Introduction
The address of the blockchain seems to be anonymous, but it is more transparent. Through the blockchain browser, people can find all kinds of transfer data of the address, whether it is the sender, the recipient or the amount, they can all see it. Once a person is associated with an address, privacy basically ceases to exist. Even seemingly anonymous accounts are transparent to some data analysis companies on the blockchain. Companies such as ChainAnalysis can discover the various connections behind the addresses through clues.
Therefore, since the emergence of cryptocurrency, privacy-related exploration has always existed, from privacy coins to privacy solutions are continuing to advance. Monero, Dash, etc. are all privacy coins. Monero uses an anonymous public key encryption scheme; Mimblewimble eliminates the concept of "address" and retains confidential transactions and interval proofs; Zcash's zero-knowledge proof supports general computing; and Ethereum-based The rapid development of Tornado, a currency mixing protocol, has also attracted the attention of the market.
In the development of encryption privacy, a trend has gradually evolved: the application scenarios of pure privacy coins are difficult to expand, and the demand for privacy layers has increased. Most of the privacy needs will not be solved by a separate privacy coin, but more likely to be solved by the privacy function on the chain. Suterusu is an encrypted privacy layer project developed in this trend.
Suterusu tries to be an encrypted privacy layer
The encryption privacy layer means that Suterusu is not a separate privacy token. It attempts to integrate with public chains and protocols to provide privacy functions for existing assets on different chains such as btc, eth, dot, atom, and realize users on different chains. Protection of privacy.
For example, Suterusu can realize the "anonymous transaction" of Bitcoin and Ethereum, can realize the "anonymous payment" of stable currency and even the national legal digital currency, which can be DEX such as Uniswap and Sushiswap, loan market such as Compound and Aave, YFI, etc. Converged mining projects provide privacy support. In addition, with the continuous development of blockchain, it can also support the needs of anonymous voting, anonymous auction and other scenarios.
Privacy DeFi
Judging from the current development of the encryption field, Suterusu's biggest scenario will occur in DeFi. With the rapid development of DeFi, users have an increasing demand for privacy. For example, some users don't want to see their transactions being tracked and analyzed by people, and they don't want to be found out which lending activities they have performed, which mining projects they have participated in, and so on. With the gradual maturity of payments, people also don't like their payments to be transparent. Ultimately, the DeFi field needs a DeFi with privacy. It can hide the sender, receiver and specific transaction amount. One of Suterusu's application scenarios is to help users achieve privacy DeFi.
In addition to privacy DeFi, with the development of web3.0, privacy is also an important prerequisite for the implementation of these applications in terms of privacy identification and data protection, and even data commercialization.
Privacy ID Proof
In the future web3.0 era, privacy identification will be an important basic function. When a user logs on to the website, it is not necessary to upload an identity certificate to prove the identity, and the user identity verification can be completed through the technology of private identity verification. This helps protect user privacy.
Data protection and commercialization of data
There are huge problems with current data protection and commercialization. On the one hand, data is abused, stolen by hackers, used by websites for various purposes, and users' privacy cannot be protected. And if the privacy of users can be protected, some data can be commercialized, such as very sensitive user medical data. When using ConSNARK's privacy technology, on the one hand, the privacy of users can be protected, and at the same time these data have the opportunity to be used for commercial purposes. These originally sensitive data can form a data transaction market, and data owners can obtain income without worrying about the leakage of their privacy.
From its official website, Suterusu has cooperated with Meter, Harmony, Chainlink, Elrond, Fantom, NEO, Theta, Waves/Gravity, etc. It also supports Heco and BSC chains, and currently supports anonymous transfers between ETH and BSC chains.
So, Suterusu, as an encryption privacy layer, how does it integrate with its public chain or protocol? How does it provide privacy services for users of these chains or protocols?
Suterusu's trilogy
Suterusu wants to provide privacy services for public chains and protocols. So, what is its place to settle down? Suterusu's core technology is ZK-ConSNARK. Compared with ZK-SNARK, it has some important features:
No trusted initialization required
Zcash requires trusted initialization, which leads to potential security vulnerabilities.
The amount of communication is almost constant
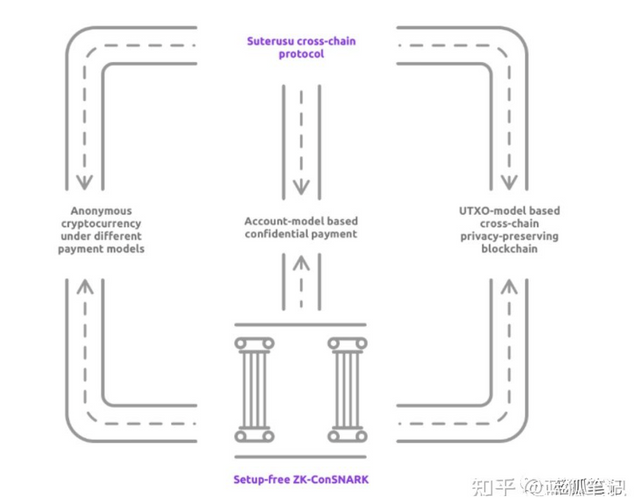
Through Suterusu's technology, the anonymity of the sender and receiver and the confidentiality of the sent amount can be realized. On the basis of ZK-ConSNARK, Suterusu launched Suter Shield for privacy mining; started SuterVM; realized the privacy protection of cross-chain asset flow.
In other words, Suterusu’s trilogy is:
The landing of ZK-ConSNARK technology;
Launched Suter Protocol and Suter Shield based on ZK-ConSNARK. Support DeFi privacy protection on different public chains, and currently complete deployment on Ethereum and BSC;
The cross-chain asset privacy protection protocol facilitates the flow of anonymous assets between different chains.
ZK-ConSNARK: The foundation of Suterusu privacy layer
In blockchain privacy, size must be considered. The performance of the blockchain is difficult to improve because its throughput is related to the block space and transaction size. Therefore, the size of the SNARK is very important, which will have an important impact on scalability. For example, Monero's zero-knowledge proof occupies a large space, so it is not conducive to its scalability. Zcash has a constant SNARK, and the space for proof is small, but it has the problem of credible presupposition.
The ZK-ConSNARK mechanism is to combine the advantages of the two, the SNARK size will not be too large, which is conducive to expansion; there is no problem of credible presets. ZK-ConSNARK is a constant zero-knowledge proof mechanism that does not require credible initialization, which is beneficial to both efficiency and safety. That is to say, in the current SNARK mechanism, some mechanisms can achieve constant proof size, which is more efficient, but there are potential problems in security (for example, trusted initialization is required); while some mechanisms do not require trusted initialization, and are safe Higher, but it has a logarithmic scale to prove that the efficiency is lower. However, ZK-ConSNARK takes into account both, and can realize constant-level zero-knowledge proof without credible initialization, thus laying the foundation for the implementation of privacy technology.
According to Suterusu, Suterusu plans to integrate new research results in cryptography in the implementation of the project: a new range proof scheme that does not require trusted initialization. The paper of this program was completed by Suterusu’s CTO Lin Huang in cooperation with cryptographers from the French National Academy of Sciences and Karlsruhe Institute of Technology, and has been accepted by the top cryptography conference Eurocrypt 2021.
This paper aims to propose a new scheme for constructing range proofs. Its core breakthrough is to convert any promise scheme on a finite field into a general scheme of bounded integer promise schemes, which can be used to prove the satisfying relationship between bounded integers. , Changed the original situation that required trusted initialization and consumed a lot of communication and computing resources. Based on the discrete logarithm hypothesis, the range proved to be small and efficient. According to Suterusu's official website, under the same parameter selection, its proof space is about 12% to 20% less than the Bulletproof scheme, and it has more than ten times improvement in proof generation and verification compared with similar schemes.