
This summer I found potential vulnerability in CGTrader Marketplace platform. And tried to remove my data to keep in safe myself. Unfortunately it's not possible, then I started the conversation with support. They are absolutely bozos, support stuff refuse to delete my data and begun to assure me that their security is all right. When I began to explain how a third party can gain access to my data - they just stopped conversation.
It's chat with support below:
Aleksandr Dikov: Documents are stored on the same server as the product images. OK, Can I delete the image of a document, as long as the situation is not resolved?
CGTrader: You can delete it yourself after it is not needed
Aleksandr Dikov: How? I don't see any link or buttons near my scan links in billing profile.
CGTrader: Oh, my mistake
Aleksandr Dikov: We misunderstood each other from the beginning?
CGTrader: No, I understand your concern, but images will stay safe with us
Aleksandr Dikov: Of course, I'm not an expert on network security, but I believe that possible to bruteforce a couple of ID + filename as a minimum . Given that we know that there are stored passports, filenames can be quite predictable. Can I somehow delete the uploaded images, and reload them with hash names. At least they were not able to get such a simple way that I have described?
*** END OF CONVERSATION BY SUPPORT MANAGER***
Then I wrote to the owner and someone with name Mantas Bliudzius answered:
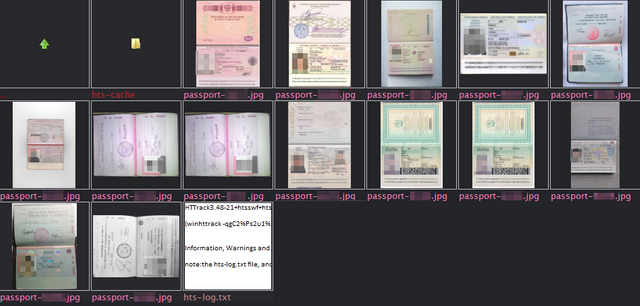
They had added some salts and hashes to the link, in admin panel, but it change nothing, you can just ignore it. And I realized that time of words has gone, we need a clear demonstration and publicity, to affect on the management of the company! I should to say that I don't professional hacker, and next tools can be used by everyone. We need any text editor (or anything else) that could generate links with increment numbers (in my case I just use JavaScript in browser (!!!)) and any program that can save files from list of links (in my case used WinHTTrack Website Copier).
Well, generate links:
https://cgtfiles.s3.amazonaws.com/uploads/attachments/0000/passport.jpg
https://cgtfiles.s3.amazonaws.com/uploads/attachments/0001/passport.jpg
https://cgtfiles.s3.amazonaws.com/uploads/attachments/0002/passport.jpg
...Range from 0000 to 9999 was used in my case. Then just start downloading process in your favorite program.
YES! That's all! In this case 12 users was compromised! ONLY WITH ONE SUPPOSED FILENAME (passport.jpg)!!! But you could to imagine what could be founded with different keywords and more complex scripts.
Thank you for pointing out this vulnerability in our security system. I would like to apologize for failing to adequately respond to your messages and overlooking the technical issue itself. We take the security of private data trusted to CGTrader very seriously, and we are taking significant steps to ensure similar situations do not occur in the future.
This vulnerability in the system has now been fixed. This issue is specific to image document copies provided, and no other digital identity, payments or banking information has been compromised. This issue affected ~30 users, as the issue was actually fixed after your comments in January for all new uploads, except for images uploaded previously. We have notified the potentially affected users so they can take steps to protect themselves. We are also now initiating a full security audit to prevent similar vulnerabilities from arising in the future.
My sincerest apologies once again and I would be happy to respond to all the outstanding concerns.
Dalia, CEO @CGTrader
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit