In antiquity before the creation of the OSI, performing a communication on a computer network is not easy because each vendor and developer in that period using their respective network protocols, making it difficult for users when going to exchange data from a computer to another computer due to protocol networks owned by each computer is different.

source
Seeing this, in the 1980s the international standardization body of the International Organization for Standardization (ISO) created a reference model called OSI consisting of seven layers. Each layer has its own role so at this moment we do not have to worry about what computer protocol problem you will use to be able to communicate with your friends. For more details about the OSI layer or the OSI model, its seven layers and how it works, see the following description.
Understanding OSI Layer (OSI Model)
Open System Interconnection or OSI is commonly referred to as a reference model in the form of a conceptual framework that defines a connection standard for a computer. The purpose of making this OSI reference model is to be a reference for vendors and developers so that the products or software they create can be interpor, which means it can work together with other systems or products without having to make special efforts from the user.
OSI Model – Stacked Application Layers
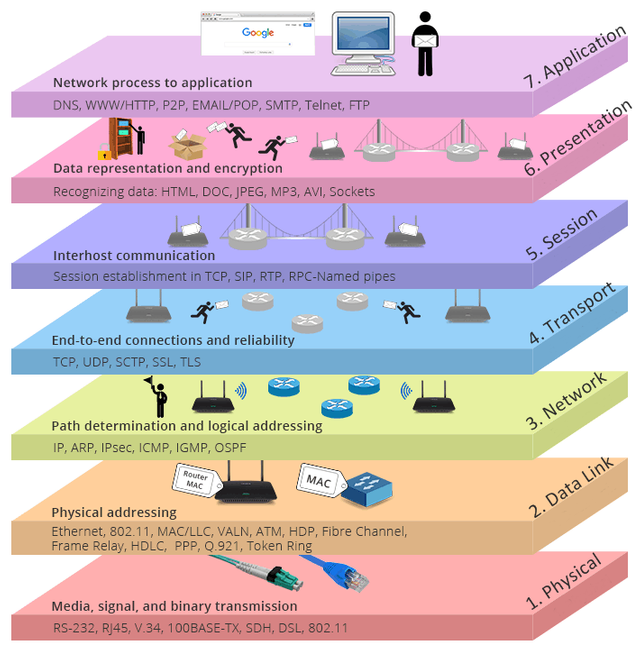
source
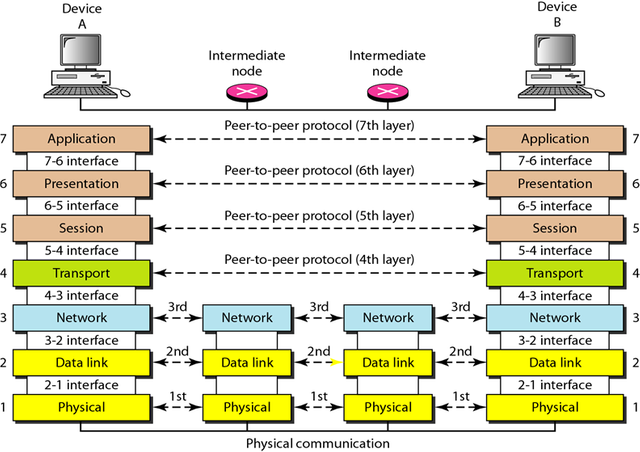
In the process the OSI model is divided into seven layers in which each layer has an interrelated role between the above layer and the layer below it. Here is an explanation of the seven OSI layers.
Layer 7 – Application Layer
The application layer is the topmost layer in OSI network model. There are plenty of applications available which facilitate different types of communication over a network. Typical examples of this layer are web browsers, email clients, remote file access, etc. A user usually interacts with these applications and access communication over a network.
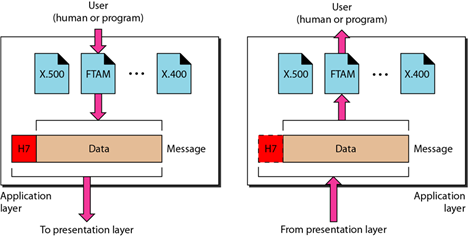
source
Do not get confused with these applications or programs as part of OSI model. The application layer provides necessary protocols or network services, such as FTP, HTTP, SMTP, IMAP, etc., to all these programs. For example, one can configure an email client on your smartphone by configuring IMAP or POP settings, which are nothing but Application layer protocols.
Another example of this layer is when you try to browse the internet, HTTP is the application layer protocol which in turn, identifies the communication partners, establish resources & orchestrate communication. This layer either provides or receives data from the sixth layer aka presentation layer.
6. Presentation Layer
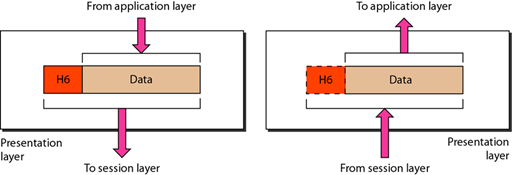
source
The presentation layer is responsible for defining the syntax that the network host uses to communicate. The presentation layer also performs the encryption / decryption process of information or data so that it can be used in the application layer.
5. Session Layer
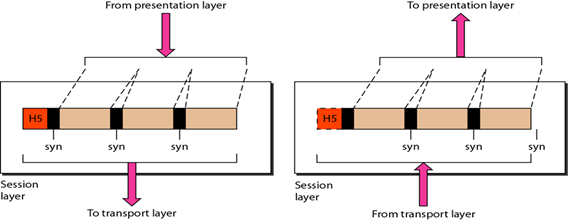
source
Session layers are responsible for controlling connection session dialogs such as setting, managing and disconnecting between computers. In order to establish a communication session, the session layer uses a virtual circuit created by the transport layer.
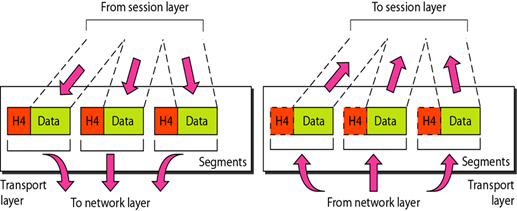
4. Transport Layer
source
The transport layer is responsible for sending messages between two or more hosts within the network. The transport layer also handles the splitting and merging of messages and also controls the reliability of the given connection path. The TCP protocol is the most commonly used instance of transport layer.
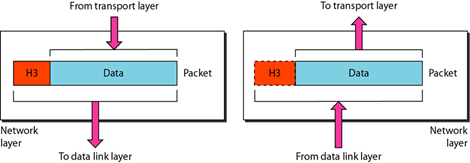
3. Network Layer
source
The network layer is responsible for defining the path to be used to transfer data between devices within a network. The network router operates on this screen, which is also the main function of the network layer in terms of routing.
Routing allows packets to be moved between computers connected to each other. To support this routing process, the network layer stores logical addresses such as IP addresses for each device on the network. Layer Network also manages the mapping between logical addresses and physical addresses. In IP network, this mapping is done through Address Resolution Protocol (ARP).
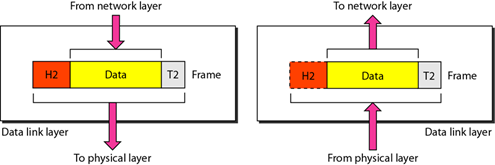
2. Data Link Layer
source
The data link layer is responsible for checking for errors that may occur during the data transmission process and also wrapping the bits into the data frame form. Data link layers also manage physical addressing schemes such as MAC addresses on a network. The data link layer is one of the fairly complex OSI layers, so it is subdivided into two sublayers, namely the Media Access Control (MAC) layer and the Logical Link Control (LLC) Layer.
The Media Access Control layer (MAC) is responsible for controlling how a device on a network gets access to the medium and permits to transmit data. The Logical Link Control (LLC) layer is responsible for identifying and wrapping network layer protocols and controls error checking and also synchronizes on the frame.
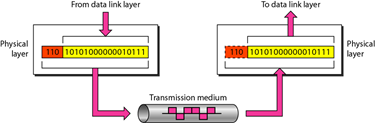
1. Physical Layer
source
Physical layer is the first or lowest layer of the OSI model. This layer is responsible for transmitting digital data bits from the physical layer of the sending device (source) to the physical layer of the receiving device (destination) through the network communication medium.
In physical layer data is transmitted using a type of signal that is supported by physical media, such as voltage, cable, radio frequency or infrared or light.
How an OSI Layer Works
The process of running data from one host to another on a network is fairly long, all the data must go through each layer of the OSI to get to the destination host. Example for example when you will send an email to another computer on a computer network.
The process that occurs first is on the application layer, which provides an email application program that will be used to send data to other computers through the network. The presentation layer of the email is then converted to a network format. Then on the session layer will be formed a session of travel data from start to be formed until the completion of the delivery process.
how the OSI layer works
source
In the transport layer the data is broken down into small parts and then will be collected again at the transport layer of the receiver. In the network layer will be created an address and determined the path that will be passed by the data to get to the destination. In the data link layer data is formed into a frame and physical address of the sending and receiving devices will be set.
Then at the last layer the physical layer sends the data through a network medium, leading to the transport layer of the receiver. Then the same path occurs in the destination computer but starts from the bottom layer (physical layer) to the top of the screen (application layer).
source
Hope this article is useful to understand the OSI model and how it works. Understanding how the OSI screen works can improve our understanding of how a computer network works and the protocols involved there.
References for further reading:
- https://community.fs.com/blog/tcpip-vs-osi-whats-the-difference-between-the-two-models.html
- https://cohesive.net/2017/06/cloud-security-best-practices-part-4-application-security.html
- https://www.stemjar.com/osi-model-seven-layers-explained/
- https://www.ictshore.com/discover/osi-model-introduction/
- https://technicalustad.com/the-osi-models-seven-layers-defined-and-functions-explained/
- http://semiengineering.com/osis-model-for-security/
Support @steemstem and the #steemstem
project - curating and supporting quality STEM
related content on Steemit

This post has received a 1.54% upvote from thanks to: @biomanu.
thanks to: @biomanu.
For more information, click here!!!!
Send minimum 0.050 SBD/STEEM to bid for votes.
Do you know, you can also earn daily passive income simply by delegating your Steem Power to @minnowhelper by clicking following links: 10SP, 100SP, 500SP, 1000SP or Another amount
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit