In the recent years, blockchain community has been bombarded with new projects every day. No matter how much you think you are familiar with the latest technology, there is always something brand new on this market; and it is extremely difficult to keep up. Most blockchain technologies differ in one principal thing, Consensus Algorithm. So let’s dive into what consensus algorithms actually are, followed by why and how they were assembled.
As we all know, it all started in 2008, when bitcoin was born. The term “Proof of Work” or PoW was first coined an formalized in a 1999 paper by Markus and Ari. Bitcoin used Proof of Work (PoW) which is, by the way, older than bitcoin. Proof of Work (PoW) might not be the most “perfect” consensus algorithms out there, but it paved a way for all other protocols. It made people think about all the possible ways there could be for transaction of money on a public ledger without involving a third party.
PoW (Proof of Work)
It works on the sole idea of competition between the miners to gain rewards. Who doesn’t want to take part in a competition, right? But, there is a little catch i.e. it needs a lot of power consumption.
Miners have to solve complicated mathematical problems that require a brute force method.
Once a miner solves it, he announces his win to everyone in the system, and is rewarded.
Types of Mathematical Puzzles:
There are several examples of the mathematical puzzles, some of them are:
Hash function:
This puzzle, once solved, gives the input of a function if the output was known.
Integer factorization:
This gives a number as a multiplication of two numbers.
Guided tour puzzle protocol:
This requires solving hash functions for nodes in a defined manner if a server suspects a DoS attack.
Used by:
Bitcoin, Litecoin, Ethereum, Bitcoin Cash, Monero, Bitcoin Gold.
There was a big uproar about the power consumption of this algorithm, which leads to different variations of it that tries to solve the biggest con of the PoW.
PoB (Proof of Burn):
Proof of Burn is usually known as Proof of Work minus the energy waste.
It works on the simple principle of burning virtual tokens which helps the miners to build a block.
Process:
The process is as follows:
This is done when miners send their coins to an address known as eater address that consumes the coins. Note that the burned coins are the only consumed resources in this process.
Once coins (they could be thought as mining rigs) are burned, the miners are granted their mining rights.
More the coins burns, more the miner will have his rights. This characteristic of PoB resembles Proof of Stake to some extent.
Used by:
Slimcoin, TGCoin.
PoET (Proof of Elapsed time):
PoET is the consensus algorithm that is used by permission based blockchains.
This consensus is based on the fair lottery problem meaning every single node has a fair chance of winning the mining rights.
The process is as follows:
The nodes have to wait for certain time (thus the name) to gain mining rights.
The time is chosen on the basis of the random numbers generated by the nodes themselves.
The node with the shortest wait time wakes up and commits a new block to the blockchain.
Used by:
HyperLedger, Sawtooth.
PoS (Proof of Stake)
PoW has been a ground breaking algorithm with some of the best implementations up-till now but it has a lot of shortcomings, the most prominent and controversial to be the high energy consumption. Hence, the need to evolve arised and that’s where PoS comes in!
How it differs?
Stake based.
No mining rewards.
Lesser energy consumption.
It is simply a stake based system. This actually assigns mining power based on the number of stakes owned by any individual node in the network. The stakes are based on the amount of coins owned by the nodes. The more coins someone holds, the more is their stake in the network. The ones with the maximum stake can mine and verify the blocks and transactions.
PoS is not reward based, so removes the competition between the miners. In return of mining a block, the block producer gets the transaction fee in return for their services.
Everybody gets to verify transactions directly proportional to their stake in the network. The problem that arises here is that those who hold the most stakes will always be the first ones to get a chance for verifying a transaction.; hence the ones with the least stake may never get a chance to verify any transaction...
To solve the issues existing in PoS the following protocols are built with different systems to reach consensus.
Used by:
BitShares, Stratis, PIVX, NavCoin (NAV), Cardano (ADA)

DPoS (Delegated Proof of Stake):
For achieving consensus in the network it uses repute of the nodes and an actual voting structure in a democratic way.
Process:
The process is as follows:
Everyone who has a stake in the system takes part in virtual voting to select the delegates.
These delegates then secure the network and verify the transactions for the new block. It focuses highly on scalability, efficiency and speed.
Though, DPoS might be forgoing decentralization for scalability.
Used by:
EOS Lisk, ARK, BitShares.
LPoS (Leased Proof of Stake):
The problem with normal PoS is that small-holders with minimum balances cannot stake a block.
Process:
Leased Proof of Stake gives a solution for in this way:
As by its basics, the smaller miners will lease their balances to the staking nodes.
The funds generated by lease are in control of the holder. They can spend it or move it as per their wish. Once the holder moves the leased balance, the lease ends.
The leased coins increase the stake of the staking node which increases its chance of being selected for the verification of blocks.
The rewards received are then divided among the leasers proportionally.
Used by:
Waves platform.
PoWeight (Proof of Weight):
PoWeight tries to solve the same problem (holders with more tokens have more stakes in the system) PoS possess.
Proof of Weight tries to overcome it in this way:
Instead of using the system of stakes, a system of defined weights is used in order to identifying the nodes that will verify the blocks in the network.
The weighting criteria might differ for different blockchain networks.
It focuses on customizability and scalability.
Every user has a weight assigns to them. Most probably the weights are assigned based on the amount of money which the users hold.
It is not designed to generate passive revenues for the nodes.
Used by:
Algorand, Filecoin, Chia.
PoC (Proof of Capacity):
Instead of changing numbers in block headers and hashing, PoC introduces a new mechanism.
Process:
The process is as follows:
It works by plotting hard drives of all the interested nodes. They compute and store multiple solutions on every willing node’s hard drive. This is done before the mining game starts. This works like a lottery system.
Every solution has a different speed. If your hard drive has the fastest solution to the present block’s problem then you will win and get the right to verify that block. Same happens for every block.
It is all based on luck. The greater number of plotted solutions on hard drive means a greater chance to win block verification.
Used by:
Burstcoin, Spacemint.

POW+POS
PoA (Proof of Activity):
Proof of Activity starts like PoW with miners trying to solve the mathematical calculations to get rewards.
Process:
The difference is explained through this process:
The mined block doesn’t contain transactions, just the header and mining rewards address.
Once this process is over, the system switch back to PoS. Header helps in selection of random group of validators to sign the blocks.
These validators are the coin holders. More the coins a validator has, more will be the chances that he will be selected to sign a new block.
Once all the validators sign the block, it will be considered as the new block in the blockchain system.
Used by:
Decred.
PoI (Proof of Importance):
PoI recognizes that the how much tokens one have shouldn’t be the only determining factor for the value of the nodes.
Process:
The process of this algorithm has these characteristics:
How much activity one node does is the better judge of who should have the most stake of the system.
This algorithm uses PoW in combination with PoS, with PoW coming first followed by PoS.
Used by:
NEM.
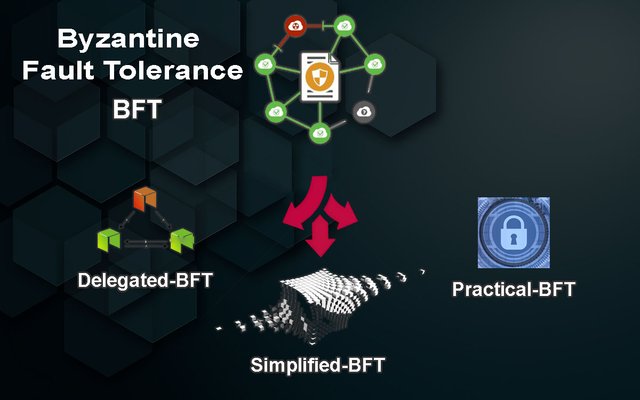
BFT (Byzantine Fault Tolerance)
Byzantine Fault Tolerance is the characteristic of fault-tolerant system that tolerates the class of failures that belongs to the Byzantine Generals’ problem.
There are several consensus algorithms based on this dependency:
PBFT (Practical Byzantine Fault Tolerance):
The pBFT tolerates malicious nodes by providing a Byzantine state machine replication by assuming that there always be the nodes failures and those nodes can spread manipulated messages.
The algorithm is devised to work in asynchronous systems. It is optimized to be high-performance with an impressive overhead runtime and only a slight increase in latency.
For this algorithm to work, an assumption is made that the malicious nodes cannot exceed one third of the total nodes. If the total number of the nodes is large, it will be highly unlikely for the malicious nodes to reach one third of that amount.
Process:
The process goes like this:
Client asks the main (leader) node to invoke an operation.
The leader asks the other (backup) nodes to execute the request; which they do and then send reply to client.
The client awaits almost one more than the total faulty nodes’ reply and expects the same result.’
For this process to occur, it is agreed upon that all nodes are deterministic, and they start at the same state. The final results depend on what all honest nodes agreed on.
Used by:
Zilliqa, HyperLedger.
DBFT (Delegated Byzantine Fault Tolerance):
Delegated Byzantine Fault Tolerance works in the same way as the country’s governance system.
This method is similar to PoS rather than PoW, by utilizing voting system to choose delegates.
Process:
DBFT works like this:
Citizen votes for delegates which do not depend on the number of tokens one hold.
One of the chosen delegates is selected at random to be a speaker.
Their job is to keep track of all the transactions that are being made on the system which is then recorded on the public ledger.
After that, the speaker proposes his own block ,which he sends to all other delegates for confirmation
At least ⅔ of the delegates should approve that block to be added on the public ledger.
Used by:
NEO.
SBFT (Simplified Byzantine Fault Tolerance):
In simplified Byzantine Fault Tolerance (SBFT), there is only one block generator that collects and verifies the transaction into a new-block proposal.
Process:
The process goes like this:
The generator applies rules that have been agreed upon by all the nodes to the blocks and all the blocks signers.
Other block signers then verify that proposed block by signing on it.
All members of the system knows the identity of these signors, so they only accept those blocks that have been signed by them.
One important thing about Simplified Byzantine Fault Tolerance is that nodes and the signers could be deleted at any time, thus ensuring a layer of security to deal with the malicious nodes.
Used by:
Chain
DAG (Directed Acyclic Graph)
A DAG is an information or data structure which can be utilized to demonstrate diverse problems.
It is not a part of blockchain but it offers a solution existing in the current blockchain frameworks.
Process:
Its process is given below:
It is a directed,acyclic and graphic algorithm that runs in linear time.
It follows topological ordering.
This algorithm finds the shortest paths form the source nodes to other vertices.
Every DAG starts from a parent node and has multiple following nodes in it. The last node is supposed to have no kids.
These graphs are never cyclic and cannot refer back to themselves hence are uni-directional.
Used by:
Iota, HashGraph, Byteball, RaiBlocks/Nano.