
Security researchers recently created a proof-of-concept attack against Internet connected lightbulbs, causing breached devices to reach out and infect their neighbors. Propagation continues and spreads itself across the community. This hack highlights the insecurity in one of many IoT network protocols.
Researchers say the worm, which currently targets Phillips Hue lightbulbs, can set off a chain reaction that could compromise devices across entire cities. Right now, the hack only causes the insecure web-connected globes to flick on and off, but this is only a proof-of-concept to show foundational weaknesses. It is likely more advanced impacts and propagation may be able to be developed.
Home Automation Networks
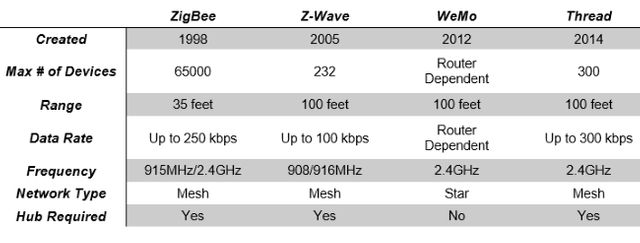
The primary weakness is in the network by which the devices are connected. ZigBee, Thread, WeMo, and Z-wave were developed as home automation standards to allow IoT devices to communicate and be controlled. They have been around for years and complement more familiar WiFi and Bluetooth standards. In many cases these require a hub, which can connect a mix of different products communicating on two or more of these standards. These are popular in homes settings but have expanded over the years and can now be found in business environments. ZigBee and Z-Wave are the most widely used of the ZigBee/Thread/WeMo/Z-wave automation protocols. Z-Wave has more than 1500 products, totaling over 50 million devices in customer’s hands, and ZigBee has over 1000 products. Thread is the newest and unlike ZigBee/Z-Wave, is IP based, which has both plusses and minuses from a security perspective. The Thread protocol was driven by the needs of Google's Nest Labs, Samsung Electronics, ARM, and others who wanted a smart-home networking protocol compatible with IPv6.
Theoretical Attack
The vulnerability research highlights the insecurity of such systems, especially in peer-to-peer or mesh mode. Such configurations can open the door to chain style attacks, like zombie infestations you see in movies. The worm that was created, spreads by jumping direction from one infected lamp to physically nearby neighbors using their ZigBee connectivity. As there is no validation between Philips hue globes, the attack is allowed to spread.
Based upon percolation theory simulations to infect an entire city, researchers believe there is a tipping point where it would take at least 15,000 vulnerable devices to sustain the contagion to spread everywhere. Any less, they suspect the infection would remain compartmentalized to just certain areas and not infect the entire city. Estimates vary, but the total number of global IoT devices may exceed 30 billion by 2020. Many of these will be connected to home automation networks.
Key Points:
- This is a proof-of-concept attack, not yet seen in the wild. It does highlight the risks that entire networks of devices may be compromised and even worse, configured to infect each other.
- A real-world attack could range from amusing flashing lights to moderately inconvenient and costly incidents where devices must be recovered and safety may be put at risk. Impacts will be based upon the types of devices deployed and how they are used. Household convenience devices are less important than those in an emergency room or illuminating a busy intersection.
- The vulnerability research is a motivator for standards bodies to take action in hardening these standards. Future versions, with improved security, may not be backwards compatible in all cases and residual devices would remain susceptible to attack.
- These standards do use some encryption and authentication controls is in place, but as the research has proven, these can be undermined.
- Such attacks are a fear of SmartCity developers, most of which have known this could happen but the long-term security is still uncertain.
The importance of IoT security is currently a hotly debated topic and these additional weaknesses adds to the overall concerns. I expect additional vulnerability research and eventually attacks in the real-world to pursue these aspects of insecure IoT network protocols. Discussions will fuel more scrutiny and the development of better design and security practices as the future of devices will be in control of more facets of our personal lives and business functions.
Interested in more? Follow me on Twitter (@Matt_Rosenquist), Steemit, and LinkedIn to hear insights and what is going on in cybersecurity.
Source: I posted my blog on LinkedIn as well: https://www.linkedin.com/pulse/iot-worms-could-spread-like-zombies-matthew-rosenquist
What can we do to ensure our IoT products are not contributing to the problem or won't be taken advantage of in the future?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This is the only company I know of that is addressing this concern directly:
http://www.mgtci.com/intro/
http://www.mgtci.com/part-1-data-is-increasingly-life-itself -IOT specifically
Luckily, the CEO is John McAfee and the CTO is the white-hat hacker, Eijah! Two solid libertarians! So if you buy their products, you also help put them in a position to restore freedom to the US political system, and then expand it beyond previously-existing levels.
McAfee's brilliant Libertarian Party nomination speech:
Some info on protecting your data using demonsaw, and the digital dead-drop device (3D) --a router that connects only to an anonymized and encrypted "web 2.0"
https://www.youtube.com/results?search_query=demonsaw --more videos on Vimeo, search for Eijah and demonsaw
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
It is a little tough at the moment, as most of the current generation of IoT devices don't have much security built in or are not easily updated/patchable. For the device you do own, make sure you:
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This goes to show how vulnerable we really are, and how hard it is to successfully eliminate threats.
Thanks for the info @mrosenquist.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
So true!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi! I am a content-detection robot. I found similar content that readers might be interested in:
https://www.linkedin.com/pulse/iot-worms-could-spread-like-zombies-matthew-rosenquist
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Down kitty. Yes, I posted this on LinkedIn earlier. Will add the reference. ...good kitty.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit