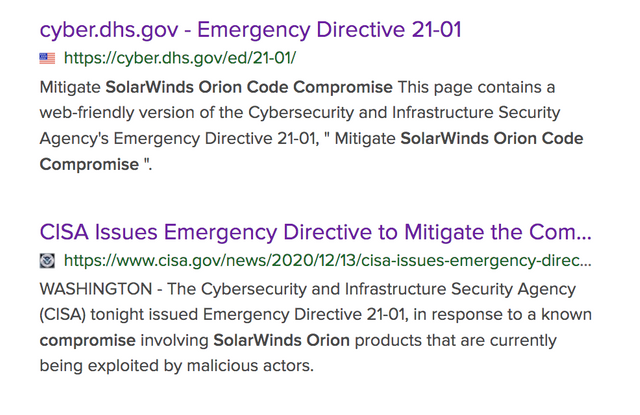
On December 13, 2020 there was an Emergency Directive 21-01
regarding the Sunburst Vulnerability on Dec. 13, 2020
to mitigate Solar Winds Orion Code Compromise. This verifies our systems have been compromised.
Reported by Solar Winds Security Advisory
- SolarWinds was the victim of a cyberattack to our systems that inserted a vulnerability (SUNBURST) within our Orion® Platform software builds for versions 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1
- which, if present and activated, could potentially allow an attacker to compromise the server on which the Orion products run.
- This attack was very sophisticated supply chain attack, which refers to a disruption in a standard process resulting in
- a compromised result with a goal of being able to attack subsequent users of the software.
- In this case, it appears that the code was intended to be used in a targeted way as its exploitation requires manual intervention.
- We’ve been advised that the nature of this attack indicates that it may have been conducted by an outside nation state, but SolarWinds has not verified the identity of the attacker.
So SolarWinds claims they were the victim of SUNBURST. Were they?
Is there more to the story?
Wonder why this happened. . .
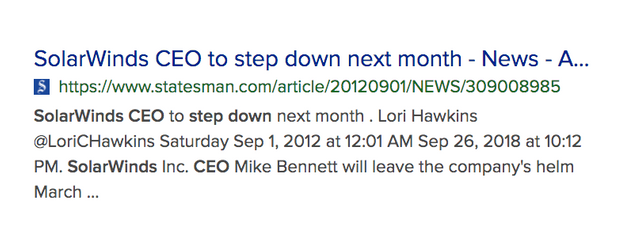
So Mike Bennett stepping down from this Austin based company. That's interesting as word out is he also sold a Lot of his stock.
As reported in the Statesman,
Last month, SolarWinds acquired Dallas-based Tek-Tools Inc. for $42 million in cash and stock. Bennett said that the company’s global expansion, including the addition of a software development team in India through the Tek-Tools purchase, added to his decision.
“We’ve now got operations around the world — Singapore, Ireland, India, New Zealand, the Czech Republic — and it’s hard for me to travel the way I used to,” Bennett said. “I don’t know how you can do this job without being willing to get on an airplane pretty much every week of your life.”
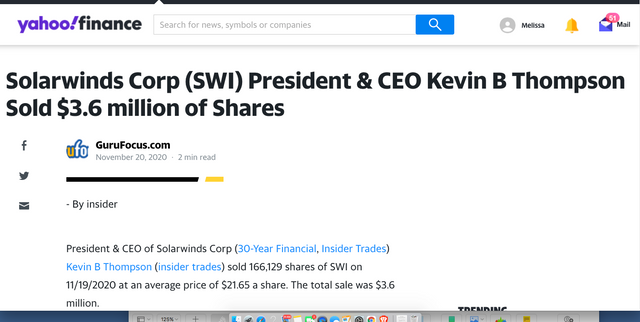
Yahoo Finance speaks of the Solarwinds corporation stepping down and selling stock,
I guess it's Just like the song from the 80's said,
"Someone always playing, Corporation Games"
"Who cares they're always changing corporation names."
"We just want to dance here, someone stole the stage" (who's really in charge of information?)
who counts the money underneath the bar?
Well. ..
"Marconi plays the mamba, listen to the radio, don't you Remember?"
Hmmm. ..I just wonder!
Have a listen and consider what reality is,
We Built this City w Lyrics
Who was Marconi?
Who had the nickname of Black Mamba?
As reported by the History channel,
Guglielmo Marconi was born in 1874 in Bologna, Italy. His father was a wealthy landowner and his mother was a member of Ireland’s Jameson family of distillers. Marconi was educated by tutors and at the Livorno Technical Institute and the University of Bologna.
Did you know? In his Nobel Prize acceptance speech, radio pioneer Guglielmo Marconi—who was much more a tinkering engineer than a scientist—freely admitted he didn't really understand how his invention worked.
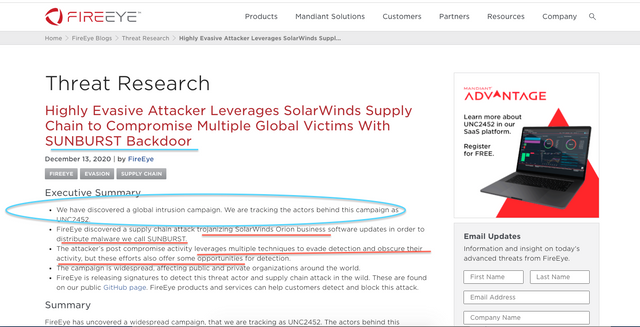
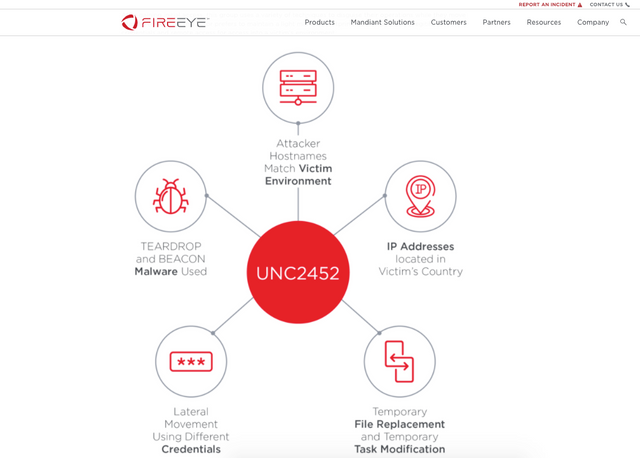
According to FireEye, a Cybersecurity company,
Multiple trojanzied updates were digitally signed from March - May 2020 and posted to the SolarWinds updates website.
FireEye has detected this activity at multiple entities worldwide. The victims have included government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East. We anticipate there are additional victims in other countries and verticals. FireEye has notified all entities we are aware of being affected.
FireEye
- cybersecurity company headquartered in Milpitas, California.
- It has been involved in the detection and prevention of major cyber attacks.
- It provides hardware, software, and services to investigate cybersecurity attacks, protect against malicious software, and analyze IT security risks.
- FireEye was founded in 2004.
In 2013, Mandiant (before being acquired by FireEye) uncovered a multi-year espionage effort by a Chinese hacking group called APT1
In 2014, the FireEye Labs team identified two new zero-day vulnerabilities – CVE-2014-4148 and CVE-2014-4113 – as part of limited, targeted attacks against major corporations.
- Both zero-days exploit the Windows kernel. Microsoft addressed the vulnerabilities in their October 2014 Security Bulletin.
- FireEye provided information on a threat group it calls FIN4.
- FIN4 appears to conduct intrusions that are focused on a single objective: obtaining access to insider information capable of making or breaking the stock prices of public companies.
The group has targeted hundreds of companies, and specifically targets the emails of C-level executives, legal counsel, regulatory, risk, and compliance personnel, and other individuals who would regularly discuss confidential, market-moving information.
In 2015, FireEye confirmed the existence of at least 14 router implants spread across four different countries: Ukraine, Philippines, Mexico, and India.
Referred to as SYNful Knock, the implant is a stealthy modification of the router’s firmware image that can be used to maintain persistence within a victim’s network.
Here is another bit of connecting info if you really want to see just how Deep this goes!
https://steemit.com/techgiants/@artistiquejewels/lenovo-the-chinese-co-that-took-over-motorola-after-google-acquired-it-and-kept-the-patents-lenovo-acquired-more-tech-companies
Also of interest. . .
https://www.vox.com/2018/8/17/17704526/google-dragonfly-censored-search-engine-china
Also in 2015, FireEye uncovered an attack exploiting two previously unknown vulnerabilities, one in Microsoft Office (CVE-2015-2545) and another in Windows (CVE-2015-2546). The attackers hid the exploit within a Microsoft Word document (.docx) that appeared to be a résumé. The combination of these two exploits grant fully privileged remote code execution. Both vulnerabilities were patched by Microsoft.
Same year, FireEye as a Service team in Singapore uncovered a phishing campaign exploiting an Adobe Flash Player zero-day vulnerability (CVE-2015-3113). Adobe released a patch for the vulnerability with an out-of-band security bulletin. FireEye attributed the activity to a China-based threat group it tracks as APT3.
I find this interesting because. . .
Google's is a skunkworks team and in-house technology incubator, created by former DARPA director Regina Dugan. ATAP is similar to X, but works on projects, granting project leaders time—previously only two years—in which to move a project from concept to proven product.
Now it is interesting to note that Regina Dugan 19th Director of DARPA also worked for Facebook.
See more information here and thanks for the archive Hive!
https://hive.blog/sethrich/@artistiquejewels/more-evidence-russians-did-not-hack-the-dnc-reporter-statements-on-seth-rich-a-trail-that-leads-to-crowdstrike-and-a-verified
How about the recent spy stories that have broken regarding Swalwell, a rep from CA and an Ohio mayor involved with what Axios reports as. ..
in contact with a female Chinese spy named Fang Fang, aka Christine Fang, between 2011 and 2015.
Find more information inside of here,
https://steemit.com/republic/@artistiquejewels/update-what-is-happening-in-trying-to-gain-back-our-constitutional-republic-will-the-steal-be-stopped-you-decide
The US news agency AP quotes US officials who wish to remain anonymous, saying this is "the most serious hacking attack in America's history."
According to ISA Cybersecurity,
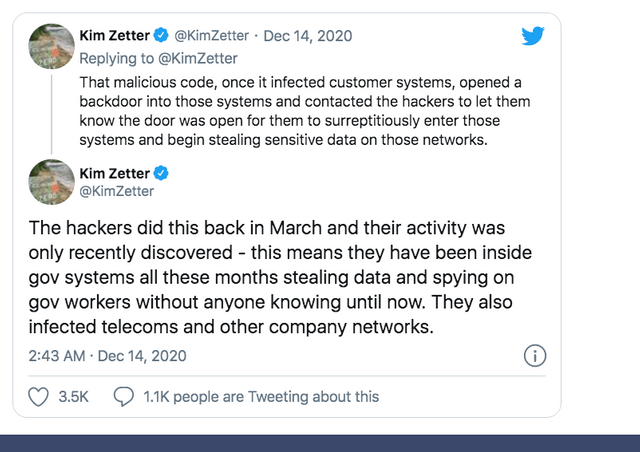
The compromise appears to have been created by cyber attackers who quietly tampered with Orion software updates. The compromised updates contained secret “backdoor” malware called SUNBURST, bundled within legitimate Orion software patches and hotfixes provided to target victims by third parties. Orion software released between March and June of 2020 may have been affected.
According to a detailed analysis by FireEye, the backdoor malware sits dormant after installation for up to two weeks, after which it “retrieves and executes commands, called ‘Jobs,’ that include the ability to transfer files, execute files, profile the system, reboot the machine, and disable system services.” It is believed that this vulnerability is behind the serious email system breach recently discovered at the U.S. Treasury and Commerce Departments.
Very Interesting as we had a technology from Texas pour of the Dominion Voting Systems manual. Have you seen what is on page 11?
Get the breakdown from him including his analysis here,
Scroll down about 1/3 of the way to see what Ron Watkins has to say after pouring over the manual for a week.
So Lines of communication cut and compromised!
An attempt to control Information warfare through Cyberwarfare?
Has it been evidenced?
How about CISA and who all was involved there? Who all was as We Built This City put it. ..Knee deep in the Hoopla?
"Who sunk in their fight?"
Do you remember?
Fired
He left with many others.
The question becomes were these people planted?
You decide.
Economic warfare?
Could POTUS declare all the debts to China null and void since they have engaged in
- biological warfare
- economic warfare
- covert warfare
- unrestricted warfare
This is a possibility as he had seized assets through Executive Order of human trafficking.
Validates imposing sanctions in foreign interference in United States Elections.
Could this translate into the International Emergency Powers Economic Act?
50USC Code 1701
https://codes.findlaw.com/us/title-50-war-and-national-defense/50-usc-sect-1701.html
Does this give our Commander in Chief the authority to stop it?
Does this give our Commander in Chief
See further information in a connecting article in sources below.
Would you know if it happened or what it be classified?
Do you Let the enemy know your hand? Or is it sleight of hand. . .you decide! You're the judge!
The Judge - twenty one pilots lyrics
Have these threats been evidenced before? Once again, look over what we know and You decide.
Just how deep does this really go?
The web is vast as you know!
Post compromise activity and detection opportunities
In section 3553 title 44 U.S. code authorizes the Secretary of Homeland Security in response to
- a known or reasonably suspected information security threat
- vulnerability or incident
- that represents a substantial threat to the information security of an agency
- to issue an Emergency Directive to head of an agency
- to take lawful action with respect to the operation of the Information System
It's still CIA vs DIA
likely also the war between NSA and DoD
SolarWinds Orion products are currently being exploited by malicious actors.
Places like CNN are once again attempting to say Russians. Does that help them keep the focus off of China and all the evidence of these Dem should be leaders and their evidenced deals with China? Not the good people of China, but rather the corruptors in China's government once again.
For Example, when you look at government sites, they give the facts that are verified, but when you look at CNN's site concerning SolarWinds, you get speculation and attempts to distract from evidence. Why do you suppose that is?
According to CISA (Cybersecurity and Infrastructure Security Agency)
the breach of SolarWinds poses an unacceptable risk to Federal, Civilian, Executive branch agencies and requires Emergency Actions.
Current exploitation of affected products on major network systems have
- the potential of compromise on agency systems
- grave impact of a successful compromise as stated here,
https://us-cert.cisa.gov/ncas/current-activity/2020/12/13/active-exploitation-solarwinds-software
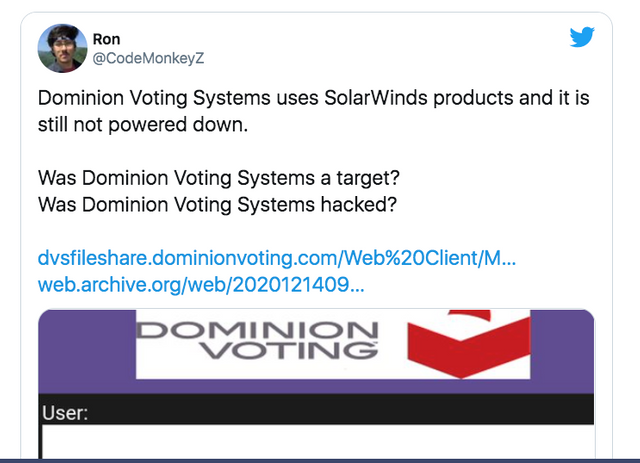
According to InvestmentWatchBlog in an article from Dec. 14, 2020,
Dominion uses SolarWinds, guess what just happened
Think about it, these hackers gained access in March and they had access to pretty much all govt communications, databases and our voting systems. This was NOT Russia. This was either deep state or China. My money is on China.
Take a look at what Antrim's statement was as reported locally by 9 and 10 news. Do you suppose this local station is one of the Approved links from the "powers that be" and overlords of your information allowance? I guess we will see as it completely Tests their Narrative they are so desperately trying to push!
9 and 10 News reports,
The public release of the audit was authorized by Judge Kevin Elsenheimer. It takes a closer look at the voting operation system used to count the ballots in Antrim County.
Read the full audit done by the Allied Security Operations Group: in sources below where the entire pdf link is given
ASOG concludes,
“The Dominion Voting System is intentionally and purposefully designed with inherent errors to create systemic fraud and influence election results.”
And adds,
“The system intentionally generates an enormously high number of ballot errors.”
While the county clerk stated that the election night result of the vote flip was human error, ASOG says it’s instead due to “machine error built into the voting software designed to create error.”
So basically anyone including the cleaning crew. . .in other words Anyone with access,
All they had to do was go in, put a thumb drive in, download and crack the code later.
Sure is interesting an Elections Warehouse was broken into in Philadelphia and MSM desperately tried to downplay it, though Dem leaders were Not downplaying Election interference in 2019 as was evidenced by Elizabeth Warren and other Dem leaders letters which spoke about Dominion Voting Systems. Interesting right?
Laptop, USB drives stolen from Elections Warehouse
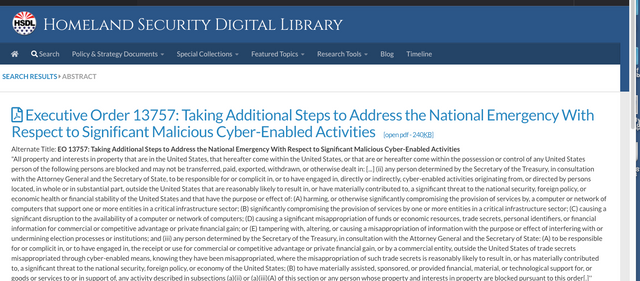
Here is that Exec order right here,
https://www.hsdl.org/?abstract&did=797652
Where Obama states,
- The Executive branch operates it's Information Technology on behalf of the American People.
The President will hold heads of Executive Department Agencies ACCOUNTABLE for managing Cyber security risk to their enterprises.
Oh, Obama wasn't done there. .
In addition because risk management decisions made by heads of can affect the risk to the Executive branch as a whole, international security is also the Policy of the United States to manage cybersecurity risk as an Executive Branch Enterprise.
In July of 2018 this Imperative was strengthened by President Trump. . .
to include requirements to insure that U.S. Elections, Systems, Processes and it's people were not manipulated by foreign meddling either through electronic or systemic manipulation, social media or physical changes made in software or supporting systems.
Very Clear don't you think?
So ask yourself, what role does DNI now play?
So it operates it's technology on behalf of the American People?
Who is sworn to act in the interests of We the People?
President TRUMP!
Can a weapon formed against you be used against you if you are the Sons and Daughters of God?
This is how God reigned in on it. . .
Isaiah 54:17
“No weapon that is formed against thee shall prosper; and every tongue that shall rise against thee in judgment thou shalt condemn. This is the heritage of the servants of the LORD, and their righteousness is of me, saith the LORD.”
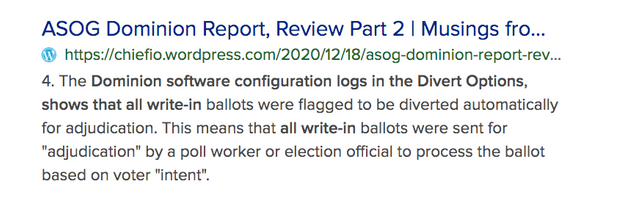
Dominion voting system software configuration logs in the divert options shows that all write in options were flagged to be diverted automatically for adjudication.
If not familiar please check 11 Alive News,
Thereby, allowing Any Operator to Change Those Votes!
On 12/08/2020 Microsoft issued 58 Security Patches across Ten Plus Products, some of which were used for Election Software
- of 58 Security Fixes, 22 were patches to remote code exec Vulnerabilities.
- in reviewing the Election Management System Logs it was evidenced there were config errors through the set-up election and tabulation.
- The bottom line. . .This Calibration Rejects the Vote!
This provides Direct Proof to tamper with evidence.
President Trump's Executive orders, initiated by President Obama are Rock Solid!
He will be able to meet with
- DNI
- JASOC (Joint Special Operations Command)
- CYBERCOM
and other Special Operations Intelligence Units and come up with a solution if the judicial and justice depts. are so corrupted and infiltrated.
Go WHITE HATS!
The First 7 to enlist in the U.S. Space Force graduated from basic Military Training on Dec. 10th, 2020

Head of the Space Force sates,
- “I need you to be bold. You will help us build this service from the ground up. You will help us define our warfighting culture.
- You will build the Space Force as the first digital service. You will lay the foundation of a service that is innovative and can go fast in order to stay ahead of a significant and growing threat, and you, if deterrence fails, will fight and win the battle for space superiority which is so vital to our nation, our allies and our joint and coalition forces,” he said, adding that “the nation expects you to deliver dominant Spacepower.”
Will they take the place of agencies that have been corrupted and infiltrated like CISA, and like Esper head of DOD have proven to be?
Only Space Force and Air Force which had not been compromised.
Do you Remember the Weakening of the air force and the generals directly let go that didn't support a nefarious enemy?
A loyal core has been built of those who have Not Been Corrupted or Bribed by the globalist enemies.
https://www.myairforcebenefits.us.af.mil/News/US-Space-Force-makes-history-at-basic-military-trainin
https://chiefio.wordpress.com/2020/12/18/asog-dominion-report-review-part-2/
Who gained access to a Backdoor into various sectors years ago?
How about that QRS11 Gyrochip?
Do you remember how that ties into Kobe Bryant?
How about that helicopter he was on and where he and his daughter were laid to rest?
All coincidence? You decide!
THE HELICOPTER KOBE BRYAN WAS FLYING, MILITARY APPLICATIONS? INTRO PIANO CO, MAKER OF QRS11GYROCHIP
https://www.bitchute.com/video/dViA5VxbadMz/
KOBE BRYANT THE TRUTH ABOUT HIS HELICOPTER, SIGNALING, MUSECAGE AND DARK MUSINGS
https://www.bitchute.com/video/WIuNXcP0yQy8/
Ties into many Events that are signaled prior. Why do you suppose that is?
CARTOON FROM LEGENDS OF CHAMBERLAIN HEIGHTS SHOWING KOLBE BRYANT IN CRASH OVER 3YRS PRIOR TO DEATH
https://www.bitchute.com/video/tJzmNUGDcVU6/
Bottom line is. ..if we are declared into a covert war then the sitting commander and chief, who is legally still President Trump, will remain in power and continue in the middle of a crisis.. As verified by the Director of National Intelligence (DNI) John Ratcliffe.
There would not be a hand off as this is all about espionage in our election process and cybertage. Subterfuge using information warfare in the cyber vector.
There are also reports of counterfeit money and weapons that were brought into battleground states.
**UPDATE from Patriot James King as seen on this group the Inconvenient Truth!
CNN Originally reported the interests those at the top of the business interests chain in Venezuela had in Smartmatic along with the manipulation to give Chavez a victory. A Harvard Mathematician crunched the numbers and stated it had to be the machines. Runs through their history. Majority of the workers for Smartmatic are based in Venezuela verified and testified.
https://www.facebook.com/IKFSSAPresident/videos/10219566897867271
Sources,
https://cyber.dhs.gov/ed/21-01/
Allied Security Operations Group forensics report pdf
https://www.9and10news.com/content/uploads/2020/12/Antrim_Michigan_Forensics_Report_121320_v2_REDACTED.pdf
https://www.statesman.com/article/20120901/NEWS/309008985
https://finance.yahoo.com/news/solarwinds-corp-swi-president-ceo-181502379.html
https://www.theguardian.com/technology/2020/dec/16/solarwinds-orion-hack-scrutiny-technology
https://www.history.com/topics/inventions/guglielmo-marconi
https://www.solarwinds.com/securityadvisory
https://www.cnbc.com/2020/12/15/joe-biden-selects-pete-buttigieg-as-transportation-secretary.html
https://github.com/fireeye/sunburst_countermeasures
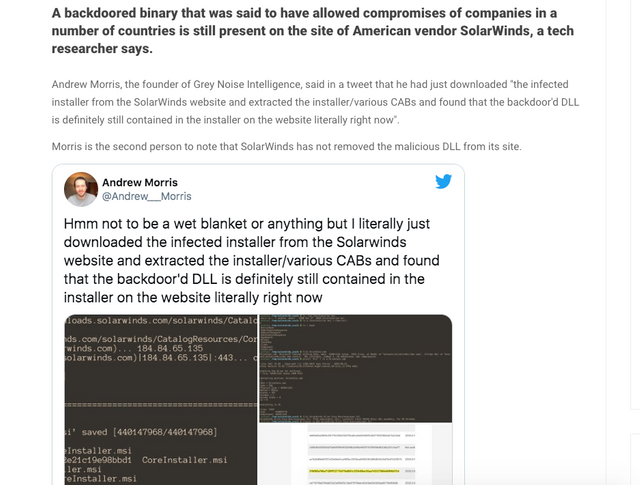
https://www.itwire.com/security/backdoored-orion-binary-still-available-on-solarwinds-website.html
https://www.investmentwatchblog.com/dominion-uses-solarwinds-guess-what-just-happened/
https://www.9and10news.com/2020/12/14/analysis-of-antrim-county-ballot-machines-made-public/
https://www.9and10news.com/content/uploads/2020/12/Bill_Bailey_Antrim_County_Press_Release.pdf
See connecting articles here recently written,
UPDATE article
2022
#UkraineCrisis, #StarlinkSatellitesShotDownInUkraine WHY?
https://steemit.com/emergencybroadcastsystem/@artistiquejewels/the-emergency-broadcast-system-ebs-was-initiated-during-the-kennedy-administration-to-allow-the-president-to-address-the-entire
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit