Hello Steemstemers, Utopians, Future Hackers and Crackers :]
%20(1).jpg)
Methodology: The Hacking Process
Any type of legitimate hack, be it of virtue or spite, has a process in which it should be conducted. Today, I would like to take these few moments of your time, one so as to show you the methods that practices that attackers will take, to invade your devices, lives, etc. Perhaps more importantly, if you are following along with these guides for more than just informational reading, and rather personal use, this is where you will learn the steps that you as a hacker, be it ethical or not, should always take, at least into consideration. I have created the image below to illustrate the process clearly.
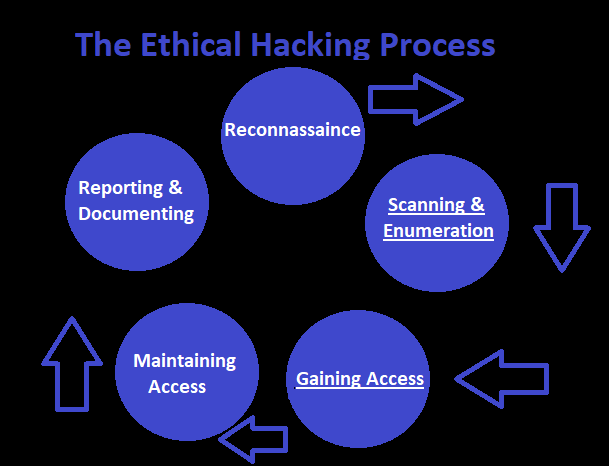
Self-Generated Image
Reconnaissance:
Reconnaissance is a critical step in any hack, and well, really any spy mission ever lol. Reconnaissance is the step where you do nothing but learn. learn every single thing about your target that you can. Emails, birthdays, favorite color, It will all be useful. More commonly, this step refers to performing manual or passive means of recon, on a target server or device, however I personally feel that ANY information, is useful information.
Nmap, Nessus, and Maltego, are all different tools that can be used for reconnaissance of a device, however Nmap, standing for Network Mapper, would be one of the first things an attacker will use, to gather information about a device, and the processes/protocols that it may be running. We will learn more about Nmap below in the tools section. For know, lets carry on to the next step, knowing that one should only do this once they feel they have amassed enough information on a target that they feel comfortable launching an attack.
(Remember, the reason we spend so much time learning about our target, is because any errs in our tactics, will almost certainly alert any legitimate service to the threat, thus defeating yourself before you have even started.)
Scanning, and Enumeration:
Scanning and Enumeration, is the step in which we take the time to learn even more about our targets :) This time however, we are going to be actively scanning our targets for any potential vulnerabilities, or means of access. The tools commonly used in this step, are Nmap again, Nessus, and Nexpose. One of the first things an attacker will do, is scan open ports on a device, to see if perhaps they are running an outdated SSH or Telnet Server, which would be a fairly common means of gaining access to an average household device or web server.
Tools like Nessus however, would be used to scan a web server for any potential means of access, like perhaps some sort of remote code execution, or file upload vulnerabilities. Many of these are outdated techniques, that still function perfectly well for the average situation, however often times you will find a rather dangerous vuln in the wild.
Gaining Access:
Gaining Access is of course a crucial step in the hack, and again obviously one of the most exhilarating and fun steps as well. This is where all of your hard work in the first two steps has finally paid off. The tools used to gain access to a device or a server, will most often be a tool known as Metasploit, however there are variations like Arbitrage that are also useful.
Gaining access can be done through so many possible means, that I would never list them all here, though a few of the more common ways, are simple Trojan viruses, SSH/Telnet/VNC/RDP exploits, etc. There are so many things to defend in your computer, that I will probably be taking the time in the near future to do a piece on that for our more user friendly readers :)
Maintaining Access:
Maintaining Access, is the step you take immediately once you have gained access to the target system, and only once you have done everything that you needed to get done immediately. Once again, Metasploit will be used more commonly for this step. This is the time where you will find some sort of backdoor to set up on the target device, so that you can come back to it for further access.
Methods used as a 'backdoor' can be anything as simple as creating a new user, and opening an SSH tunnel to your PC, or as complicated as turning the target into a slave for your zombie army. (Bad Black Hat!) Once you have gained access to a target, maintaining is usually fairly simple, at least in some way.

Reporting & Documentation:
Well guys, this step isn't included in every attack, as not all people are ethical. But this is an ethical guide, and I believe that as users of the internet, we should all be working towards a safer community for everyone, and one of the main aspects of that, is disclosing potential dangerous vulnerabilities, to people who have the power to fix it. Be that the owner of the device, the IT department, whoever can fix the problem, and will not abuse it.
This step should when possible be done quite professionally. you never want to indicate that you are a potential threat, or even are seeking reward, as this could come off as blackmail or extortion to some. An ethical hacker, will often do his/her best to outline the process in which the attack was completed. The tools used, Vulnerabilities Exploited, and potential threat model, should an attacker find the same information that you already have.
Interested in Payment?
I did mention to never ask for reward, though for those of us who like to eat and live in houses, money has to be made at least some of the time :) When you take your time, do a good job, and impress you person you have helped, often times, depending on who you have helped, they will reward you in various ways. There are numerous corporations who have already initiated public bug hunting bounties, and their terms and conditions are clearly defined so be sure to take a look at that.
You may even score a job out of the deal should you save something important enough. In the past, I have had people ask me to do regular testing once I have found a vuln, and I currently work for three businesses in my city doing pen-testing for them every 6 months or so. If you find this is something you are good at, you can make quite a decent bit of money on bigger websites like Google, or Facebook. I hope this has been entertaining for you, and next we will be doing a brief little outline on the tools mentioned in this post.
Tools of Mention
Nmap: Network Mapper
Nmap is a fairly simple to use tool. however it is quite extensive an powerful at the same time. Nmap operates by using raw ip packets, in many many different ways, sometimes even fragmented, so as to determine information about a device on a network, or even a network as a whole. Nmap is used commonly during the Reconnaissance, as well as the Scanning and Enumeration phase, and will give information such as what ports are currently open, what services a target may be running, even sometimes make and model of PC or OS.
Nessus: Web Vulnerability Scanner
Nessus is an extremely powerful tool, free of charge for personal use, and used all over the world by attackers looking to gain acces to systems. This tool is largely used during the Scanning & Enumeration Process, and will do everything it can to find all vulnerabilities of a web server. This tool often finds sever dozen at the least, however many of them are often low threat vulnerabilities.
Maltego: Data Mining and Footprinting
Maltego is a tool used for gathering a different type of information. not necessarily open services or ports, but rather domain names, foot-printing, and more of this personal nature. This is a way of finding more of an external exploit, though perhaps a neighboring domain that lives on the same web server as your target. This too is a powerful and extensive tool.
Metasploit: Attack Framework - Hacker Heaven
Metasploit... What to say about Metasploit. Metasploit is an extremely advanced attack framework, one which I love so much that I'd like to mention, this tool was created by H. D. Moore. It is designed with security in mind, for all sorts of penetration testing. There are thousands of different exploits available to your hands with this tool, for a wide variety of devices, from Mac to Android.
Conclusion
I hope this has been an informative, and entertaining read for you all, and I am excited to see you again in the near future. I am greatly enjoying doing these guides, and as always am interested in hearing your oppinions, feedbacks, etc. I'd like to be showing you how these tools are used in the near future, however before we get down to any of that, we will need to ensure that we are doing our practices from a secure device. One free from prying eyes that is...
In the next guide, we will be setting our Kali Virtual Machine up, so that all network traffic within it, will be configured through a 'tor' exit node. It is critical to never to any of the things mentioned in this guide, from your home PC, or a device directly connected to you. Even if you aim to please, the world may not see it so. I wish you all the best.
Happy Hunting,
Cerulean
Interesting content overall, I'll drop a follow. Also voting for some videos!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Haha awesome :) Always happy to meet new peeps. Hope I can keep em comin for ya!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
So glad to see everyone enjoyed this! There is lots of fun stuff to come, and I can't wait to get through it with you :]
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi ceruleanblue,
Visit curiesteem.com or join the Curie Discord community to learn more.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You made my day! Thank you Curie! So happy to be a part of this awesome & friendly community.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @ceruleanblue!
Your post was mentioned in the Steemit Hit Parade for newcomers in the following categories:
I also upvoted your post to increase its reward
If you like my work to promote newcomers and give them more visibility on Steemit, consider to vote for my witness!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Love the new avatar pic @arcange
!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Cool themed posts man, I like it. Always wanted to know this stuff, even if I never used it. Following now to see what else ya got.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks a bunch man, It's nice to see that people find it even just an interesting read :) Happy to make another buddy, and will definitely be checking your page out as well. Have a good one!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks alot. With some Dtube videos the content can be more informative on practice.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Awesome idea @fako! I have been wanting to do Dtube specials with these as well. Will definitely take the time in the near future :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
@ceruleanblue I gave you an upvote on your post! Please give me a follow and I will give you a follow in return and possible future votes
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I'd be happy to follow you, and thank you for enjoying my post, though I would advise you to only vote on content that you enjoy, rather than so as to earn followers and future votes. It will work out better for you in practice, as you only have a limited amount of voting power, especially as new as we are.
Will always upvote your post if it is enjoyable for me :) Good luck in the future,
Cerulean
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
the comment above is most likely spam mate :) I think its steemstats.com where you can see everyones comments, previous comment I mean, comes in handy to fish out the spam accounts :)
edit.. its blatently a copy and paste comment
Congrats on this epic post , I resteemed it for you and will read it later myself as someone who knows nothing of this subjuect !
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hahaha Thanks buddy
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Dude!! Just read it all now ☺ im exited to see about setting up to run all through tor, thats sounding fucking great! Im a perfect tester to follow your instructions as I will try it on my laptop and if i manage to do it from that future post,then anyone can hahaha
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Haha awesome :) I can definitely help you out if you get stuck anywhere. Nothing better than a Tor-box. Not reliable for anything large, but good enough anonymity for the average misuse :P
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Sounds like it eliminates the need for a vpn?!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit