockchains are not ready to perform method group actions at the speed required for large transaction process systems.
We have an associate in nursing innovative approach to overcome this limitation. We tend to believe that Blockchain should not operate globally on any reachable node. In contrast, Peerchains ™ will coexist and work together harmoniously, all specializing in a greater part of environmental trust.
Each Peer Mountain operates Peerchain ™, which we can use for any service provider, regulator, auditor, trade watch cluster or customer protection cluster. If you want to check chain integrity, you can access the soul that is publicly on the market chain.
Safest identity of solutions in the market
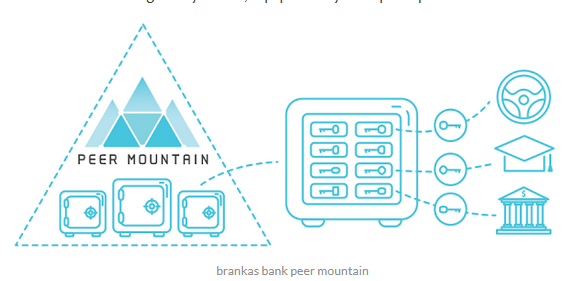
Think of Peer Mountain as a real mountain, with a prudent frontier guard. Every Peer Mountain user has his own “bank safe” with safes hidden in these mountains. You can insert copies of your documents with special keys in different fields. Each button is unique and users can separately share it with entities they trust.
With this special key, this entity can access the user’s safe and retrieve the information that has been released for them, and nothing else. If the user decides to revoke access, the document disappears from the drawer and the key in the changed drawer is possible according to the law applicable to the business relationship. Further access to the Peer Mountain is by invitation only.
Activities are pseudo-anonymous and private. With Peer Mountain, you use different people to interact with different entities, so your activities with one entity remain completely separate from interactions with others. Not only personal information, interactions are also private. Of course, you can release it later, but the choice is up to you.
SmartCap PTM TOKEN SALES
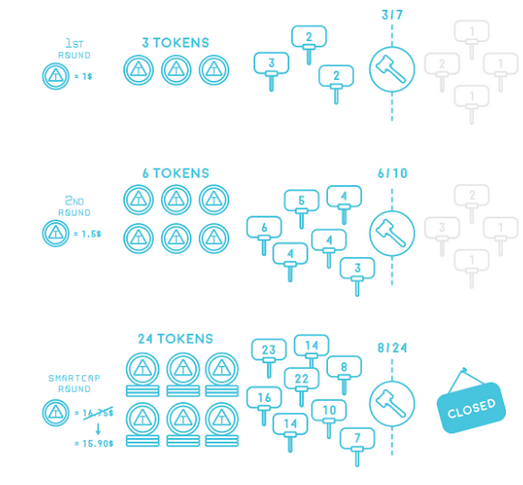
The economics of PMT tokens and the sale of PMT tokens were carefully designed by Jed Grant and validated by Prof Jos Van Bommel, an expert in securities, liquidity and IPO valuation.
In that case, we suggest a method to sell the new token that is included in the sale of our token smart contracts; We call it SmartcapTM algorithm. Smartcap makes it easier to price tokens, fulfilling all buyers and allowing you to complete sales at a specific market price.
As libertarian capitalists, we believe in individual freedom, fairness, transparency and great customer service. We conclude that the current token sale method has several disadvantages:
Traditional pre-sales are opaque, closed and suitable for direct transactions and insider transactions.
Open stocks create a greed that leads to irresponsible capital allocation.
Cap still creates a paradox in which sales organizers must guess the right market demand before starting a sale; If they guess wrong, they will leave the market dissatisfied, or have a “benchmark” sale or an ICO that will not work, even if they are raising capital in large numbers.
SmartcapTM fulfills many of our goals:
Smartcap ™ eliminates pre-sales and brings transparency to the entire token sales process.
Smartcap TM provides a pricing mechanism for the sale.
Smartcap ™ improves algorithmic bid and token prices until demand and pricing are met.
SmartcapTM rewards big investors by putting it in front of the queue every turn.
Parameter Peer mountain SmartcapTM:
Token allocation
We will divide the results into four key areas:
40%: Technology that includes the development and testing of smart contracts, peer mountain, blockchain nodes, application architecture, mobile and corporate customers, and other staged goals.
25%: Business development that includes typical business costs such as office space and equipment, administrative and managerial salaries, fees and taxes.
25%: Marketing, including PR initiatives, marketing and partnerships.
10%: regulations and laws, including lobbying and development of regulatory recommendations.
For more information, please visit:
Website:
http://www.peermountain.com/
Bitcointalk thread:
https://bitcointalk.org/index.php?topic=2642081.0
Telegram:
https://t.me/peermountain
Twitter:
https://twitter.com/PeerMountain
Medium:
https://medium.com/peermountain
Reddit:
https://www.reddit.com/user/PeerMountain/
CREATOR