As a growing network engineer, I was fascinated with the workings of the Internet and IP operations. When I was introduced to network simulation tools like Cisco’s Packet tracer and GNS3, I made very complex networks of switches and routers and that gave me unspeakable joy. Within weeks I was almost an expert with Cisco command line interface (CLI). Of course, I had my feel of networking hands-on cause I was opportuned to be part of the field engineers in my former office.

[Image source: Pixabay. CC0 Creative Commons License.]
As it were with every aspect of human life, my networking career became boring with time and as such, I wanted more. I was highly certified so getting an interview was always easy for me. I was being interviewed one day and my interviewer being very impressed with my skills asked if he could get some network security personnel from my former unit, that they were ready to pay a premium to have such person. I lost interest in the position I was seeking (WAN support Engineer) not because of the monetary involvement in the statement my interviewer just made but because I always believe that as a salary earner, your salary says a lot about your importance.
I carried out a research on career path in networking and came up with two conclusions. First, setting up a network is easy and secondly, securing a network is equally as important as monitoring a network and both are more important than the former.
This post is all about network management and when it comes to network management, two main protocols power any network management solution. These protocols are the Internet Control Message Protocol (ICMP) and Simple Network Management Protocol (SNMP).
The ICMP
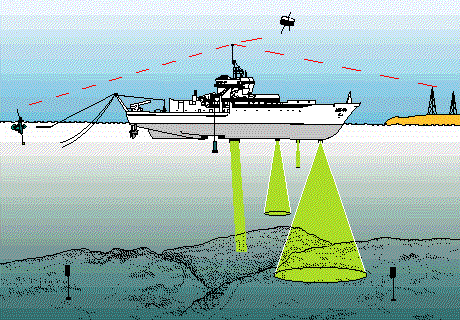)
Sonar technology is widely employed in marine systems for locating marine objects, positioning, etc. Image credit Wikimedia. Image by Sonerkut. Creative Commons Attribution-Share Alike 4.0 International license.
During my high school days, there was a topic in Physics I liked very much and that topic was acoustics (Sound). A very popular sub topic on Sound Physics is the Echo and one very important application of echo is in the determination of depth or distance. A special device (sonar) was developed based on the principle of echo and is used in the determination and location of marine objects. The ICMP works on principle similar to that of sonar.
The Internet Control Message Protocol just as the name suggests, is a protocol that contains the control messages of a network. Control messages are light weight packets since such packets are void of application data, they only contain information about the network health and or status. A very popular ICMP utility is the Packet Internet Gropper, popularly known as PING.
ICMP uses 14 sets of messages and depending on the designation of the message it receives, ascertain the status of a network. Hence, ICMP is mainly used to manage and troubleshoot “network” related problems. The “network” in the statement above is in quote because ICMP only exists in the layer three (network layer) of the International Standard Organization’s (ISO) Open System Interconnect (OSI) protocol stack and can hence only detect issues related to network connectivity.
Putting the above statement in simple and clear terms, a successful ping operation does not equal a successful web browser operation. This is because the web browser uses protocols which are higher up the protocol stack than the ICMP, which means that in absence of security commands explicitly blocking an ICMP operation, a successful browser operation equals a successful ping operation.
The sets of messages used by the ICMP are listed below alongside its numeric designation or message type
| S/N | Message Type | Description |
|---|---|---|
| 1 | 0 | Ping reply |
| 2 | 3 | Destination Unreachable |
| 3 | 4 | Source Quench |
| 4 | 5 | Redirect |
| 5 | 8 | Ping Request |
| 6 | 9 | Router Advertisement |
| 7 | 10 | Router Solicitation |
| 8 | 11 | Time Exceeded |
| 9 | 12 | Parameter Problem |
| 10 | 13 | Timestamp Request |
| 11 | 14 | Timestamp Reply |
| 12 | 17 | Address Mask Request |
| 13 | 18 | Address Mask Reply |
The message type 0 works in line with message type 8 and in fact, many networking authors treated the two as one. The type 8 and type 0 messages are used for communication between two remote hosts in a network. Here, a probing host transmits an echo request message (also known as ping request) to a remote host determined by an IP address provided by a user. If the probing host successfully receives an echo reply, the network under test can be assumed to be free from connectivity issues.
Consider the ping commands from my PC, the first ping command was targeted at www.google.com which was resolved with the help of my functional DNS server to the IP address shown in the image.
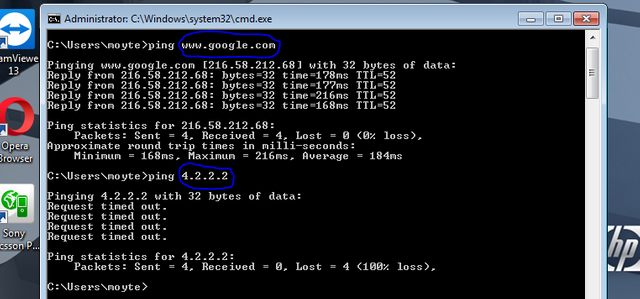
From the summary of the command by Windows, it can be seen that my computer sent four (4) packets of echo request messages with a size of 32bytes (this the default size of echo requests and can be changed), just like the normal physical echo, the packet successfully traveled to Google.com and returned a response after 178 milliseconds, 177 milliseconds, 216 milliseconds and 168 milliseconds respectively, meaning that I have functional Internet connectivity.
The above timing depends on the instantaneous speed of my network and hence varies.The TTL (time to leave) is a parameter that is used to prevent packets from traveling infinitely in a network (loop), hence, the TTL value is 255 by default and is decremented any time a router receives a packet. Once the TTL value clocks 0, the packet is dropped and error message like "destination unreachable" can be sent to the originator of the packet.
The ICMP message type 3 (Destination Unreachable) is not used in conjuction with other message types and is used to inform a probing host about the unreachability condition. There are basically four unreachable conditions numbered zero (0) to three (3). Condition 0 is used to inform a probing host that a network is unreachable. Condition 1 is used to inform a probing host that the remote host it is probing is unreachable.
At this point, I need to differentiate between a network and a host. A network is the "folder" that contains the host. Withing a network, we can have many hosts. Take for instance, the network address 192.168.1.0/24. This is a network address that can contain up to 254 hosts in the range 192.168.1.1 to 192.168.1.254, where 192.168.1.0 is the network address, 192.168.1.255 is the broadcast address used to address all the hosts in a network.
Condition 2 is Protocol Unreachable and is used to report a reachability problem relating to transport layer of the OSI model i.e, TCP or UDP. Finally, condition 3 is the Port Unreachable, someone might ask, what then is the difference between transport layer issues and port issues? To expand on the condition 3, this condition report issues relating to active or inactive process on a target host. This is more like saying, "there's no network reachability issues, no network protocol stack issues but the application on a host I am trying to use has either not started or is not located on the remote host".
From the image above, the second ping command returned with a message For more explanation on the lists above, please refer to the reference section.
The Simple Network Management Protocol (SNMP)
As described above, ICMP is a great tool for any network administrator and even an ordinary network user in that it helps in confirming the condition of connectivity, reporting problems in the network using clear messages (a possible vulnerability) but ICMP does not offer concise information about the problem it detected. For instance, a "network" unreachable message does not say exactly where the fault originated, but with that, we now know that we have a "network reachability problem". This is where the SNMP comes into play.
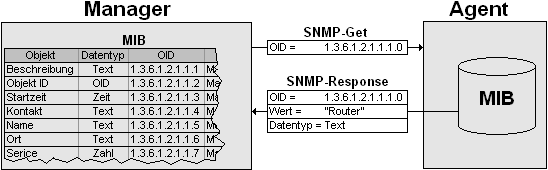
Overview of the operation of SNMP, data flow between the agent and the manager. Image source Wikimedia. A Creative Commons Attribution-Share Alike 3.0 Unported license.
The simple network management protocol has been around for long and can be said to be as old as the Internet itself. SNMP is so common that almost all managed device is made SNMP compliant, which means such device can "speak" and "understand" the language of SNMP. The "language" of SNMP consists of a central location (Network Management Station) which requests/probes for "certain" information from a device depending on the capabilities of such device with the help of an agent and also serves as a storage location for information sent by a compliant host.
SNMP just like the ICMP is a standardized protocol and works independent of any environment. Devices that can be made SNMP compliant include phones, servers, routers, IoT systems, AI systems, switches, PCs, to mention but a few. Every SNMP enabled device contains what is known as the Management Information Base (MIB), this is the landing point of an SNMP agent from the NMS, more on this shortly.
Evolution of SNMP
Image source: Wikimedia. A Creative Commons Attribution-Share Alike 3.0 Unported license.
The Simple Network Management Protocol was introduced in the year 1988 with the sole purpose of reducing the management overhead of the internet. From the initial definition of SNMP in the RFC 1065 and 1066, SNMP consists of two major components, the agent and the manager. The manager as the name implies give out instructions in the form of applications, these instructions are responded to by the agents. The agents can also send information without receiving instructions from the manager in the case of notification to mark the beginning or the end of an event(s).
As expected, the first standard version of SNMP was introduced early 1990 and named SNMPv1. Due to the accompanying overhead on the payload of internet packets by the SNMP agents, a Data Definition Language (DDL) was introduced alongside the SNMPv1 to define many pieces of information contained in the agent database, the management information base (MIB). This DDL is known as SMI (Structure of Management Information).
The SNMP version 1 is has the advantage of simplicity, hence could easily be setup. It's setup only requires a community string which links the agent and the manager. This community string is exchanged in plain text within the network, making the version 1 an unsecured protocol.
The move to advance the version one was not an easy one and this is evident in the naming of the preceding version, the version 2c (there was never a version 2). The major drawback of the version one is security and this is majorly because it supported only 32-bit counter. With such counter, the version 1 can only hold approximately 4.3 billion bytes (232), converting this bytes into bits (232 * 8) gives approximately 34.4 megabits. Assuming management information was polled for say 10 seconds, we will have approximately 57.3 Mbit/s for a period of 10 minutes. Such value can easily overflow (for, say, a gigabit port) and when such happens, the counter starts counting from zero again.
Wrapping through zero once actually is not a problem since counters take progressive stance, hence when the counter generates a value less than the previous one, we can easily conclude that the counter has overflowed but the problem occurs when the counter counts through zero more than once for a process, making it impossible to determine how many times the counter has looped.
The main aim for the developing SNMPv2 (SNMPv2c) which is security was not achieved with the V2c which led to the move to the development of the version 3 around late 1997. With the introduction of version 3, strong security was not only added to SNMP but also added the remote administration functionality, making the version 3 a widely recognized industry standard and a success.
Components of SNMP
A simple network management protocol enabled network consist of three major components, these are:
- Network Management System
- Managed Device(s) and
- Agent
The Network Management System also known as the NMS is the intelligent part of the whole setup this is because the applications needed to control and monitor connected devices are located in the NMS. NMS applications can be deployed directly (dedicated) withing the network of devices it controls or it can be accessed as a service (SaaS). Dedicated NMS software has the advantage of being able to perform specific tasks and high level of flexibility and in some cases can be accessed remotely.
))
The three components of SNMP system. Image credit Wikimedia. Creative Commons Attribution-Share Alike 3.0 Unported license.
The managed device is actually the target device, i.e, the device that is being monitored and managed, just as the name suggests. It contains the SNMP agent. Managed device is a general name in the IT industry and is used to refer to devices that can be configured and possibly respond to SNMP packets.
The managed device has the functionality of storing information gathered by the agent and making such information accessible to the the Management System either based on request or submitted periodically or based on event.
An SNMP agent is a software or application within a managed device. An agent residing locally in a device has full knowledge of the format managment information exist in a system, the file format and heirarchy, and also have the functionality of ensuring that management information exits in standardized format(s).
The Management Information Base and the Object Identifiers
In order to facilitate understanding, I will take a buttom-up approach in explaining the concept of objects, object ID and management information base (MIB). An object is an virtualized version of a physical or logical component of a system. Take for instance, the LED indicator on the network port of a server, or the cooling fan in an IoT system, these can be refered to as an object of such system.
These objects can be grouped and assigned to an agent or sets of agents. The system software ensures that the agent has full information on the condition of the agent. The agent gathers these information and stores them in the MIB.
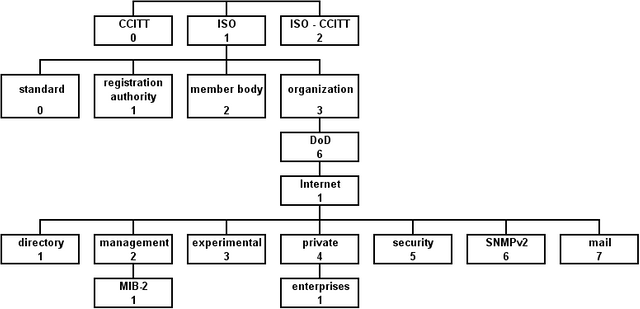
The heirachical structure of the management information base as assigned by different standard organizations
Wikimedia. Creative Commons Attribution-Share Alike 3.0 Unported license.
The MIB is heirachical a collection of information or messages and each object entry in the database has an unique Object ID (OID). The information contained in the MIB can only be accessed using standard SNMP. Information in the MIB exists in the form of module (containing instances of objects), hence each module can be referenced using the OID.
References
- Simple Netwrok Management Protocol ~Wikipedia
- Networking 101: Understanding (and Using) ICMP ~Enterprisenetworkingplanet
- ICMP Message Types ~InformIT
- Versions of the SNMP ~WebNMS
- Components of SNMP ~Oracle
- Management Information Base (MIB) ~Wikipedia

This post has been voted on by the SteemSTEM curation team and voting trail in collaboration with @utopian-io and @curie.
If you appreciate the work we are doing then consider voting all three projects for witness by selecting stem.witness, utopian-io and curie!
For additional information please join us on the SteemSTEM discord and to get to know the rest of the community!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi @henrychidiebere!
Your post was upvoted by utopian.io in cooperation with steemstem - supporting knowledge, innovation and technological advancement on the Steem Blockchain.
Contribute to Open Source with utopian.io
Learn how to contribute on our website and join the new open source economy.
Want to chat? Join the Utopian Community on Discord https://discord.gg/h52nFrV
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Can we talk on whatsapp?
+2348125706952
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
sure
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I love how simple it is to set up an SNMP for remote monitoring of equipment. It is one of my favourite past times in ages past :D
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Good to read https://9blz.com/smi-indicator-explained/
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit