
I often get the question from SmartNode Operators, "How can I improve my chances of getting a reward"? Well, the simple answer is there is nothing you can do to increase your chances as it is determined by block hash entropy. There is no way to predict when your next payout will be exactly. This is actually good, because if it could be predicted precisely it would be a target for a DDOS attack.
What you can do, however, is take steps to protect your node and keep it from going offline. You can set up monitoring tools to track your SmartNode as well.
One way to do that is to protect your node with a firewall. If you already followed the SmartCash SmartNode Vultr Firewall + 2FA Guide your server will overall be protected and isolated from random or malicious internet traffic. The SmartNode install.sh approach also include ufw firewall rules to limit access to all but the required SmartNode port and an ssh. However, port 9678 is still open, the one that is required for your SmartNode to communicate with the rest of the network. It would be useful to limit traffic going to that port to reduce the impact of an attack on the SmartNode by a DDOS flood.
You can go one step further and add an IPTABLES configuration to limit the type of internet traffic that hits your ports. This can be helpful if someone wants to flood your SmartNode with fake or useless network data in order to overwhelm its processing power to knock it offline. If you're offline for more than an hour, you won't earn rewards and your node position will be reset. The following will replace IPTABLES configuration on the VPS so it's recommended you also use a Vultr firewall for extra layers of redundancy.
I've constructed a set of firewall rules that will limit concurrent connection 2 per ip, 8 per c class network address, limit 3 synchronication packets per ip with in 30 sec, and also limit some tcp ddos packets. It also drops things like UDP packets which are not used by the SmartNode network. Additionally, in case you like using SSH, there are also simple protections for port 22 and 222 (in case you changed the default to that per the SmartCash Smartnode 10 Minute Guide).
This installer is configured for Ubuntu 16.04 and tested on the Vultr VPS. This will overwrite any existing iptables rules. Use in combination with the Vultr firewall is recommended. You can view the code on GitHub Gist here. These were based on rules that were created after a DDOS attack on another masternode network as seen by the fork history on Gist.
The following has been tested on actual SmartNodes on Ubuntu 16.04 on the Vultr VPS. Testing has not been done on other systems. As long as they also use eth0 for the primary network connection it should work okay. You can always backup before installing to test.
Installer Script
This was tested on Vultr Ubuntu 16.04. It should work on other hosts if they use ETH0 for their network connection. A different way to save may be required using this command afterwards: iptables-save
Do the following to download the script and execute it:
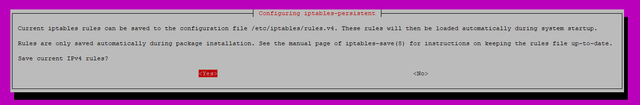
Press "Y" and enter when prompted. Be sure to save ipv4 and ipv6 current rules when prompted by pressing enter each time.
wget -O ./smartnode_ddos.sh https://git.io/vAyem
bash ./smartnode_ddos.sh
https://git.io/vAyem is the shortened link for https://gist.githubusercontent.com/blockchainlibraryorg/186807cbb005fb449c068e71cb119609/raw/4a9f90eecd6c43ba6301ff7145521efc61d929b5/smartnode_ddos
The screen to press enter looks like this:
After you install, reboot and restart your smartcashd:
reboot
smartcashd
That's it! You're done.
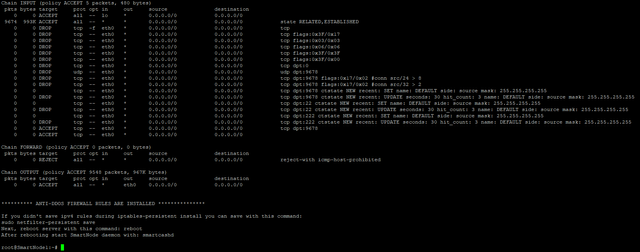
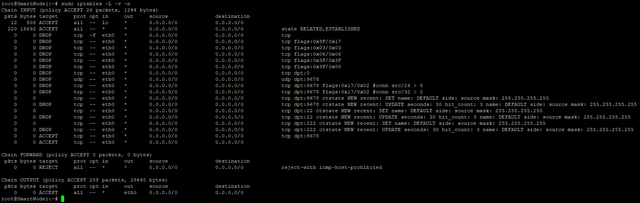
You can do the following to see the new firewall rules.
Check iptables was loaded after rebooting:
sudo iptables -L -v -n
It should look the same as after installing, like so:
You can get more information on the connected node peers with:
netstat -tupn
smartcash-cli getpeerinfo
If you need to, you can restore iptables backup from /etc/network/iptables.backup
sudo iptables-restore < /etc/network/iptables.backup
If you don't like using the git.io or bash scripts, here are manual steps to install.
Saving IPTABLES for Other Hosts
If you are using a non-Vultr host try this command before rebooting to save the iptables.
iptables-save
Manual Steps to Install
- Save current iptables backup to /etc/network/iptables.backup
sudo iptables-save > /etc/network/iptables.backup
- Download new iptables from GitHubGist
wget -O ./smartnode_iptables https://gist.githubusercontent.com/blockchainlibraryorg/186807cbb005fb449c068e71cb119609/raw/74ac1936df738243bc7b0edf1b5bfda3c85097fd/iptables
- Restore iptables using the downloaded ./smartnode_iptables file
sudo iptables-restore < ./smartnode_iptables
- Check the config was loaded into iptables
sudo iptables -L -v -n
- Save the updated iptables to start on bootup by installing iptables-persistent:
sudo apt-get install iptables-persistent
If you didn't save ipv4 rules during install you can save with this command:
sudo netfilter-persistent save
- Reboot your system:
reboot
- Reconnect to console or SSH and check iptables was loaded on boot
sudo iptables -L -v -n
- Load your smartcashd and test it's connecting:
smartcashd
smartcash-cli getinfo
You can get more information on the connected node peers with:
netstat -tupn
smartcash-cli getpeerinfo
If you need to, you can restore iptables backup from /etc/network/iptables.backup
sudo iptables-restore < /etc/network/iptables.backup
Posted from my blog with SteemPress : https://smartcash.blockchainlibrary.org/2018/03/protecting-your-smartcash-smartnode-port-with-anti-ddos-firewall-rules/
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://smartcash.blockchainlibrary.org/2018/03/protecting-your-smartcash-smartnode-port-with-anti-ddos-firewall-rules/
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit