
COVID-19 pandemic might be a nightmare for economies and individuals worldwide, but for some threat actors, it is a goldmine. The ransomware industry is on hype as cyberattacks have increased dramatically during the lockdowns.
The risk of ransomware – or in other words malicious software used to infect the computer, encrypt the files, and demand payment for the data unlocking – significantly increased as a result of a massive shift to remote working.
Due to less protected home IT and internet connection, we became more vulnerable to malicious attacks. As businesses had to adapt to the new pandemic conditions and cut their budgets, many organizations were forced to change their traditional working models. This also increased the vulnerabilities of their IT systems.
The incredible growth
Ransomware attackers go after the high-value data and sensitive information. They use a type of malware that infects a device and then proceeds to encrypt the data, denying the victims’ access to their files. The malicious actors then demand the payment of a ransom in exchange for the decryption key.
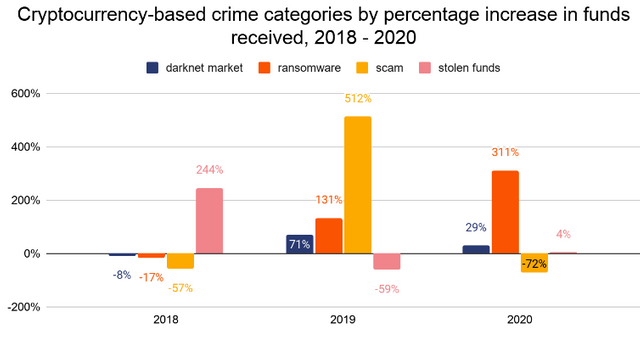
In times of pandemic ransomware attacks started to harm companies and institutions at unprecedented rates. Ransomware-related incidents increased by 311% during the past year, stated blockchain data firm Chainalysis in its annual crypto crime report 2020.
According to Chainalysis, the ransomware demand payments accounted for under $350 million of all darknet funds. However, the real damage done during the past year could reach up to $20 billion due to economic losses businesses and governments experienced when they were taken offline in attacks.
Simultaneously increased the amounts of the ransomware demands. They entered the six-zero or even seven-zero zone. The average ransomware payment demand was $230,000 in the third quarter of 2020. This is 30% more compared to the second quarter.
Bitcoin remained the most popular payment method and accounted for almost 98% of all ransomware demand payments.
What changed?
Historically ransomware attackers were less organized and more dependent on circumstances and luck: they employed massive spam campaigns and distributed thousands of emails infected with malware. When opened, this malware hit both corporate and private computers.
But in recent years the landscape of the ransomware industry has changed. The threat actors started to operate like businesses and their working model shifted from random success to planned, sophisticated and targeted attacks.
The criminals are now accurately choosing their victims and targeting organizations, businesses, and also individuals that are able to pay large amounts to redeem their data.
Ransom attacks are now more advanced and create bigger damage. Half of the ransomware cases employed data exfiltration as a tactic, says CoveWare, a firm that helps businesses with payment support and data recovery after a ransomware incident. According to them, the threat to release exfiltrated data is the main factor used to make victims engage with the hackers.
Besides that, the cybercriminals conduct more extensive intelligence operations to detect potential victims and their sensitive data before the encryption, which also evolves and becomes more challenging.
The methods
Speaking about the ransomware attack methods, cybersecurity experts agree that the most common ones are: sophisticated infected exploit toolkits, malicious email attachments, and email links.
The exploit toolkit usually activates when the victim opens the website, where malicious code is hidden. The same happens with the emails impostering trusted institutions that have the infected attachments or links in the body of the email. When opened or clicked (in the link’s case) the malicious file is unknowingly downloaded and infects the device.
However, in recent years, malware-free attacks became a fast growing threat. A malware-free attack means that cybercriminals do not install ransomware on the victim’s device via infected files or software. They rather enter the organizations (e.g.by using stolen identities) and deploy the network’s own tools against it to implement an attack.
The key targets
The cybercriminals seek victims that seem more likely to pay or to do it fast. Certain types of organizations fall under this description, for example, healthcare institutions, that hold a lot of their patient’s data and need immediate access to them.
According to cybersecurity experts, the healthcare sector saw incredible growth in ransomware attacks last autumn. Healthcare organizations including multiple hospitals were the main target, hit by 440 attacks each week in October, and by 626 attacks in November 2020.
CyberEdge agreed in its 2020 Cyberthreat Defense Report that the governmental sector was the most targeted sector in 2020 in the United States with 15.4% of all reported attacks. The manufacturing, construction, and utility sectors were the next most attacked victims.
The companies from such sectors manage massive amounts of data. Industrial control systems (ICS) manage critical operations in manufacturing and mass-production and might have devastating consequences for the supply chains when stopped. Restoring the data might be costly and difficult, which makes certain organizations much easier targets that are more likely to give in to ransom demands.
Furthermore, many of the ransomware victims were small to medium-sized businesses, mostly because of their lower cybersecurity defense possibilities compared to the wealthy large corporations.
From the technological point of view, hackers are seeking targets that have weaknesses in the security systems. Some of these weaknesses are fundamental, like the use of outdated systems, ignoring software updates, and not fixing security vulnerabilities and other bugs right after updates appear.
On the other hand, the human factor is another biggest issue for both the public and private sectors. While hackers use phishing, and social engineering techniques to compromise networks, and the lack of overall cybersecurity awareness and skilled staff is the vulnerability hackers exploit.
Who is behind ransomware attacks?
Blockchain analytics Chainalysis followed the ransomware payment moves and discovered that “the ability to cash out ransomware proceeds is supported by the owners of a very small group of deposit addresses.” The small group means the top 25 ransomware deposit addresses.
Perpetrators behind ransomware crimes are highly capable of hiding their identities. However, the same analytical firm reported the main categories of ransomware attackers a few years ago: the governments and groups of organized crime.
Speaking about the governments, experts agree that heavily sanctioned countries are the most likely to be behind the attacks.
The well known NotPetya and WannaCry ransomware cases originated from the intelligence services of Russia and North Korea. Iranian state-funded hackers were identified on various ransomware attacks against Israel’s companies. China-linked cyberspies get exposed in multiple ransomware attempts on governmental and private sector entities around the world.
The goals behind government-linked attacks vary. In the case of North Korea-related ransomware attacks, the goal was clear – generate additional funds for the country’s budget. But more often state-funded attacks have other tasks than economic profit: disruption and chaos to reach their geopolitical goals.
Organized crime groups use ransomware attacks mostly for financial gain. Intellectual property (IP) here is one of the best paying-off ransomware targets as revealing it could have immeasurable consequences.
Do organizations pay ransoms?
While statistics are difficult to find, organizations do pay the ransom. More and more companies disclose they have been attacked and succumbed to the blackmail.
Last year 57% of the attacked organizations agreed to pay the attacker’s demands to regain control over their data. This is 12% more compared to the 45% of 2019 and 38% of 2018.
Almost 73% of the small businesses that were increasingly attacked by ransomware actors, admitted to having paid the ransom. The most popular payment demands varied among the $10,000 to $50,000 range. 13% of the victims paid more than $100,000 as a ransom demand.
The criminals behind Ryuk ransomware are said to generate over $150 million worth of Bitcoin from the victim’s payouts. Ryuk is one of the most (if not the most) profitable ransomware gangs, that is accountable for nearly three-quarters of all attacks against the healthcare sector. The Russian-speaking attackers behind the Ryuk demand higher ransom payments compared to many other ransomware gangs.
Unfortunately, paying the ransom does not guarantee that the stolen information will be restored and not leaked. Only 17% of the victims who paid ransom recovered only a part of the encrypted data. And multiple ransomware criminal groups demanded a second payment from their victims after they had paid the first one.
However, the legal and even political scrutiny in increasing in the United States and the legality of paying ransomware demands here might come to an end. Last year the US Treasury’s Office of Foreign Assets Control (OFAC) informed that ransomware payments might breach international sanctions, money laundering, and terrorist financing laws. This means it can be illegal for companies to pay for criminals of ransomware attacks and that the fact may even impose civil penalties in the future.
Originally published on Daily Coin