بِسْمِ ٱللَّٰهِ ٱلرَّحْمَٰنِ ٱلرَّحِيمِ
ٱلسَّلَامُ عَلَيْكُمْ
Hy steemians hope you are good in your respective lifes and here I am presenting you the " HASH CRYPTOGRAPHY" Which is the best course outline for begginers.
The summary is that the cryptographic function are basic and origin of blockchain mania. The data is often deploys us the security formations where the hash graphgs work there for handling the systematic data operation. This is litmus overview, lets jump into more deep.
1) Explain what does the resistance to collision mean? And what does resistance to preimage mean?
RESISTANCE TO COLLISION:
The resistance to Collision means there are several properties where the hash functions place. There by, simply means different block chain aint be (cryptograph) converted in same "HASH" codes might it can be do Collision in the system. Thus the conduct of peoples can be the reason of scams and detaining or threatening situation might occurs. Although the burden of probability of information sms is so wide whilst code ain't. You can find the definite and proper structure which are the result of above facts. Hence the the Collision resistance is designed on those facts which completely impossible. So the message contains same accessories can be generate during collision and danger in system. The Collision process take place when combining different inputs to produces the same data of hash graphgs.
So the HASH functions are designed in mathematical artifacts where the disintegration are integrated in the form of hash data, so the information which is unrepeatable. So the results are understood that hash function are considered resistant until the Collision might not occurs. So the Collision not easily occur might need years then computational calculation need to deploys Collision.
So SHA algorithm have been used to increase the privacy and security, whilst formation of SHA -0 AND SHA-1 are not safe enough. So the SHA 2 AND SHA- 3 are found to be good actor of the collision and are known as "COLLISION RESISTANCE"
RESISTANCE TO PREIMAGE :
The resistance to PREIMAGE is the burden of probability of finding the input that provides output that hash's are generally very weak. So in Collision you cam seem there is number of minimal happening which Hardly gave us Very existing entries
Held, the properties of the Hash function is that a message after being encoded in Hash code can't be decrypted. Which is held to be possible to find the message of that code of return performance, as it is a single way imparting process.
Though it ultimately made hard for malicious people to find the input of the hash provided. So the technocrats provide us effective technology through this junctions.
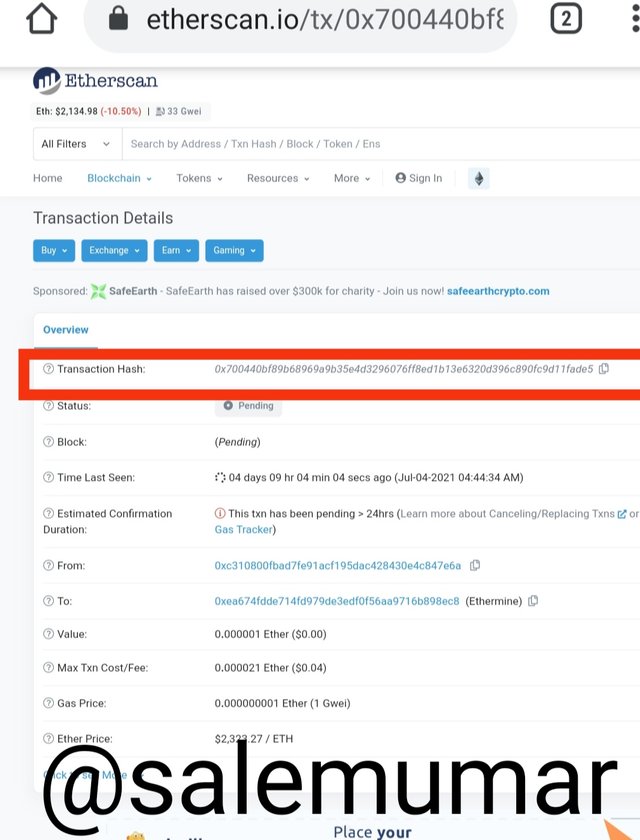
2) Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
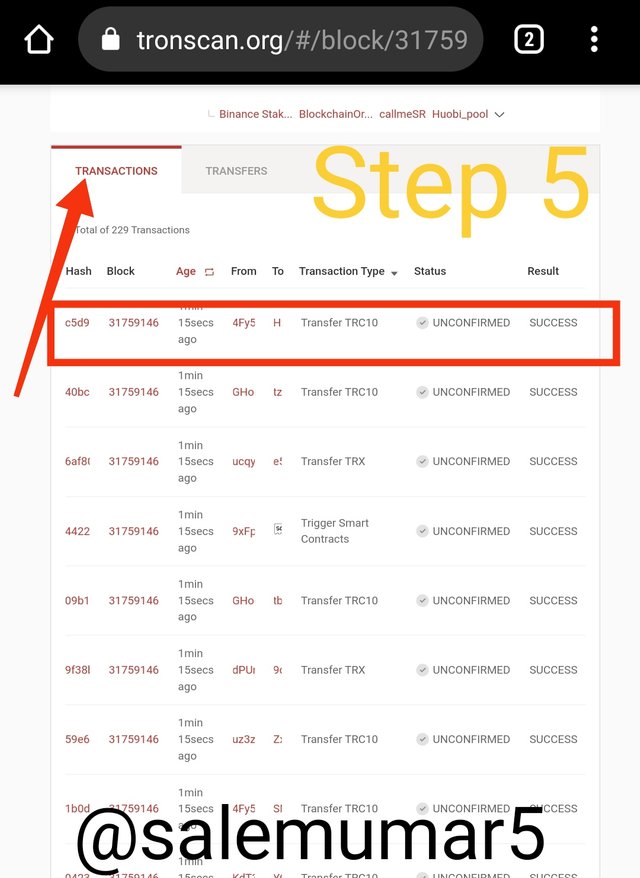
- Go to Tronscan page first link.
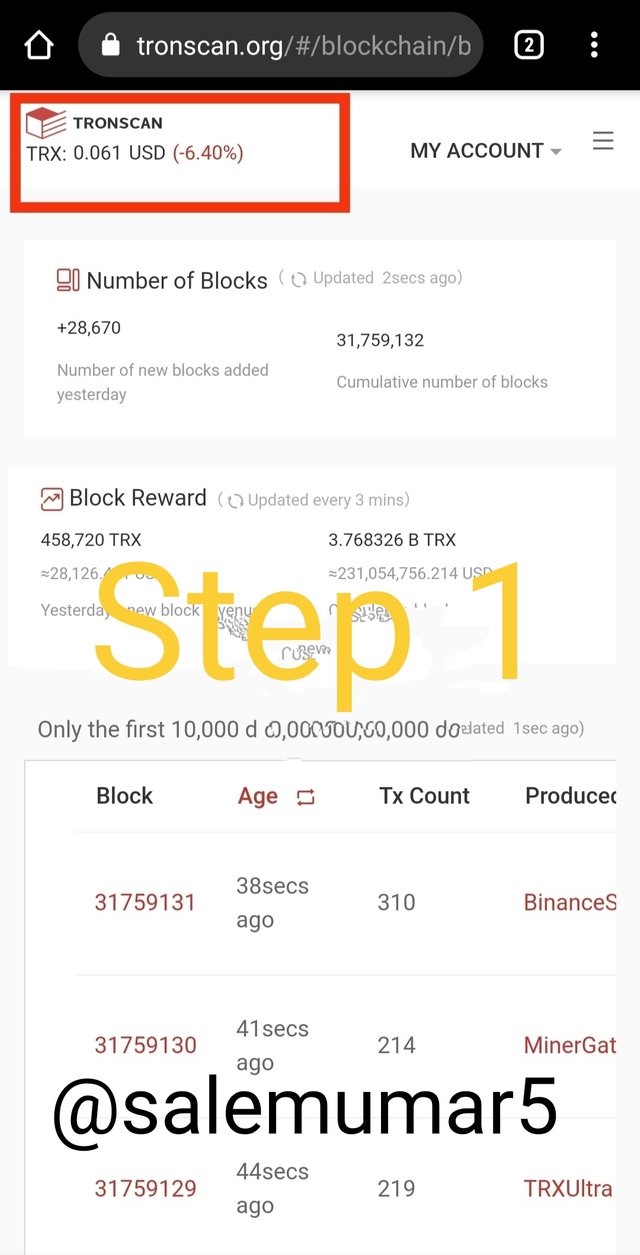
- scroll the page then I find the last validated block. In this case the hash we found 31759146
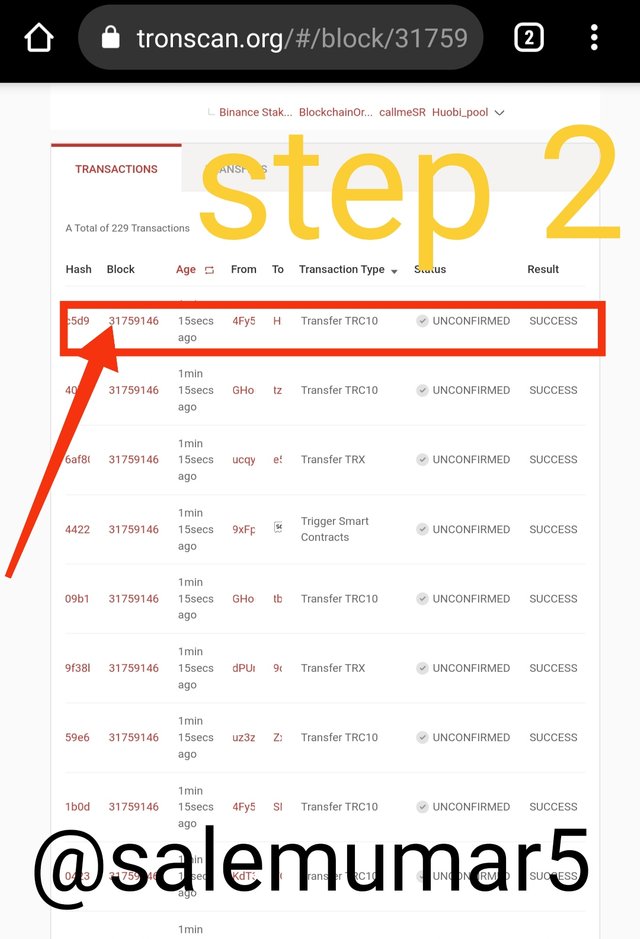
-I select it and there will be shown us all the details of the block, including the Hash, there tou can see the copy clipboard option click on it.
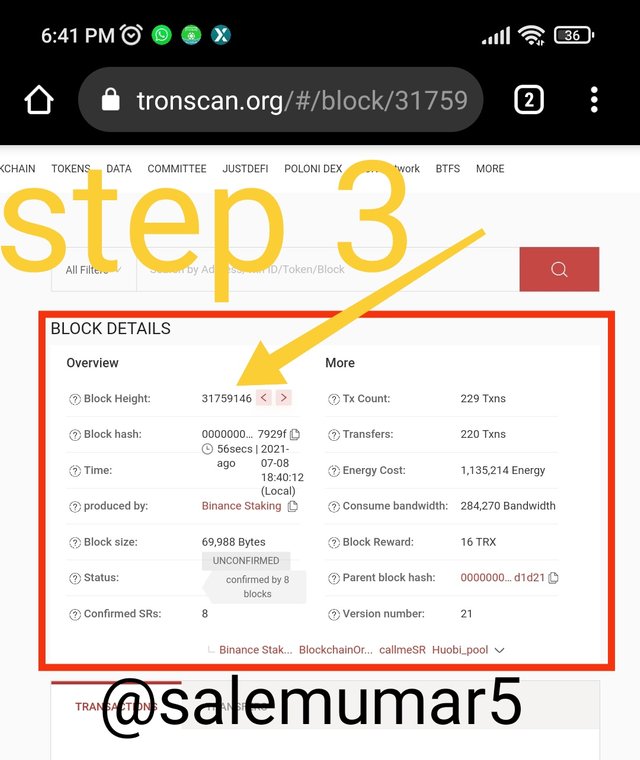
Details of block hash.
- Scroll it and you can see the transactions and look the latest one which show in screen shot.
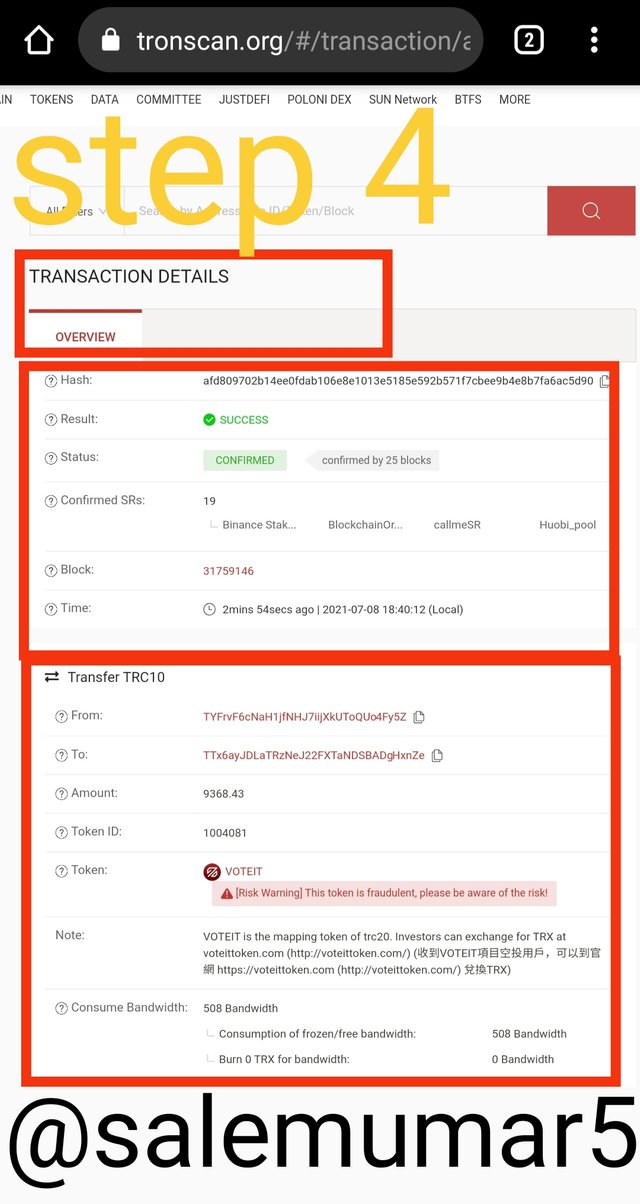
- I click on it further more it give us the details including in Hash.
3) Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
- First of all click on the page of Etherscan
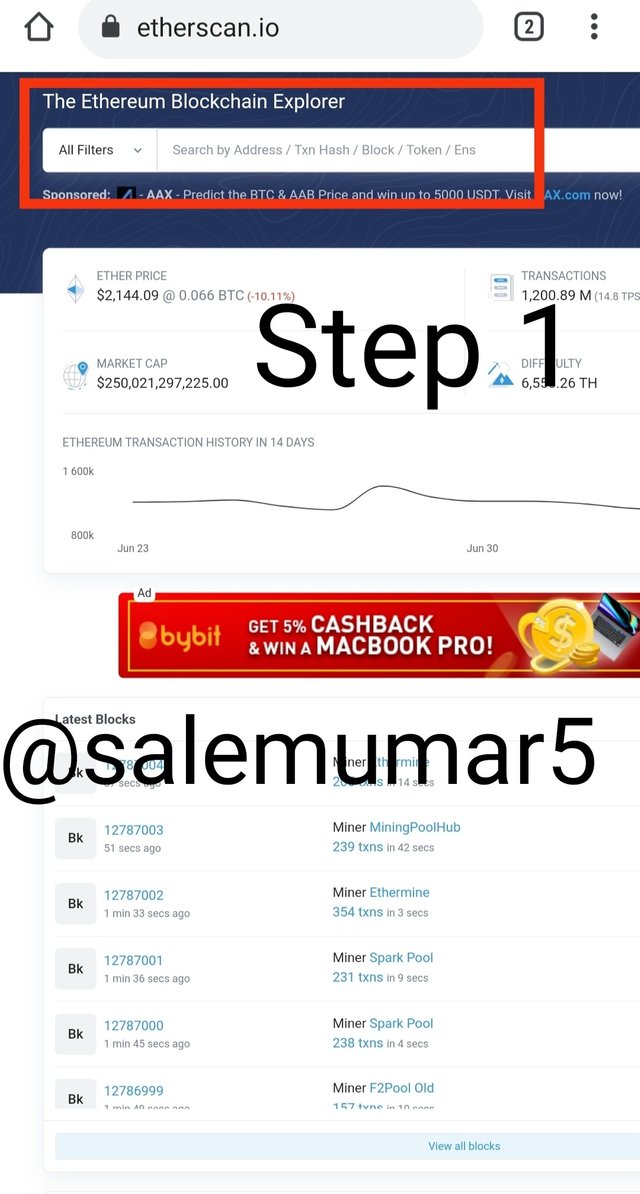
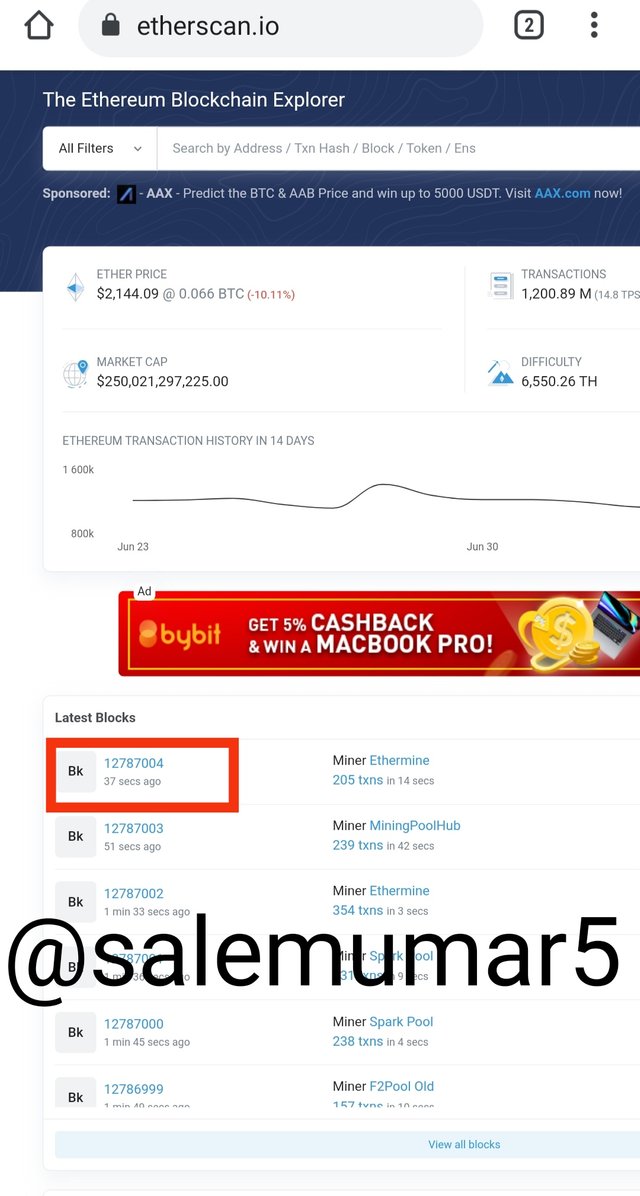
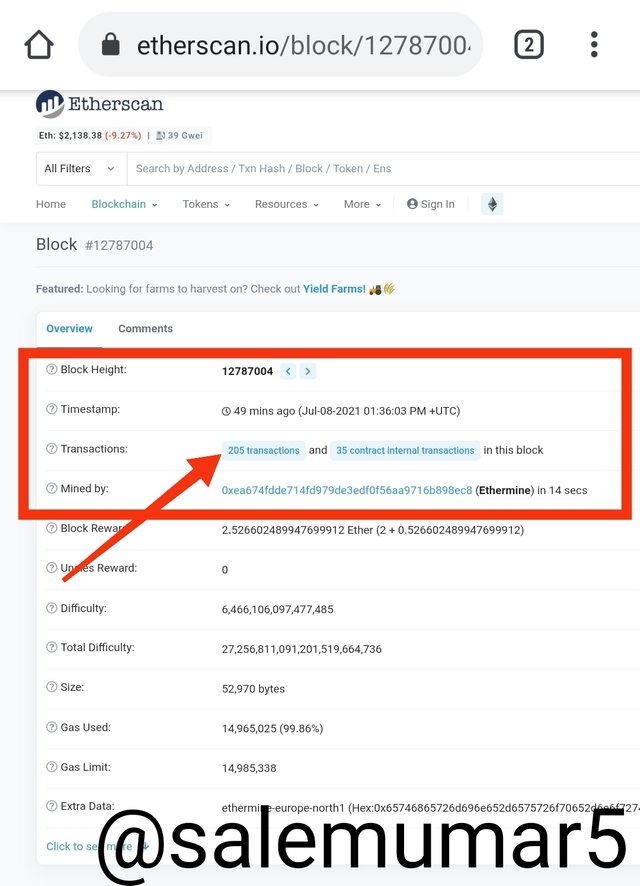
- Scroll down I found latest validate block the case is 12787004
- After that there you can see it shows us all the details of the block.
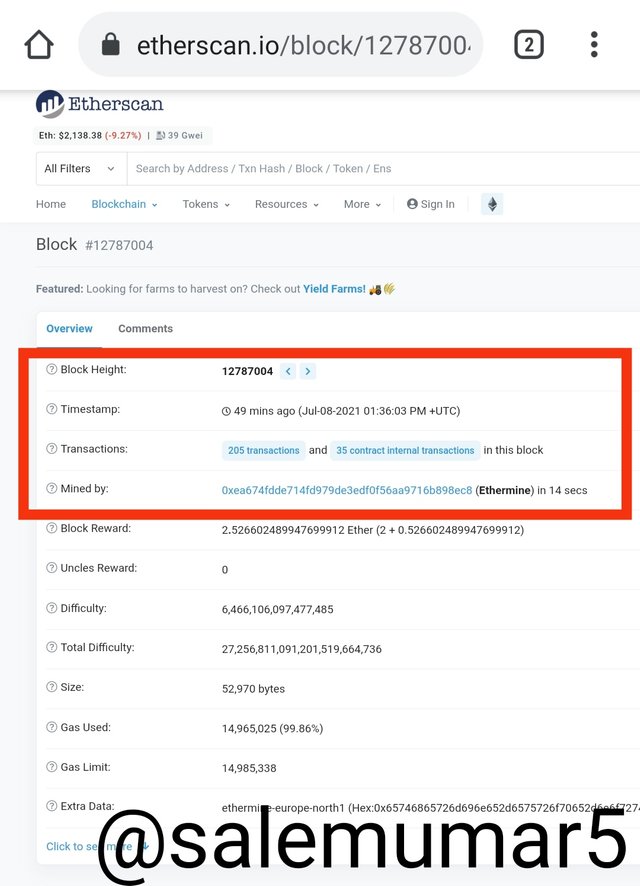
- Scroll down and click on see more
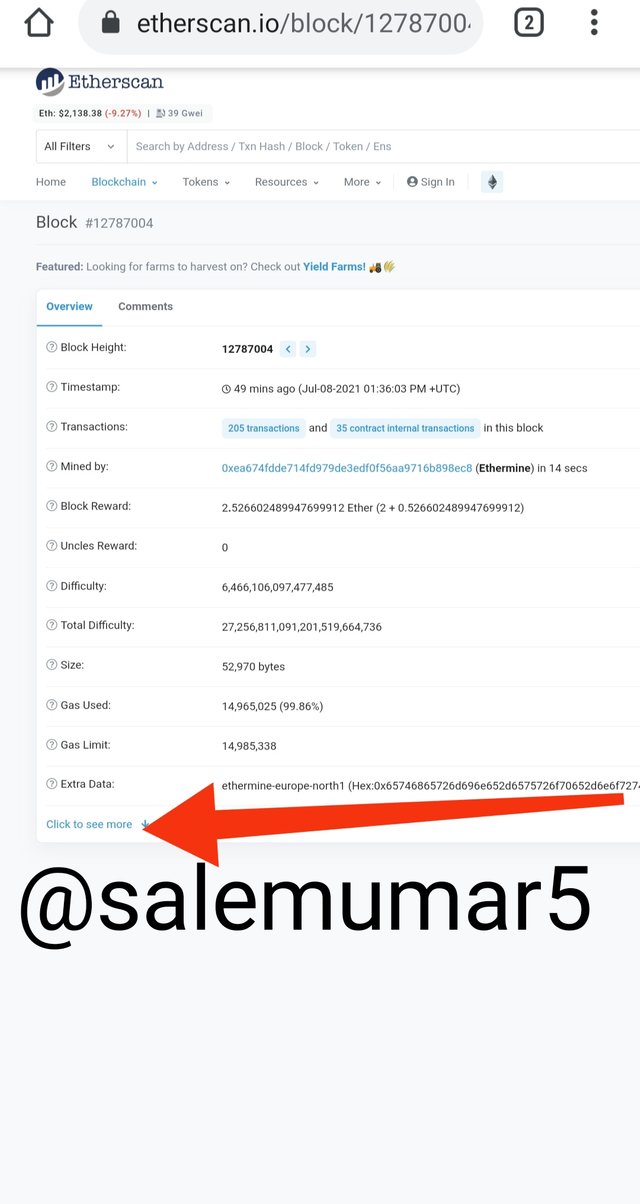
- From that data I extract and found the Hash.
Hash0x473a7e92c8dcc58dcb6bf341b16741ec838e635e0d7411c27db6fdbd9c6841d1
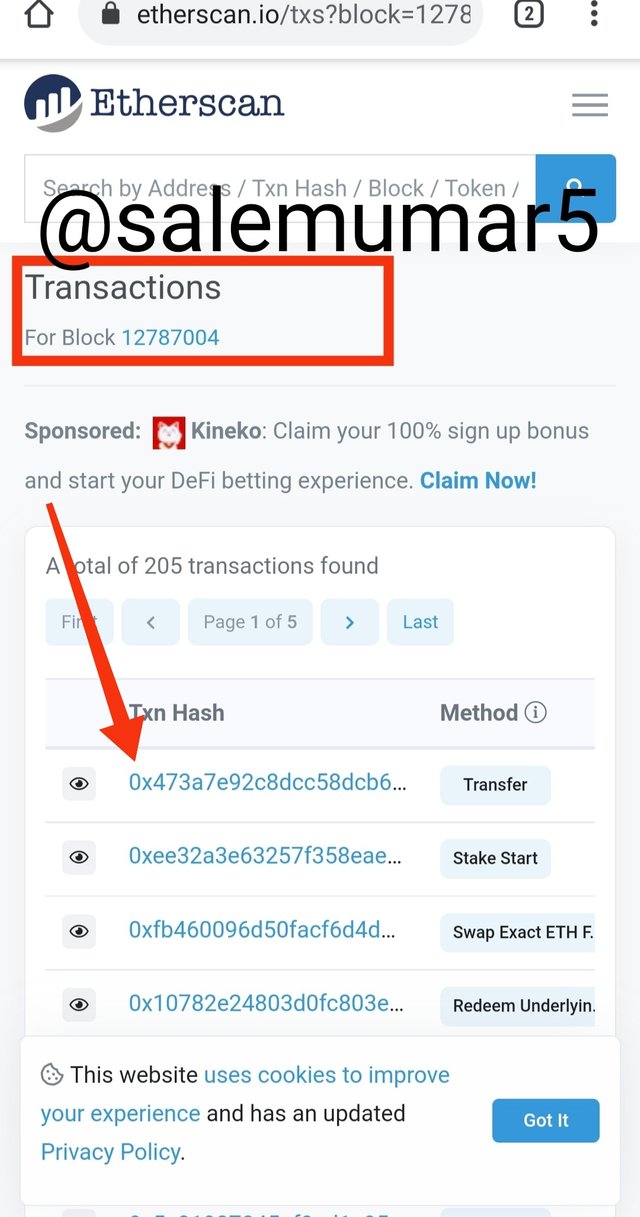
- In the screen shot you can see the no of transaction click on that.
- There you can see details in the last transaction.
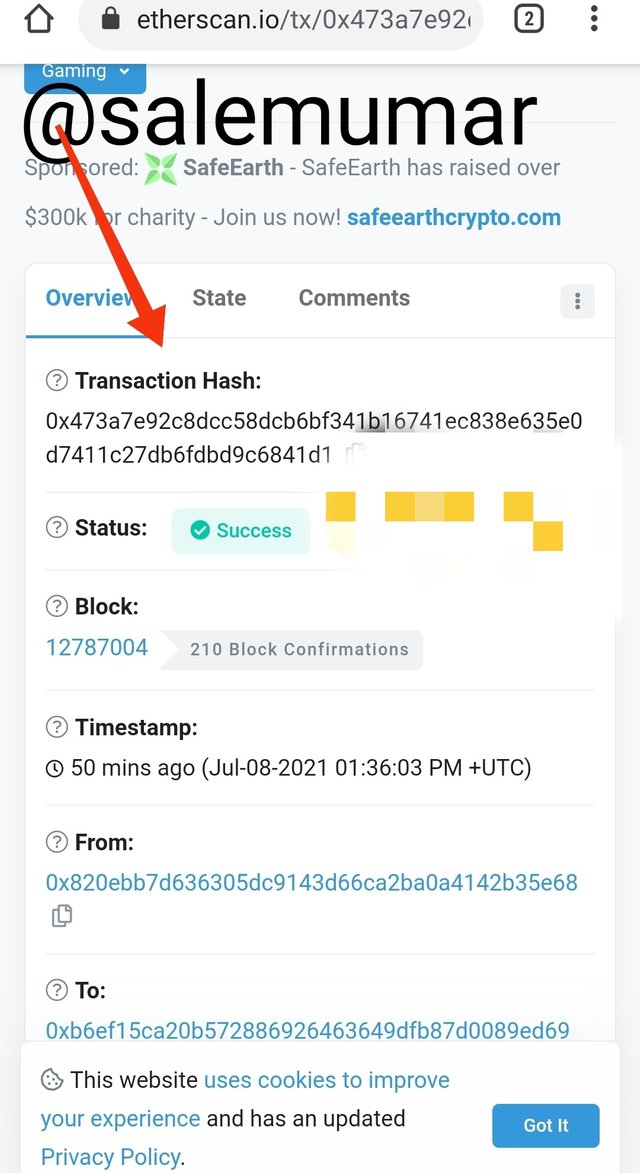
- There you will see the transaction hash graph.
4.- In your own words explain the difference between hash and cryptography.
GENERATING HAS GRAPH:
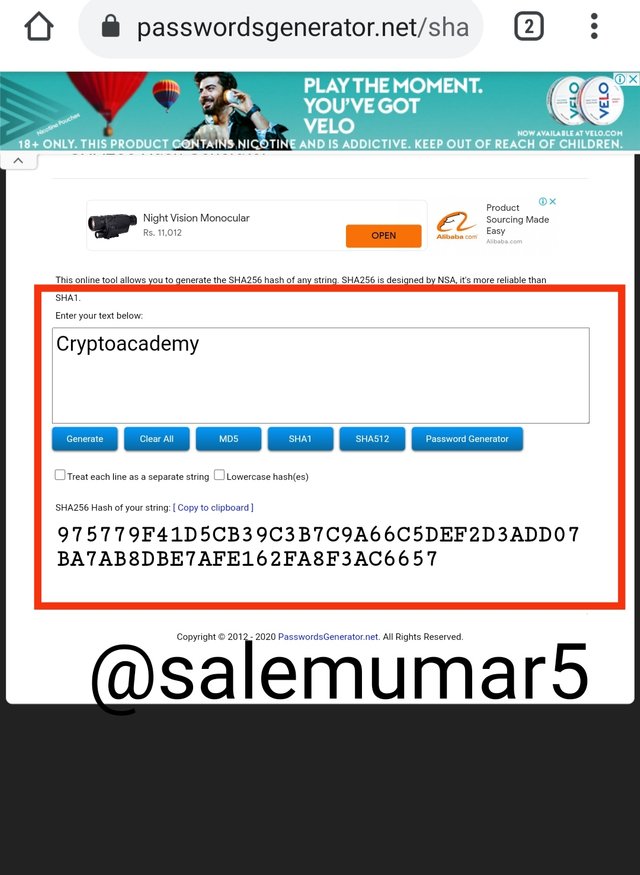
Entering '' CryptoAcademy '' in the assigned website, we obtain the following
Hash:
(975779F41D5CB39C3B7C9A66C5DEF2D3ADD07BA7AB8DBE7AFE162FA8F3AC6657)
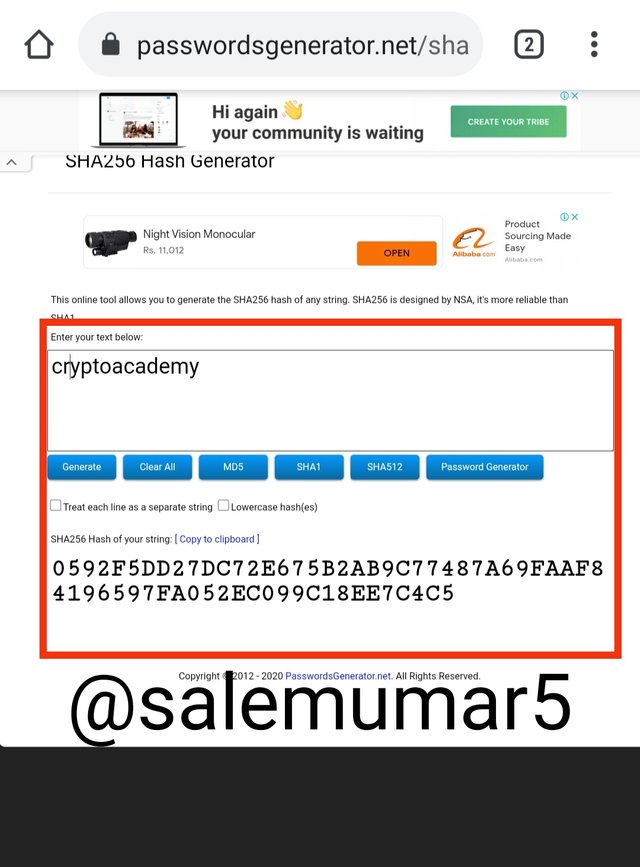
Whilst of entering '' cryptoacademy '' in the assigned website, we obtain the following
Hash:
(0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5)
You can see that while writing same words which originated two different inputs. Two different types of outputs or Hash, resulting for '' CryptoAcademy '' the Hash you can see below.
Although the main fact to notice that the inputs were totally different both output obtained from se of characters from SHA -256. So using SHA 256 ALGORITHM, the number of character of input and the generated output will having same number of digits that is 64.
DIFFERENCE:
The output or hash output of the data will be the same and same alphanumeric characters. Whilst in cryptography is ain't such that.
The hash graphs verify tha data, an encrypted message having the function of transmitting a message safe and sound.
The hash graphs having more potential with blockchain while Cryptography is through out the market mania.
In cryptography the information can be originate ot its original state to get the main of original information. Whilst hash can't do such act and ain't revert the data.
In cryptography contains hide information whose size changeable and having a lots of number digits, whilst hash having an a specific no of digits the length and coding depend in SHA where it is formed.
Your all homeworks looking so good. You working so hard. It seriously is so tough to manage the time for writing the homework along with university work.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit