When we created Steemit we set out to create a system that was as easy to use for normal individuals as possible. Just a few weeks ago there were posts complaining about password length being too long. Back then we only required a 16 character password.
Since then a white-hat hacker has brute forced hundreds of passwords. Brute forcing is possible when people pick simple and predictable passwords. I wouldn’t be surprised if the same people complaining about passwords being too long are the ones who were brute forced.
A recent article by @arhag states that If you can remember your Steemit password, then it probably isn’t secure. We would like to extend his thoughts and say, “if you can easily type your password then it probably isn’t secure”.
On our beta platform we ended up compromising security for ease of use. It is clear that we erred too far on the side of ease of use.
Steemit will Generate Passwords
Going forward users will not be given the option to pick their own passwords. Instead, a random password will be generated in the user’s browser. Users will be asked to backup the password in a password manager, write it down, take a picture or print it out. All of these things are more secure than using a weak password.
Services such as LassPass… specialize in keeping your passwords secure and available on all of your devices. By generating passwords we will make adopting a password manager the easiest option.
Reasons for Insane Password Strength
Unlike almost every other service on the internet, Steem maintains a public database: the blockchain. This means that Steem is operating in the same state that Google, Apple, Microsoft, Yahoo, and your Bank do AFTER THEY ARE COMPROMISED. Once Google user accounts are compromised they require everyone to change their passwords because it is only a matter of time before the passwords are brute forced.
Steem requires users to have passwords that cannot be brute forced.
By having long and completely random passwords, everyone can rest assured that no one will successfully brute force their password.
Updates to Website Key Management
The Steem blockchain has a very advanced and complex permission scheme. This enables it to be incredibly secure and compartmentalized. This security comes at the price of complexity. The feedback we have received is that most users do not understand the difference between owner, active, and posting authorities.
Going forward the standard user experience will be to have one password from which all other authorities can be derived. Any time you change your password, we will update all of your authorities to use a password derived from your master password.
Key Management
When you login Steem will only cache your posting key, all other keys derived from your master password will be immediately discarded. Every time you navigate from one page to another on Steemit we will check for active and owner keys and remove them from memory. This check is done out of an abundance of caution.
When you want to make a transfer or change your password, then you will be prompted for your password so that the website can derive your active or owner key. The password and keys are discarded as soon as they are used to sign the desired transaction.
The result of these changes to our key management is to make your active and owner private keys unavailable to script injection attacks.
Power Users
Power Users will be able to login with their posting and/or active private keys directly. If you know how to do this then we will presume you know how to keep things secure. Steem is an open platform, power users will have access to tools for more powerful key management. Steemit is our interface that we are targeting at the masses.
Why we don’t store Passwords on the Server
Many people have asked us to keep user keys on the server and encrypt them with a more traditional password. Under this model our users would be in the same position as Google or Yahoo users. A compromise of our database would result in their accounts being vulnerable to brute force attacks.
At some point in the future we may consider such an option, but for the time being we prefer to leave password/key security and storage to the experts (LastPass) who can certainly do it better than we could for the time being.
Why we don’t offer N-factor authentication
Our password recovery process is a form of N-factor authentication that only takes effect after you have had your keys compromised. Normally we do not have to be involved with your transactions.
It has been repeatedly stated that we should offer multi-factor authentication for transactions. This would require our servers to co-sign every transaction. This is inconvenient for normal use and usually considered overkill for a social media platform.
Once we add time-delayed transfers and notification, then the account recovery process will essentially give “after-the-fact” 2-factor authentication on almost all transfers.
Look for Updates
Over the next couple of days we will be rolling out updates that will guide all users to migrate to more secure, randomly generated, passwords. Account recovery, password change, and new user signup will all require the use of these randomly generated passwords.
Summary
We have learned a lot from having our site hacked and are taking strong measures ensure everyone’s account is as secure as possible.
First, I am very happy to hear about the new policy to generate random passwords for the user and disallow user-selected passwords.
But I think there is much more to be done to improve security.
I have a full response to this post written out here.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for the update. Your work is highly appreciated.
But I think we should reconsider the 2-factor authentication.
I do agree, generally speaking, n-factor authentication is an overkill for social media.
But Steemit is not our regular social media. It contains lots money in it. Some users may have more money invested in Steemit than their banking accounts or online brokerage accounts.
So probably should we consider 2-factor authentication if a login tries to initiate a transfer or withdraw over certain amount of money?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
2-factor authentication is a great idea!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Here is a low tech way to choose a good password from Steve Gibson. He also has a random password generator.
https://www.grc.com/ppp.htm
https://www.grc.com/passwords.htm
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I never had a problem with passwords. I use long passwords by default. The issue here is most people aren't like me so we need a simple way to generate passwords. So now you're putting the responsibility into the hands of Steemit and how will we know their random number generator is truly random?
I understand this is a difficult problem but I would like to request an expert mode to bypass this for people who know what they are doing. I would also like to know more about the random number generator Steemit will be using and the sources of entropy. If they use a pseudo random number generator then that might not be good enough, but if they get entropy from random keystrokes and mouse movements that might be slightly better and I'm guessing that is how they will do it.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I just use a bitcoin private key that holds no balance... copy and paste to log in
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Interesting. Does the Trezor password manager do something similar to that?
I currently do a few one-way hashes.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Trezor password manager is cool but it's not perfect. I've seen better options which Steemit could implement such as Clef. I suggest the Steemit development team implement support for Clef along with these improvements. SQRL is also a good alternative. The ideal is to move away from passwords once and for all and instead move onto "something they have" vs "something they know".
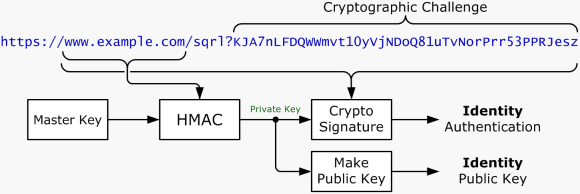
References
https://getclef.com/
https://getclef.com/security/
https://getclef.com/developer/
https://www.grc.com/sqrl/sqrl.htm
https://docs.getclef.com/docs/integration-guidelines
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
That looks like it requires a mobile phone to sign in to a desktop app. How do you sign in to a mobile app?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Why is this buried? If it weren't for a bitcointalk link I wouldn't have seen it.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
good stuff from the devs
hacked site in the early times is the best lesson for the future times
thanks guys
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for the info and elaborations. Really much appreciated.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
The upside of this is that brute-force hacking will be much harder.
The downside is that many people are going to start writing their too-complicated-to-remember passwords down, and that will lead to its own problems.
But it sounds like this is a don't let perfect be the enemy of good solutions.
That said, given the choice, I'd rather have a remember-able password and have to 2 factor auth using google authenticator every time I log in. Perhaps at some point in the future you can let user choose which they'd prefer?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Writing it down is the least of the problems. The problem is now going to be keyloggers and obvious backdoors. How will they type in a password without hackers capturing it? SQRL and other methods can bypass that but then their smart phones would have to be secure and they probably aren't always secure.
In the end we have to access that people are going to be hacked no matter what and have good disaster recovery procedures.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
What random number generation process will this generated password be using? I'd rather generate my own passwords as an expert. If there is any flaw in the random number generation process then all passwords generated from that process could be compromised.
So how will this work? Where would the sources of entropy come from? Where is the source code for generating the random numbers to do this password generation?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
https://steemit.com/steemit/@steemitblog/how-steemit-generates-secure-random-passwords
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Solid work by the developers who have now handed the hacker back his white hat and raised the bar infinitely. People underestimate how easily a password can be hacked and I'm guessing 50 (maybe less since there are many with high crypto it's) percent or more people probably use the same password for multiple accounts, so once a hacker has your password or email password they can wreak havoc on you. Thanks for keeping our hard work safe!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This great news. Helping to understand the value of strong passwords is important especially like someone mentioned the amounts money people could potentially have in their accounts. Use this invitation link to LastPass and get a free a month of premium service. https://lastpass.com/f?4635516 . Only the first 24 people will be able to use this. If you do sign-up get your referral link and pass it on to new users. Password management tools like this are must for all users .
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
hello Dear, kony he lost his password yeaterday because he made some emails from suppor@steemconnect. when I chacked it, I saw Update. So, he can't be able to long in now. please, guide me about that.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
After reading this post I turned to google and found this site : https://www.grc.com/passwords.htm
It generates high quality random passwords of 64 characters.
here you can check the power of your password against brute force :https://www.grc.com/haystack.htm
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Right so why not just use SQRL and get rid of the password for people who don't want to care about passwords anymore?
Access control is by either something they have, or something they know, or something they are, or any combination of that. So you don't really need a password for authentication or access control but you do need their smart phone, or biometric, or something else. If a password must be used then pick a high entropy password. But I think another issue is most people's computers can be compromised so a keylogger would capture them entering in their password anyway.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
The best way I have found for making a strong password is by using a mneumonic or a series of rhyming couplets. It's the length of the password that provides protection against brute force not complexity.
This is a really good site to give you an idea of how fast numeric passwords can be brute forced with no prior knowledge:
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
great update, i really appreciate your post but in my opinion the 2-factor authentication or sms verification by phone will be better than just a password , hackers will try always and they never give up, that is just my opinion i'm not a pro i'm jus an other guy
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
thank you devs, now with your efforts we have a much more safer platform
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for the explanations, this is the first post I've read and up-voted since joining!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
It's some old thread I guess, but has something changed since then? Let's say person who has significant money on steem account got lastpass hacked. After logging I can see priv keys, so I guess all money can be transferred without any issue.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
What about requiring a password with a minimum of x or xx characters? These random-generated ones are hard to use.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
A strong password does not prevent account hacking.
The hacker can put a keylogger in your computer and very easily collect all the password you type.
I remind you that the keylogging if a feature of Windows 10. Everything you type in this system is reported to Microsoft.
Every browser ask you to store your password. This kind of storage is very unsecured. You can very easily recover your password stored in this way.
I think that 2 factor authentication is a must when it comes to protect your fund. You should use either U2F (FIDO) or TOTP authentication.
U2F authentication requires you to push the button of your usb authentication key that's It. It's quick and simple.
A U2F key costs less than 10 $.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit