
Owing to various security measures to protect against email phishing, the scammers have tried other innovative ways. Researchers have found another phishing campaign on the rise that exploits QR codes. This way, the attackers tend to escape any URL analysis and bypass security controls.
QR Codes Phishing Campaign
Researchers from Cofense have noticed a new phishing campaign used to trick users. This campaign exploits QR codes to evade security measures. They have discussed their findings in detail in a blog post.
As revealed, the new phishing campaign makes use of QR Codes instead of the conventional method of using malicious URLs. This technique aids the attackers to elude URL analysis by various products.
The phishing attack begins after an email with the subject line “Review Important Document” reaches the victim’s mailbox. The email appears as a usual SharePoint email, which bears a QR code in the message body. The recipient then needs to scan the QR code to view the supposed document.
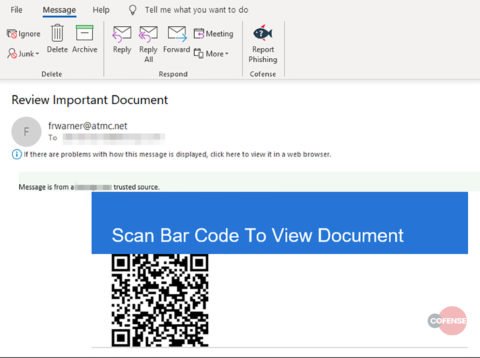
Source: Cofense
This embedded image with the QR code actually contains the URL to the malicious site. When the victim scans this code via their smartphone, the URL then opens on the victim’s smartphone. (Most recent smartphones directly open web links in the default phone browser.) The victim then sees a fake SharePoint website asking to log in via AOL, Microsoft, or any other account.
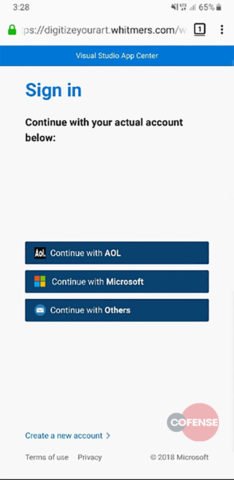
Source: Cofense
And this is it. When the user enters their login credentials, the attackers seamlessly get the username and password to misuse in any preferred manner.
Ensuring Protection Against Phishing
We have already reported a few phishing scams employing various techniques lately, including the abuse of Google Calendars and encrypted emails. Nonetheless, what makes this one different, and potentially more harmful, is the use of QR codes. As stated by the researchers,
By enticing the victim to pull out their smartphone and scan the QR code the attacker manages to evade standard corporate security controls. Secure email gateways, link protection services, sandboxes, and web content filters no longer matter because the user is now interacting with the phishing site in their own security space: their mobile phone.Furthermore since the victim receives the phishing email on the corporate or business email account, the victim is likely to enter the credentials for the corporate account. Thus, enabling the attackers to pilfer corporate account credentials.
The phishing emails also bypass Symantec Messaging Gateway, as revealed by the researchers.
This attack was observed passing through an environment utilizing Symantec Messaging Gateway. When scanned, the message was deemed “Not spam” by the system.It becomes further important for users to be careful while handling such emails. Checking the sender’s email address, and avoiding to enter login credentials on any website are just some of the many steps necessary for protection against phishing.
Let us know your thoughts in the comments.
Posted from my blog with SteemPress : https://latesthackingnews.com/2019/07/03/new-phishing-campaign-exploits-qr-codes-to-bypass-security-controls/
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://latesthackingnews.com/2019/07/03/new-phishing-campaign-exploits-qr-codes-to-bypass-security-controls/
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Yeah I have heard about it! Nice explained, resteemed ;-)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit